Authorization plays a pivotal role in regulating access and safeguarding sensitive data. Among the various authorization mechanisms, bearer tokens have emerged as a prevalent approach due to their simplicity and versatility. When employed with cURL, a popular command-line tool for transferring data, bearer tokens offer a streamlined method for incorporating authorization into API requests.
Quickly get started with APidog to build, test, mock, and document APIs within a single application - no more alt-tabbing to different windows for the sake of app development!
To learn more about Apidog, make sure to click the button below.

This article delves into the intricacies of cURL bearer tokens, elucidating their core concepts, implementation strategies, and potential benefits. By equipping readers with a comprehensive understanding of this authorization technique, we empower them to leverage cURL's capabilities for seamless and secure API interactions.
To fully grasp the topic of this article, we will first discuss what cURL and bearer tokens are individually.
What is cURL?
cURL, short for "client URL," is a free and open-source software project that provides two powerful tools for interacting with the web:
cURL Command-line Tool
This is the workhorse of cURL and allows users to transfer data using various network protocols directly from a terminal window. Think of it as giving instructions to your computer on how to communicate with a specific location on the internet.
Libcurl Development Library
This underlying library forms the core functionality of cURL. It acts as a set of building blocks that programmers can integrate into their applications for programmatic data transfer.
The beauty of cURL lies in its versatility. It supports a wide range of protocols, including the most commonly used ones like:
HTTP (Hypertext Transfer Protocol)
The foundation of web communication that is used for accessing websites and transferring data.
HTTPS (Secure HTTP)
The encrypted version of HTTP ensures secure communication with websites.
FTP (File Transfer Protocol)
Used for uploading and downloading files between computers.
SFTP (Secure File Transfer Protocol)
Encrypted version of FTP for secure file transfers.
Key Features of the cURL Command-Line Tool
Simple and User-Friendly
Commands are easy to learn and follow, even for beginners.
Flexibility
Offers a vast array of options for customizing data transfers, like specifying headers, setting timeouts, and handling authentication.
Cross-Platform Compatibility
Runs seamlessly on various operating systems like Windows, macOS, and Linux.
Scriptable
Can be integrated into scripts for automating repetitive data transfer tasks.
Common Uses of cURL
While downloading files and testing APIs are popular uses of cURL, its capabilities extend far beyond these basic functions. Here's a closer look at some of the advanced applications of cURL:
Advanced Download Management
- Resuming Interrupted Downloads: cURL allows you to resume downloads that were interrupted due to network issues or power outages. This saves time and bandwidth by picking up where you left off.
- Limiting Download Speed: Concerned about overwhelming your internet connection? cURL lets you specify a download speed limit, ensuring smooth browsing while downloading large files.
- Multitasking Downloads: Download multiple files simultaneously with cURL, optimizing your download time by utilizing your internet connection's full potential.
Communication and Authentication
- HTTPS Support: cURL seamlessly handles secure connections with websites using HTTPS, ensuring the confidentiality and integrity of data transferred.
- Basic and Digest Authentication: Need to access password-protected resources? cURL allows you to provide credentials for basic and digest authentication methods, granting access to authorized users.
- Client Certificates: cURL supports the use of client certificates for advanced two-factor authentication, adding an extra layer of security for accessing sensitive resources.
Web Scraping (with Caution)
- Extracting Specific Data: cURL can be used to extract data from websites in a structured format, useful for tasks like price comparisons or market research. However, it's crucial to adhere to website terms of service and avoid overwhelming servers with excessive requests.
- Data Aggregation: Combine data from multiple sources by sending cURL requests to various websites and aggregating the extracted information into a single dataset.
- Web Monitoring: Schedule cURL commands to periodically check website content for changes, allowing you to track updates or monitor product availability.
Scripting and Automation
- Automating Repetitive Tasks: Streamline repetitive data transfer tasks by integrating cURL commands into scripts. This saves time and effort, ensuring consistent execution.
- Error Handling and Logging: Build scripts with cURL that handle potential errors gracefully, log actions, and provide feedback for troubleshooting purposes.
- Integration with Other Tools: cURL can be combined with other command-line tools or programming languages to create powerful automation solutions for complex data workflows.
Debugging and Troubleshooting
- Simulating HTTP Requests: cURL allows you to replicate specific HTTP requests for testing purposes, making it a valuable tool for developers to identify and resolve issues with web applications.
- Verifying Server Responses: Analyze server responses returned by cURL, including headers and error codes, to pinpoint communication problems on the server side.
- Debugging Network Issues: Isolate network-related problems by using cURL to test connectivity and data transfer capabilities to specific servers.
What are Bearer Tokens?
Bearer tokens are essentially opaque strings of characters, typically alphanumeric or a combination of letters and numbers. It doesn't contain any human-readable information but serves as a unique identifier for an authorized user or application. The server that issues the token is responsible for associating it with specific access rights and permissions.
Typical Workflow of How Bearer Tokens Work
Step 1 - Authentication
The user or application first goes through an authentication process, often using mechanisms like username/password combinations or OAuth [OAuth]. This process verifies the user's identity and determines the level of access they should have.
Step 2 - Token Issuance
Upon successful authentication, the server generates a bearer token. This token encapsulates the user's identity and granted permissions.
Step 3 - Authorization with cURL
When the user or application needs to access a protected resource using cURL, they include the bearer token in the request header. The header typically follows the format "Authorization: Bearer <token>".
Step 4 - Server-Side Validation
The server receiving the cURL request intercepts the authorization header and extracts the bearer token. It then validates the token's authenticity and verifies the user's permissions associated with the token.
Step 5 - Granting Access
If the token is valid, the server grants access to the requested resource based on the permissions encoded within the token. If the token is invalid or expired, access is denied.
Code Examples of cURL with Bearer Tokens
Example 1 - cURL POST Request with Bearer Token
This example demonstrates sending data to a protected resource using a POST request.
# API endpoint for creating a new user
API_URL="https://api.example.com/users"
# Bearer token for authorized user
BEARER_TOKEN="your_bearer_token_here"
# User data in JSON format (replace with your actual data)
USER_DATA='{"name": "John Doe", "email": "john.doe@example.com"}'
curl -X POST \
-H "Authorization: Bearer ${BEARER_TOKEN}" \
-H "Content-Type: application/json" \
-d "${USER_DATA}" \
${API_URL}
Code explanation:
- This script uses the
-X POSTflag to specify a POST request. - An additional header
Content-Type: application/jsonis included to indicate the format of the data being sent (JSON in this case). - The
-dflag is used to specify the data to be sent in the request body. Here, we use a variableUSER_DATAcontaining the user information in JSON format.
Example 2 - cURL with Bearer Token and Query Parameters
This example showcases including query parameters in the URL along with a bearer token.
# API endpoint for fetching users (replace with your actual endpoint)
API_URL="https://api.example.com/users?limit=10&offset=20"
# Bearer token for authorized user
BEARER_TOKEN="your_bearer_token_here"
curl -X GET \
-H "Authorization: Bearer ${BEARER_TOKEN}" \
${API_URL}
Code explanation:
This script uses a GET request with query parameters appended to the URL. These parameters (limit and offset) can be used to control the number of results returned and the starting point for data retrieval.
Apidog - Implement cURL Codes into Readable Requests
Apidog is a powerful, comprehensive API development tool that provides developers with complete tools for the entire API lifecycle. With Apidog, you can build, test, mock, and document APIs within a single application!

Import and Edit cURL APIs with Apidog
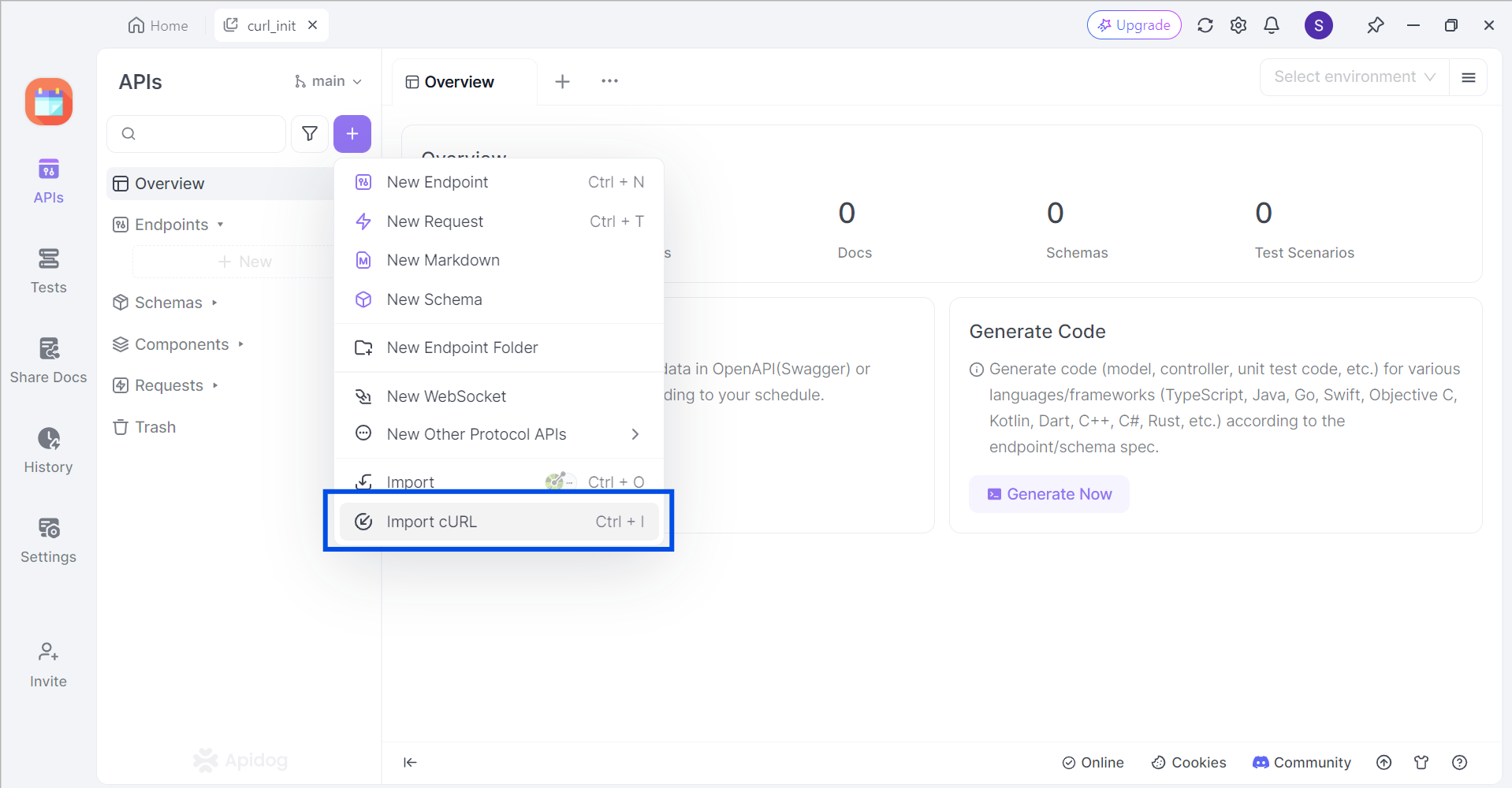
Apidog supports users who wish to import cURL commands to Apidog. In an empty project, click the purple + button around the top left portion of the Apidog window, and select Import cURL.
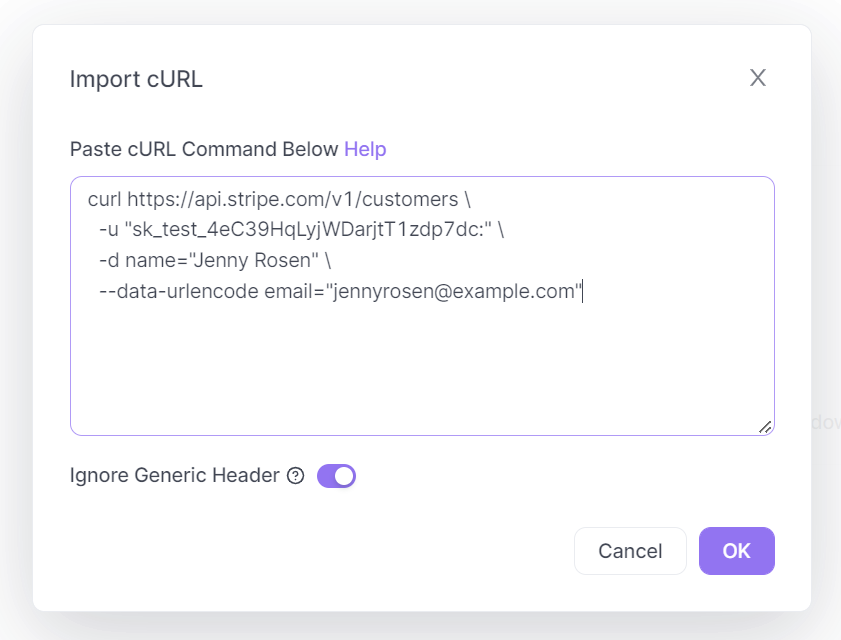
Copy and paste the cURL command into the box displayed on your screen.
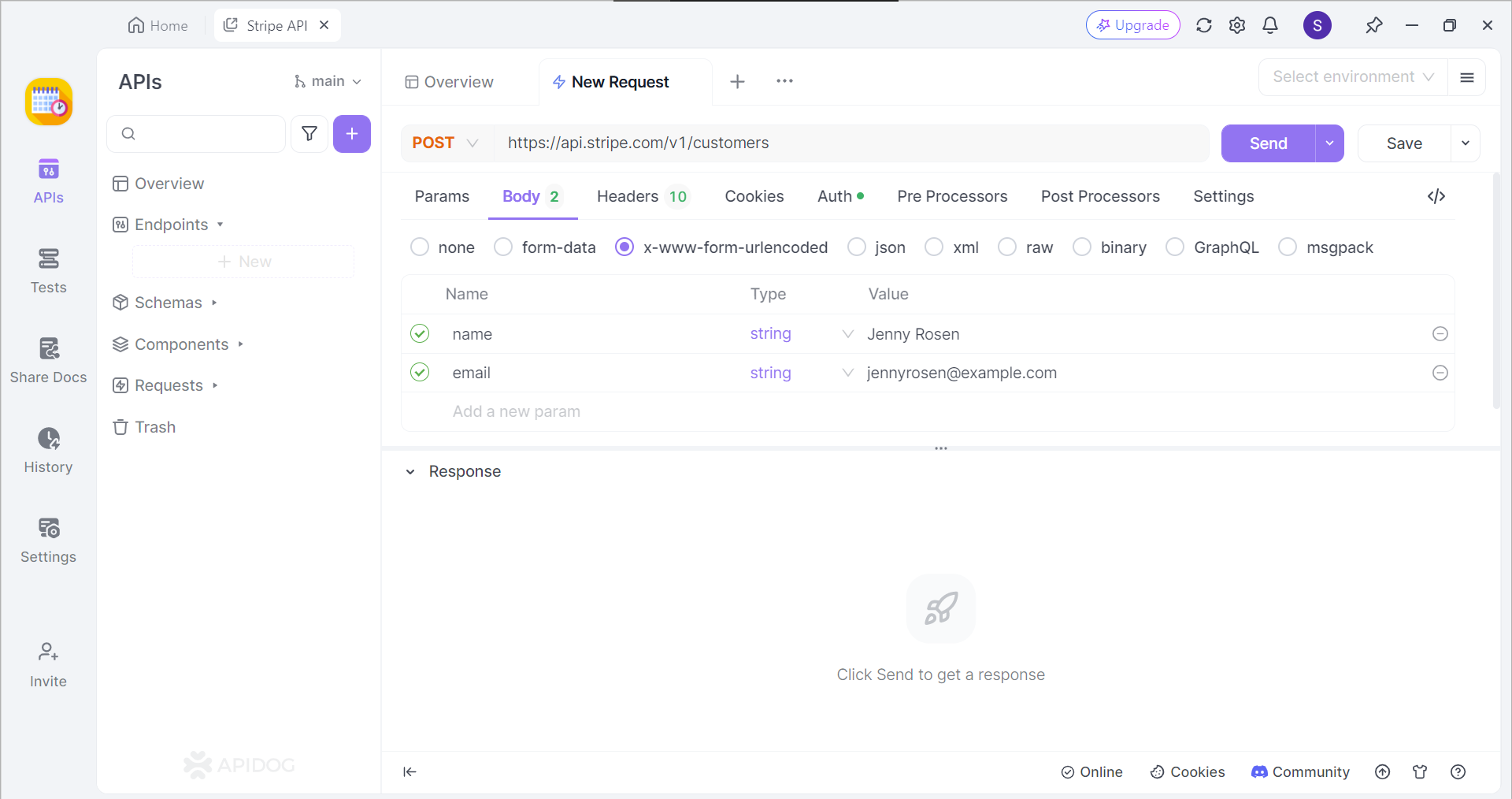
If successful, you should now be able to view the cURL command in the form of an API request.
Secure Your APIs with API Keys

Apidog provides developers with the option of securing their APIs with API keys. This is a similar concept to bearer tokens, where clients will have their unique key and value pairing to ensure that they are authentic and authorized users of the API.
Conclusion
cURL, with its versatility and ease of use, coupled with the simplicity and stateless nature of bearer tokens, forms a powerful combination for interacting with web APIs. By incorporating bearer tokens into cURL requests, developers and users can streamline API access, ensuring secure and controlled data exchange.
However, it's crucial to remember the inherent risks associated with bearer tokens, such as interception and theft. Always prioritize secure communication protocols (HTTPS) and proper token storage practices to safeguard your data and maintain the integrity of your API interactions. By understanding the strengths and limitations of this approach, you can leverage cURL bearer tokens effectively for seamless and secure API communication.
![[Guide] What is a cURL Bearer Token?](https://assets.apidog.com/blog-next/2026/02/curl-bearer-token.png)