Securing REST APIs | The Role of OAuth 2.0 in Authorization
REST APIs are becoming increasingly critical for modern applications. However, OAuth 2.0 emerges as a powerful framework for securing REST APIs by delegating user authorization. This article will therefore showcase how you can use OAuth 2.0 to secure your REST APIs!
REST APIs have become an indispensable component, facilitating communication between disparate systems and enabling the creation of dynamic web experiences. However, safeguarding these APIs against unauthorized access necessitates the implementation of robust security measures. OAuth 2.0 emerges as a powerful framework in this context, offering a standardized approach to securing REST APIs by delegating user authorization.
To learn about the other types of authentication you can set with Apidog, click the button below!

Using the OAuth 2.0 authentication approach eliminates the need for client applications to directly manage user credentials, thereby enhancing both security and user privacy. This article delves into the intricacies of OAuth 2.0 and its role in safeguarding REST APIs.
What is OAuth 2.0 Authentication?
OAuth 2.0 is an authorization framework that enables applications to obtain limited access to user accounts on an HTTP service, by delegating the user authentication process to the service that holds the user accounts and access tokens. This ensures secure authorization without exposing sensitive credentials.

Parties Involved with OAuth 2.0
Resource Owner (User): The individual who owns the account data being accessed.
Client Application: The application requesting access to the user's account data.
Authorization Server: The server responsible for authenticating the user and issuing access tokens. This is typically the service that holds the user accounts (e.g., Google, Facebook).
Resource Server: The server that holds the protected resources (e.g., user data) that the client application wants to access. This can be the same server as the Authorization Server or a separate one.
Benefits of Implementing OAuth 2.0 Authentication
OAuth 2.0 stands as a dominant force in the world of authorization, offering a secure and user-centric approach for applications to access user data on external services. Here's a breakdown of the key benefits it brings to the table:
Enhanced Security
Eliminates Password Storage: Applications no longer need to store user passwords, a prime target for attackers. OAuth 2.0 utilizes access tokens, and short-lived credentials that minimize damage if compromised.
Reduced Attack Surface: By delegating user authentication to the authorization server, the application itself doesn't handle sensitive login information. This reduces the attack surface for potential security vulnerabilities.
Granular Access Control: Scopes define the specific resources and actions an application can access within a user's account. Users can grant consent for specific scopes, offering granular control over their data.
Improved User Privacy
Transparency and Control: Users are explicitly informed about the data an application is requesting access to through scopes. This transparency allows them to make informed decisions about sharing their data.
Revocation of Access: Users can revoke access tokens at any time, effectively removing an application's access to their data. This empowers users to maintain control over their privacy.
Reduced Reliance on Third-Party Apps: OAuth 2.0 allows users to leverage existing accounts like Google or Facebook to log in to new applications. This eliminates the need to create new accounts and potentially share unnecessary data.
Streamlined User Experience
Single Sign-On (SSO): Users can authenticate with a single service (e.g., Google) and access multiple applications that utilize OAuth 2.0. This creates a seamless and convenient login experience.
Simplified Application Development: Standardized protocols of OAuth 2.0 make it easier for developers to integrate secure authorization mechanisms into their applications.
Platform Independence: OAuth 2.0 is a widely adopted framework, allowing applications to leverage authorization across different platforms and services.
Additional Advantages
Scalability: OAuth 2.0 caters to diverse applications, from web browsers to mobile apps, with different authorization flows addressing their specific needs.
Flexibility: The framework can be customized to accommodate various security requirements and user experiences.
Reduced Server Load: By delegating authentication to the authorization server, the application server experiences reduced load and processing demands.
In conclusion, OAuth 2.0 offers a comprehensive approach to authorization, prioritizing security, user privacy, and a smooth user experience. Its secure token-based system and granular access control make it the preferred choice for modern applications interacting with user data.
Using Apidog to Create REST APIs with OAuth 2.0 Authentication
As REST APIs are dominating the API market, let's learn how to use Apidog to build a REST API, and implement the OAuth 2.0 authentication type to bolster our REST API's security!
Build REST APIs With Apidog
Apidog equips users with all the necessary tools needed to create a REST API from scratch! All you have to prepare is the knowledge of REST APIs and the certain structure that REST APIs need to adhere to.
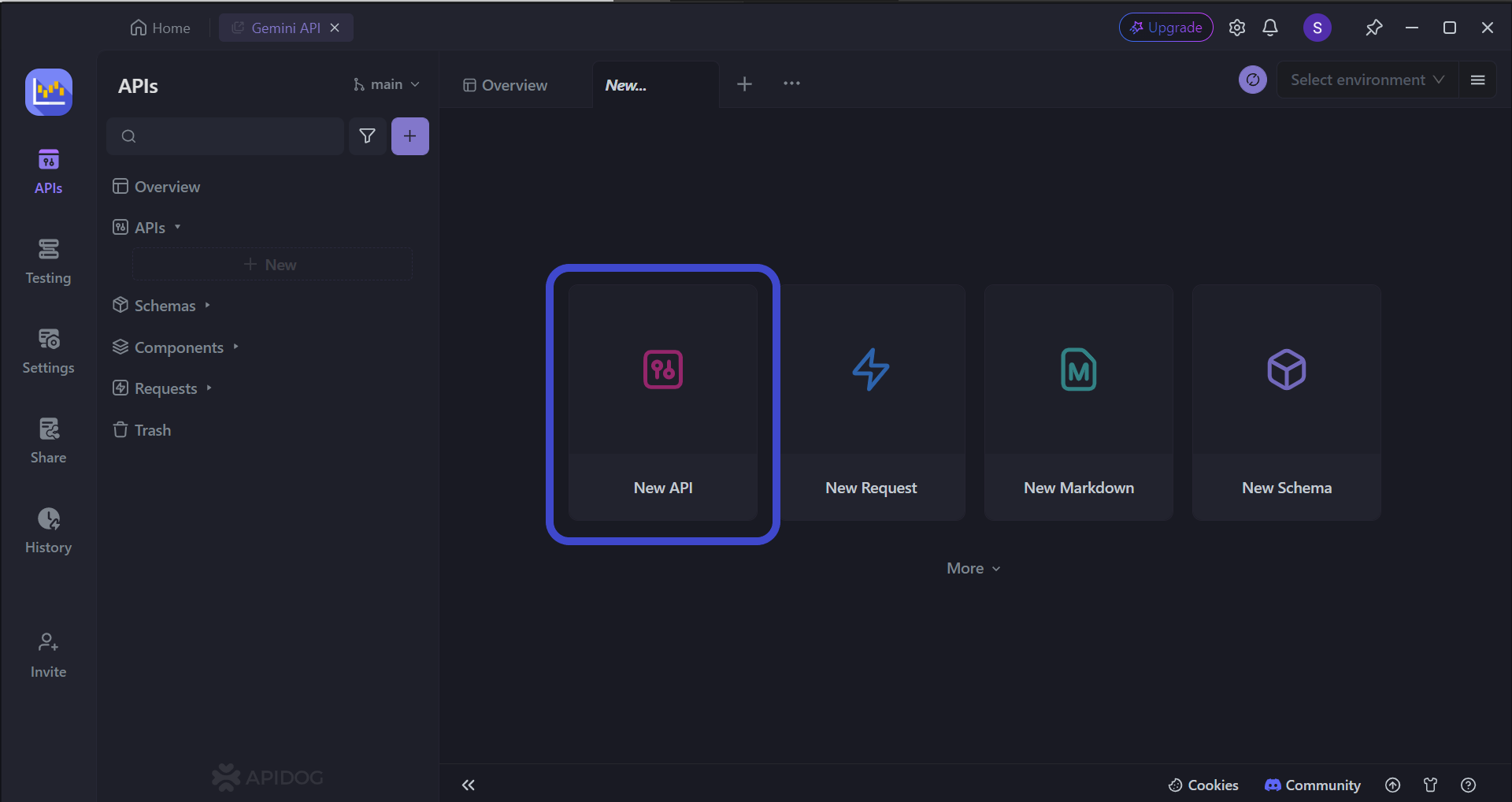
To begin, press the New API button, as shown in the image above.
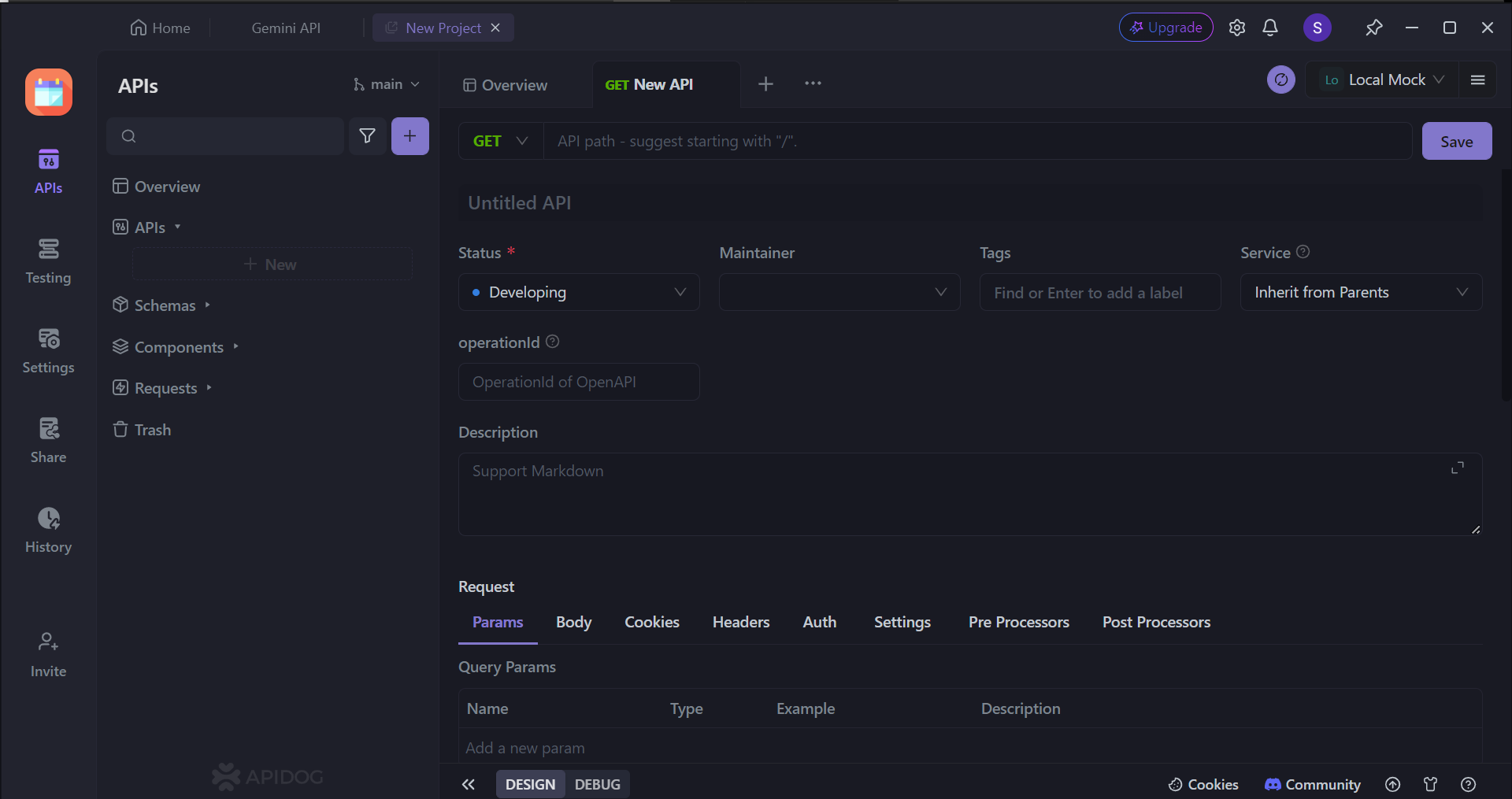
This section empowers you to outline your API's functionalities fully. You can detail:
- Actions (GET, POST, PUT, DELETE): How applications will interact with your API (retrieving, creating, updating, or deleting data).
- Access Points (URLs): The specific locations (endpoints) where applications will send requests.
- Data Specificity (Parameters): Any details required within the URL to target specific data.
- Functionality Explained: A clear description of what each endpoint accomplishes.
By defining these elements, you lay the groundwork for your REST API. With this foundation in place, you can move on to securing your REST API and exploring best practices for crafting effective REST API URLs.


Selecting OAuth 2.0 Authentication with Apidog
With Apidog's simple and intuitive user interface, you can easily choose OAuth 2.0 - or any other authentication type - in just a matter of seconds!
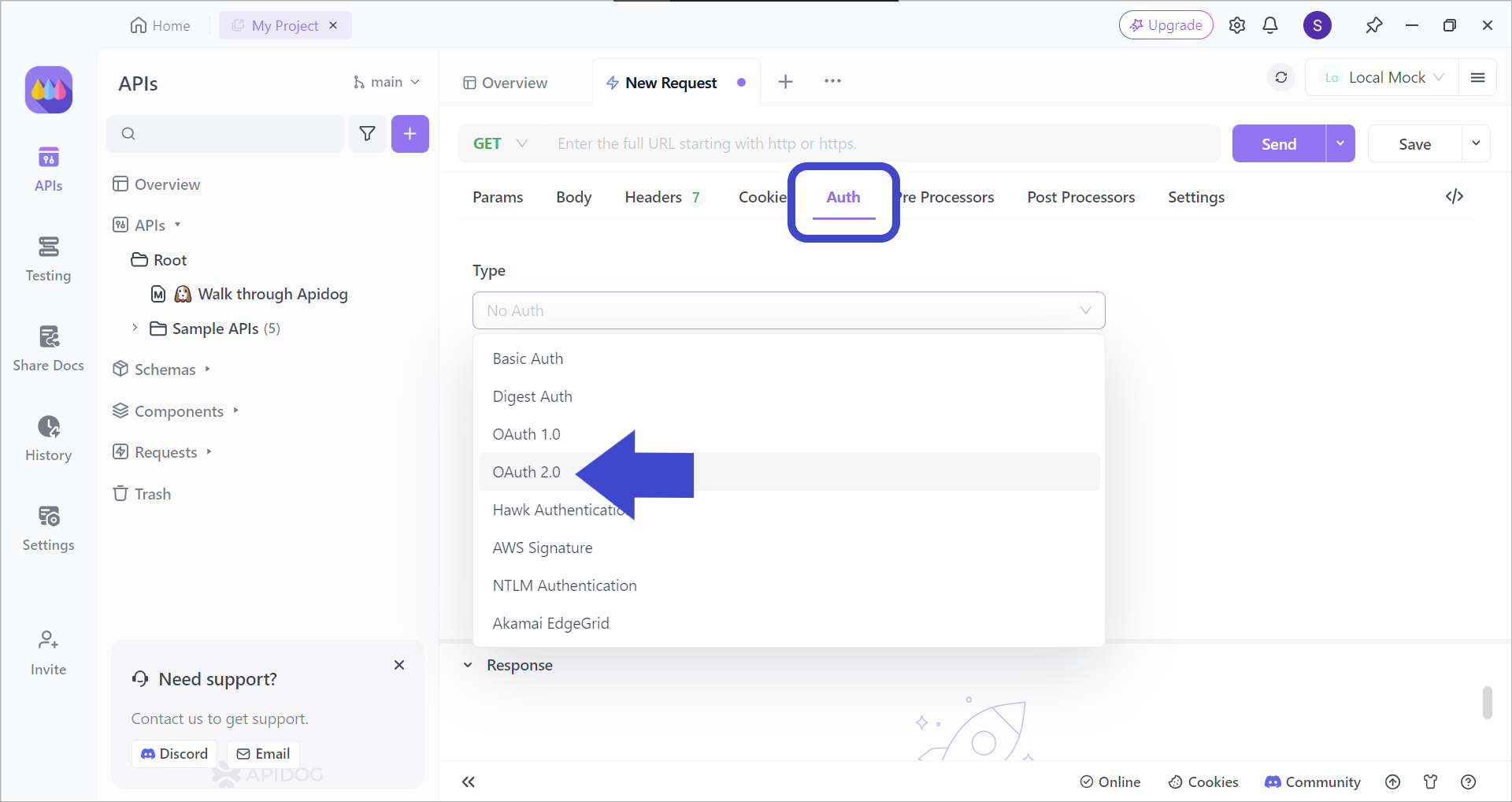
Firstly, locate the Auth header in order to change the authentication type to OAuth 2.0, as shown in the image above.
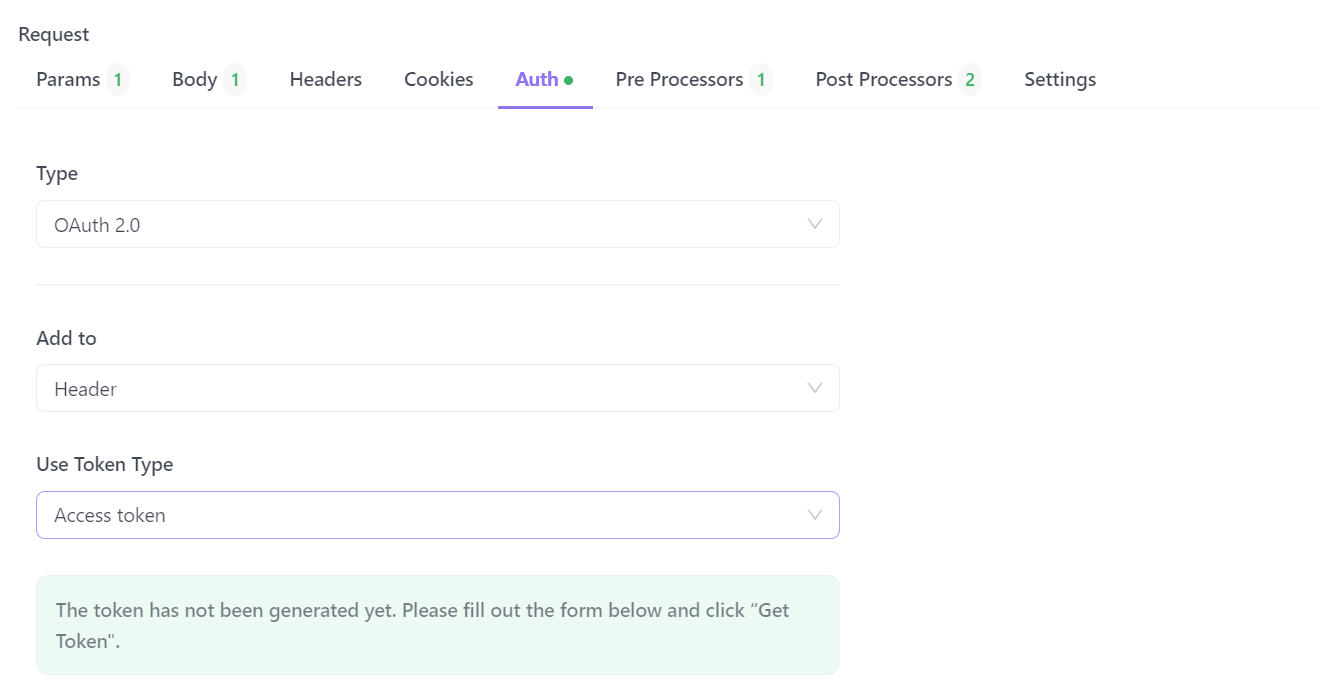
Once you have selected OAuth 2.0, you can add the necessary details for the OAuth 2.0 authentication.
Conclusion
OAuth 2.0 stands as a cornerstone of securing REST APIs in today's interconnected world. By delegating user authentication and leveraging access tokens with granular scopes, it fosters a robust authorization model. This approach safeguards sensitive user data, empowers users with control over their privacy, and streamlines the application development process.
As REST APIs continue to propel innovation, a comprehensive understanding of OAuth 2.0 empowers developers to design secure and user-centric authorization mechanisms, ensuring the continued success of modern web applications.






