API Gateway Authentication (Apidog Tutorial)
API Gateway Authentication refers to the process of verifying the identity of users or applications that are trying to access an API through an API gateway.
APIs (Application Programming Interfaces) and API gateways are fundamental in connecting different computer programs. The significance of API gateways and robust authentication mechanisms cannot be overstated in the ever-evolving landscape of software development and digital interactions. In this article, we will explore how APIs and API gateways have evolved and the essential role that authentication plays within API gateways.
What is API Gateway Authentication?
API Gateway Authentication refers to the process of verifying the identity of users or applications that are trying to access an API (Application Programming Interface) through an API gateway. An API gateway acts as a central entry point for multiple APIs, providing a unified interface for clients to interact with various services. Authentication is a crucial aspect of API security, ensuring that only authorized users or applications can access the API's resources and data.
The Evolution of APIs and API Gateways
In the earlier days of computing, programs were isolated islands, unable to communicate with each other. APIs emerged as bridges that allowed these programs to share information and collaborate. Over time, as the need for efficient communication grew, API gateways were developed. These gateways acted as central hubs, managing program interactions and making communication more efficient.
Importance of Authentication in API Gateways
Consider a locked door that only opens with a specific key. Authentication is like that key for computer programs. It ensures that only authorized programs can access valuable data and services. Without proper authentication, unauthorized programs or users can access your software and potentially cause harm. Thus, authentication acts as a security guard, ensuring only trusted programs can enter the system.
We will explore the fantastic world of Apidog API Gateway Authentication as we move ahead. We will learn how to keep our apps safe, ensure only the right ones can enter the clubhouse, and avoid any digital troublemakers. But let us first talk about what Apidog actually is.
A Brief Overview of Apidog
Apidog is a comprehensive suite of tools that empowers software development teams throughout the API lifecycle. It is designed to facilitate the best practices of API Design-first development. Apidog emerges as a robust platform that simplifies API management and security complexities. Whether you are a seasoned developer or just starting your API journey, Apidog offers a user-friendly interface and a range of functionalities to cater to your unique requirements.

This gateway acts as an intermediary layer that sits between client applications and backend services, seamlessly orchestrating API requests, handling security protocols, and optimizing performance. Apidog empowers organizations to deliver consistent and reliable API experiences while maintaining high security and control.
Key Features and Benefits
Apidog API Gateway offers a range of critical features that make it a compelling choice for developers, organizations, and businesses:
Versatile Authentication Options:
Apidog supports various authentication methods, from basic username-password authentication to more advanced approaches like Bearer tokens, OAuth, and JWT. This flexibility lets developers choose the authentication mechanism that best suits their application's security needs.
User-Friendly Interface:
Apidog boasts an intuitive and user-friendly interface that caters to developers of all skill levels. The platform's straightforward design simplifies the process of configuring, managing, and monitoring APIs, eliminating the need for complex technical know-how.
Authentication and Authorization Management:
With Apidog, implementing and managing authentication and authorization methods becomes effortless. Developers can easily set up user accounts, define access permissions, and monitor the performance of these security measures.
Scalability:
As applications grow, so does the demand for scalable API solutions. Apidog is designed to scale alongside your application, ensuring your APIs remain performant and secure even as your user base expands.
Secure Data Transmission:
Ensure that data transmitted between client applications and your API remains secure. HTTPS encryption protects sensitive information from leaking and users gaining unauthorized access during transmission.
Fine-Grained Access Control:
Apidog empowers developers to establish granular access controls, assigning specific permissions to different users or clients. This precision ensures that API resources are accessible only to those with the appropriate authorization.
Integration Support:
Apidog is designed to integrate seamlessly with existing development and deployment workflows. With support for popular tools and platforms, Apidog ensures a smooth and efficient API security implementation process. This integration support simplifies the transition to Apidog and minimizes disruptions to existing development practices.
Deep Dive into Apidog Authentication
Apidog, a powerful API gateway, provides various authentication methods to meet diverse security requirements. Here are some authentication methods offered by Apidog.
Configuration and Setup of Authentication
Configuring authentication within Apidog is an uncomplicated process that empowers developers to fortify their APIs without compromising user experience. Apidog 's user-friendly interface guides users through the authentication setup, enabling them to select the most fitting authentication method for their specific application.
Apidog provides authentication solutions that seamlessly integrate with existing infrastructures, whether it is safeguarding a web application, mobile app, or backend services. Each method is designed to cater to specific security needs, allowing you to choose the authentication approach that aligns perfectly with your application's requirements.
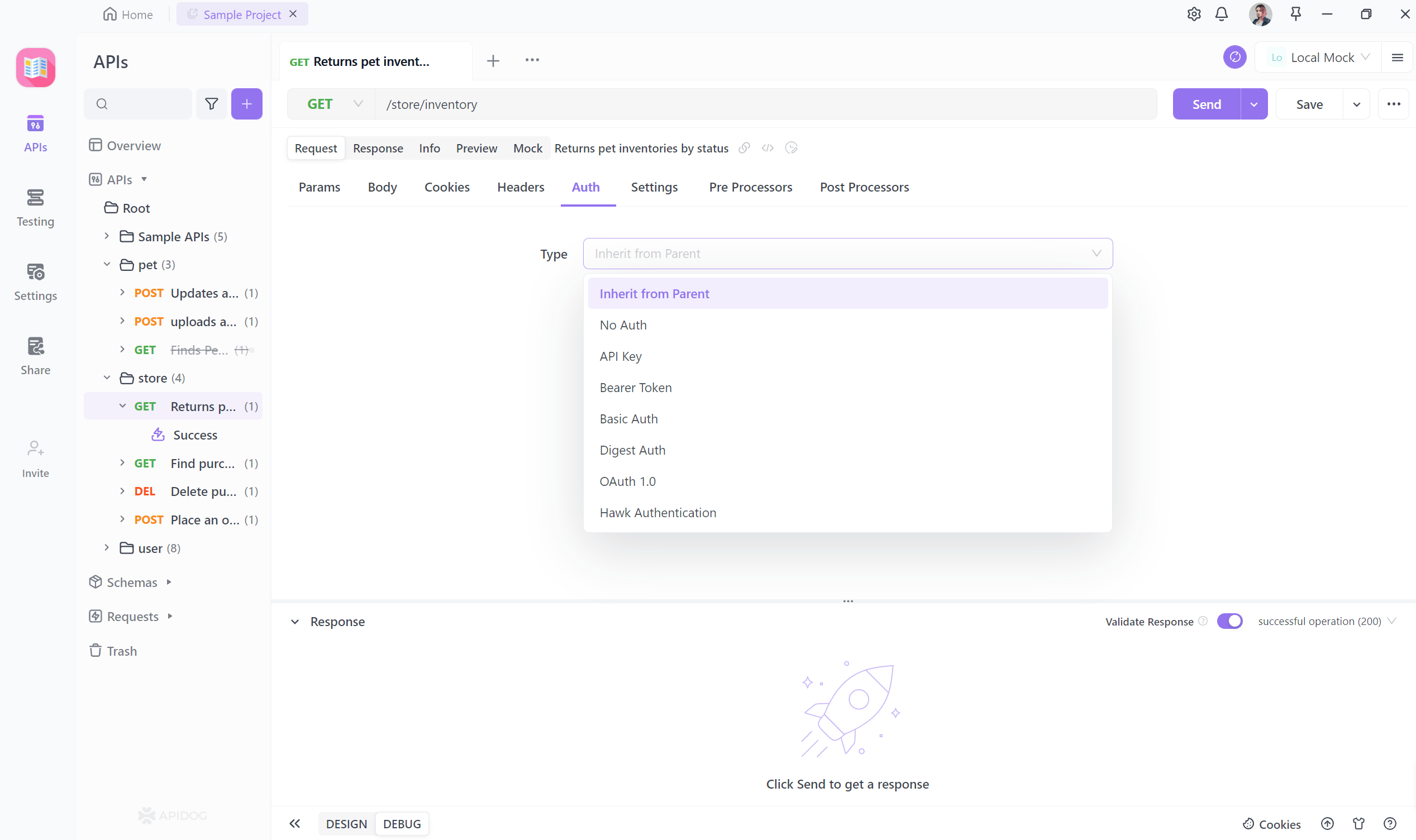
Inherit from Parent
A notable feature within Apidog is the ability to inherit authentication settings from a parent API. This approach streamlines the configuration process, ensuring uniform security protocols across various endpoints or versions of an API. By inheriting authentication settings, developers can uphold consistent security practices while minimizing the intricacies of configuration management.

No Auth
Apidog presents the "No Auth" option when authentication is unnecessary. This option grants public access to designated APIs without mandating any authentication credentials. While suitable for open data APIs or specific public resources, careful consideration is advised to address potential security implications adequately.
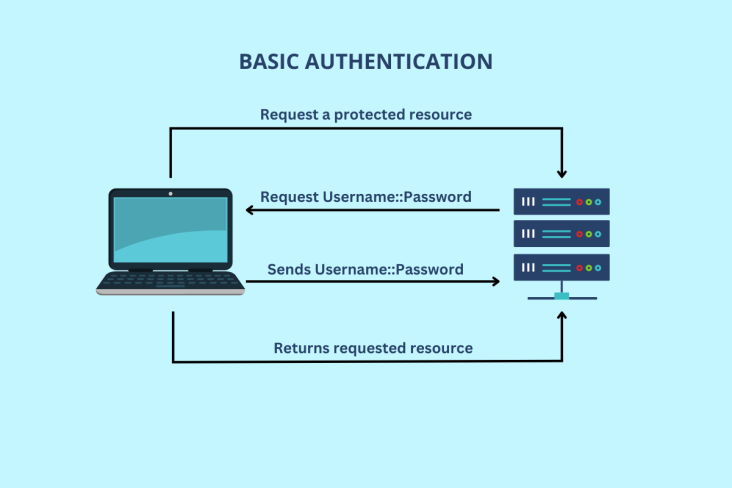
Basic Auth
Basic Authentication, a classic authentication method, entails transmitting a username and password combination in the request header. While it is straightforward to implement, coupling Basic Authentication with HTTPS encryption is crucial to ensure the confidentiality of credentials during transmission.
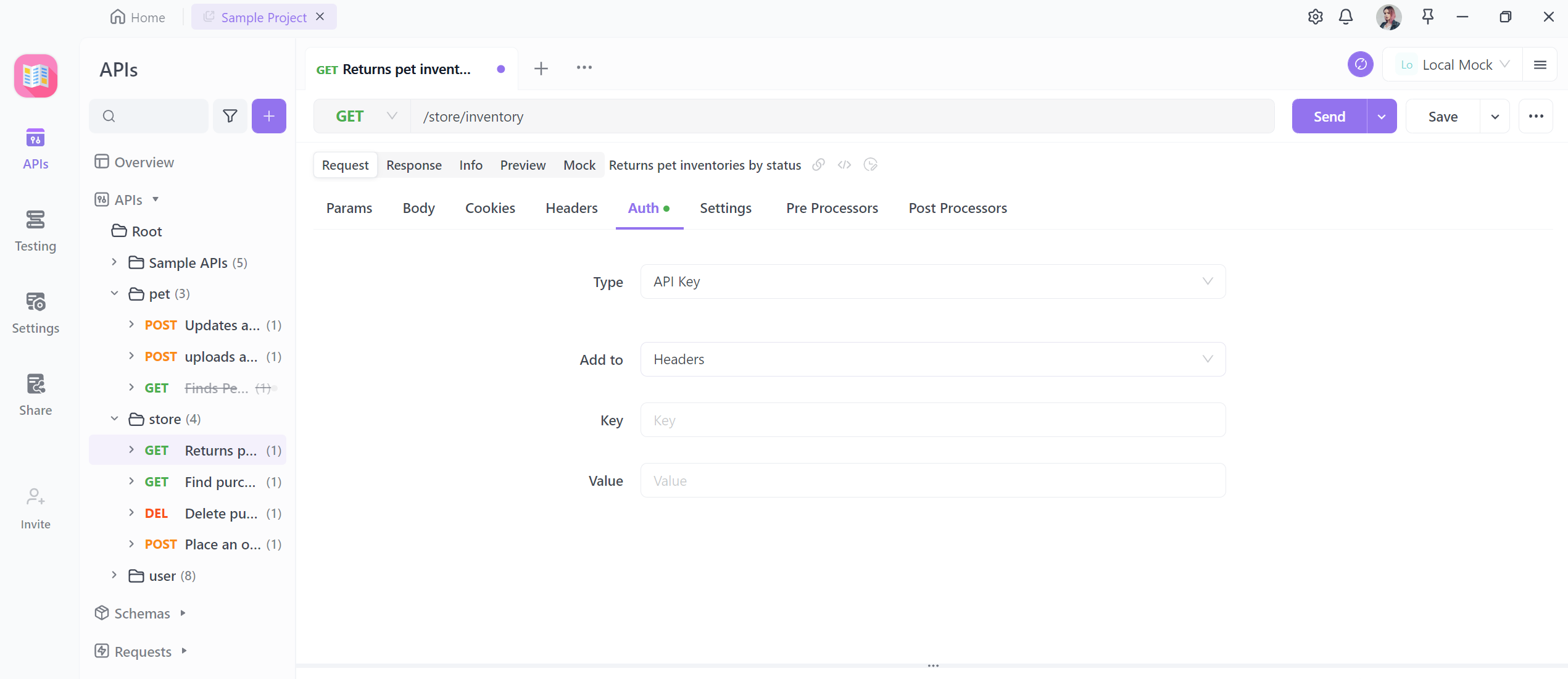
API Key
API keys offer a straightforward yet effective means of authentication. Apidog 's API key authentication empowers developers to generate distinct keys linked to specific APIs or endpoints. These keys serve as digital credentials, permitting authorized users to access resources while simultaneously preventing unauthorized access.
Bearer Token
Bearer tokens are prevalent in contemporary application authentication. Apidog seamlessly supports the "Bearer Token" method, enabling users to include a token within the request header to gain access to secured resources. This approach proves particularly beneficial for ensuring the security of mobile apps, web applications, and APIs necessitating frequent interactions.
Digest Auth
Digest Authentication enhances security by transmitting a hashed representation of the password rather than the password itself. This mitigates the risk of password exposure during transmission. Apidog 's support for Digest Authentication bolsters protection for sensitive data and resources.
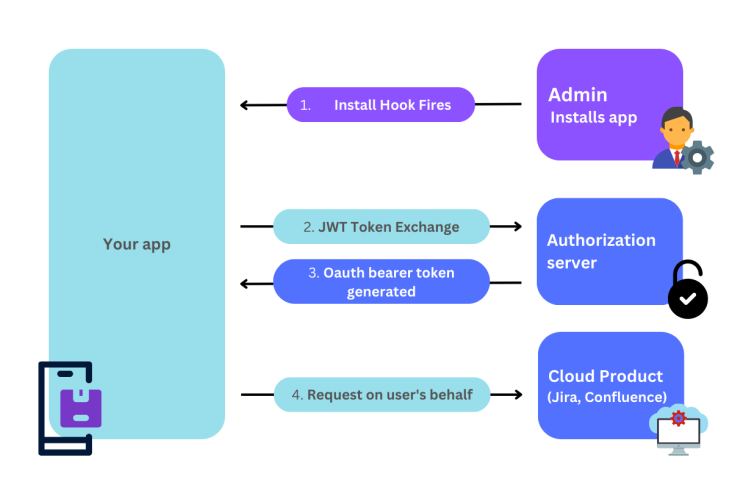
OAuth 1.0
OAuth 1.0 is a robust protocol facilitating secure authorization for third-party applications. It involves the exchange of access tokens and secret keys, granting fine-grained access control. Apidog 's implementation of OAuth 1.0 simplifies third-party app integration while maintaining stringent security measures.
Hawk Authentication
Hawk Authentication is a cryptographic protocol that furnishes message-level authentication for APIs. It ensures the integrity and authenticity of requests, thwarting tampering and unauthorized access. Apidog 's support for Hawk Authentication ensures data integrity throughout API interactions.
AWS Signature
For applications integrated with Amazon Web Services (AWS), Apidog provides AWS Signature authentication. This approach entails signing requests with AWS credentials, enabling secure communication between applications and AWS services.
NTLM Authentication
NTLM (New Technology LAN Manager) Authentication is a Windows-based protocol ensuring secure communication between clients and servers within a Windows domain. Apidog s NTLM support facilitates seamless integration within Windows environments.
Akamai Edgegrid
Apidog's Akamai Edgegrid authentication facilitates integration with Akamai's content delivery network. It ensures secure communication between applications and Akamai services, enhancing performance while upholding robust security protocols.
Role-Based Access Control:
Role-based access control (RBAC) is a pivotal facet of authentication, empowering administrators to manage user permissions efficiently. Apidog enables developers to assign specific user roles, granting access to designated resources and actions based on predefined roles. This level of granular control enhances security by ensuring that users possess access only to the functionalities aligned with their roles.
Apidog 's authentication options offer an extensive toolkit for fortifying APIs. From traditional methods such as API keys and Basic Authentication to advanced protocols like OAuth and Hawk Authentication, APIDOG equips developers with the flexibility to tailor authentication to the distinct security requisites of their applications.
Conclusion
Authentication isn't just a tech thing; it is the guardian of your data, user privacy, and application integrity. So, as you forge ahead in your coding endeavors, remember authentication – the shield that keeps your digital realm safe and sound.




