We've all dealt with the chaos of managing API keys, tokens, and different server URLs. You know how it goes: everything runs smoothly on your local machine because you've hardcoded the dev API key and the localhost URL. Life is good… until you switch to the staging environment.
Suddenly, you're editing every request one by one—changing the base URL, updating the API key, fixing Authorization headers. It's slow, it's frustrating, and it's an easy way to introduce mistakes.
And sharing your API collection? That's another headache. You send it to a teammate and then follow up with a secret Slack message saying, "Replace all the keys with your own." Now your sensitive API keys are scattered across random chats, and your security risk just skyrocketed.
This isn't just annoying—it's a broken workflow.
The good news? All of this is completely avoidable. One simple shift separates an amateur workflow from a professional one: mastering environments and secrets management. And the best part is, you don't need a pile of tools to get it right.
So, let's dive in and see how the right API client does more than just send requests — it helps you manage your entire API ecosystem with clarity, security, and confidence.
Why Environment and Secrets Management is Your #1 Productivity Boost
Before we get into the "how," let’s get clear on the "why." You might think, "It's just a few manual changes—what’s the big deal?" But the hidden cost of not managing environments properly is enormous.
- The "It Works on My Machine" Nightmare: This classic issue almost always comes from inconsistent environment settings. Your local setup uses one set of variables, staging uses another, and production is a completely different world. Without a clean way to manage them, bugs and misconfigurations are guaranteed.
- The Security Red Alert: Hardcoding API keys, tokens, or client secrets into your requests is a huge security hazard. If you share that collection, you’re also sharing your credentials. One leaked file or DM could compromise an entire service.
- The Productivity Killer: Manually updating URLs, keys, and tokens across dozens or hundreds of requests is a soul-crushing task. It steals time that could be spent on actual development, testing, and innovation.
- The Onboarding Bottleneck: When a new developer joins your team, how long does it take them to get their API environment set up? If the answer involves a cryptic README file and a treasure hunt for credentials, your process is broken.
A proper environment and secrets management system isn't a luxury; it's the foundation of a secure, collaborative, and high-quality API workflow.
Meet Your New Environment Command Center: Apidog
Apidog is a comprehensive API development platform that transforms how teams manage environments and secure sensitive credentials throughout the API lifecycle. Built for modern development workflows, Apidog eliminates the chaos of hardcoded values, scattered API keys, and manual configuration updates that plague traditional API testing approaches.
- Apidog's environment management feature provides a centralized command center for managing different configurations across development, staging, and production environments.
- Apidog's vault secrets feature — enterprise-grade integration with external vault providers — keeps your most sensitive credentials even more secure.
Managing Environments and Variables in Apidog
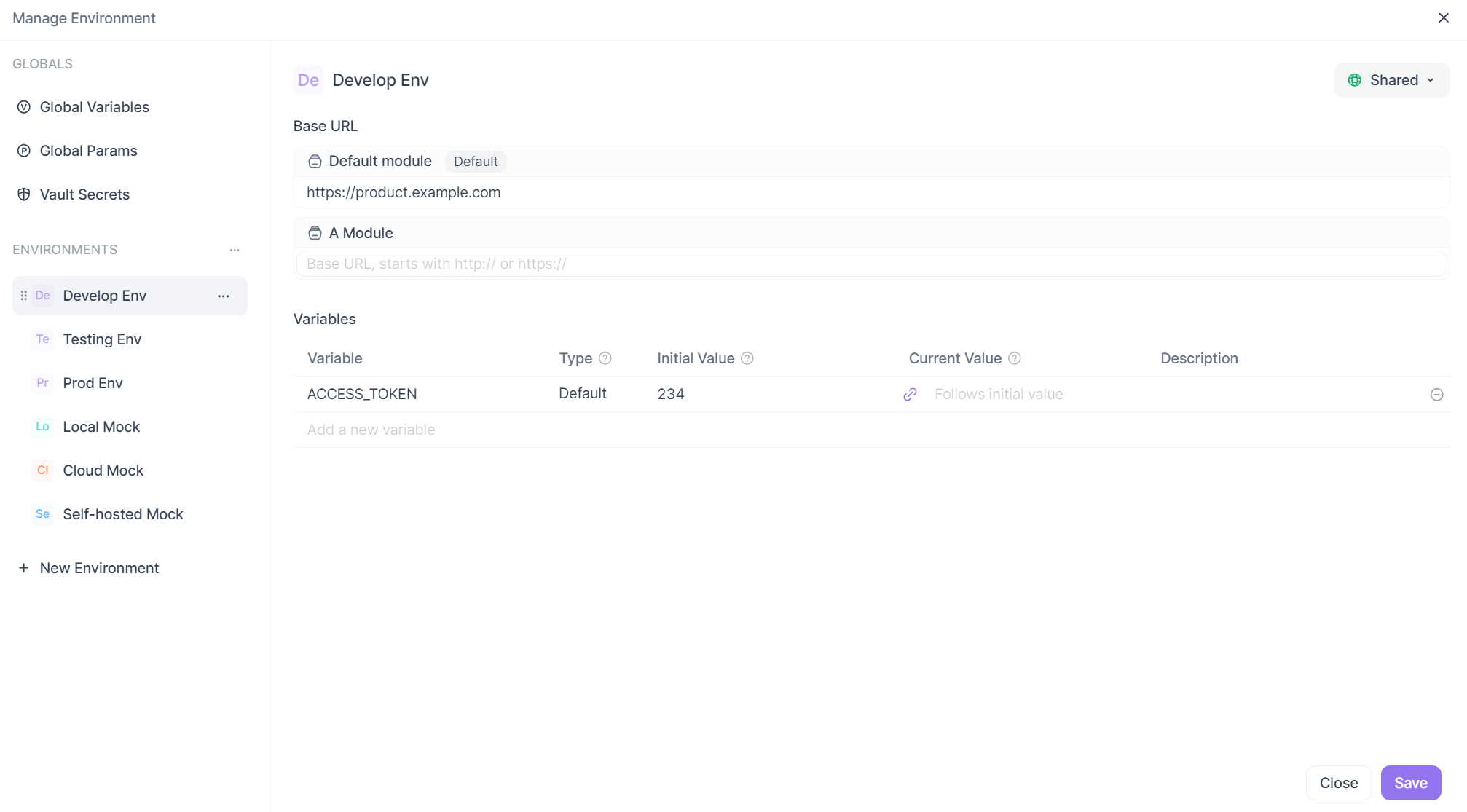
At its heart, an environment in Apidog is simply a set of key-value pairs. Think of it as a context or a scope for your variables. You can create different environments for Local Development, Staging, Production, or even Testing with User John.

Step 1: Creating and Managing Environments
Getting started is straightforward. Inside your Apidog project, you'll find a dedicated environment management section. Here, you can create a new environment and give it a clear name.
For example, you might create:
Local Dev: Points tohttp://localhost:8080Staging: Points tohttps://api-staging.yourcompany.comProduction: Points tohttps://api.yourcompany.com
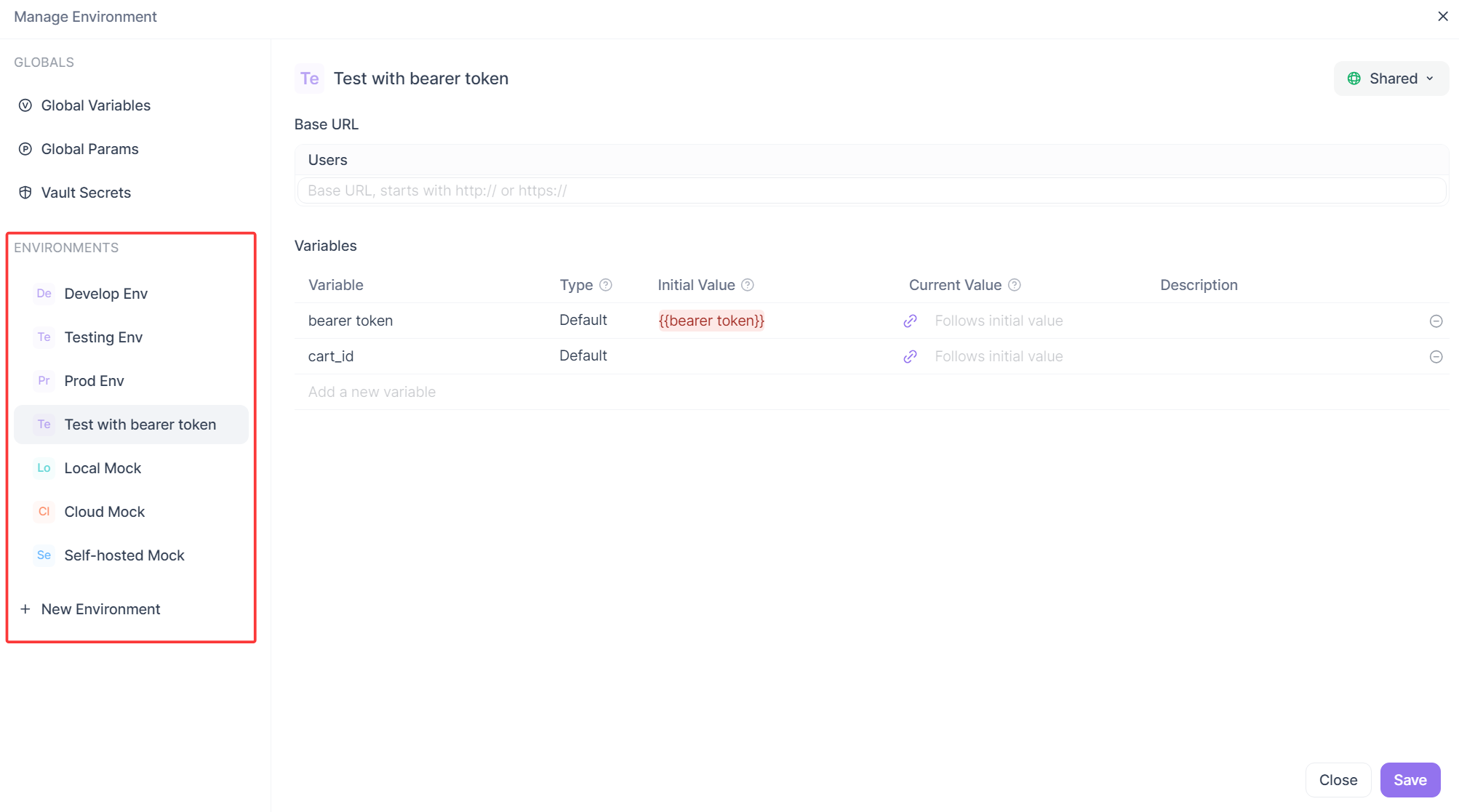
Step 2: Defining Variables within an Environment
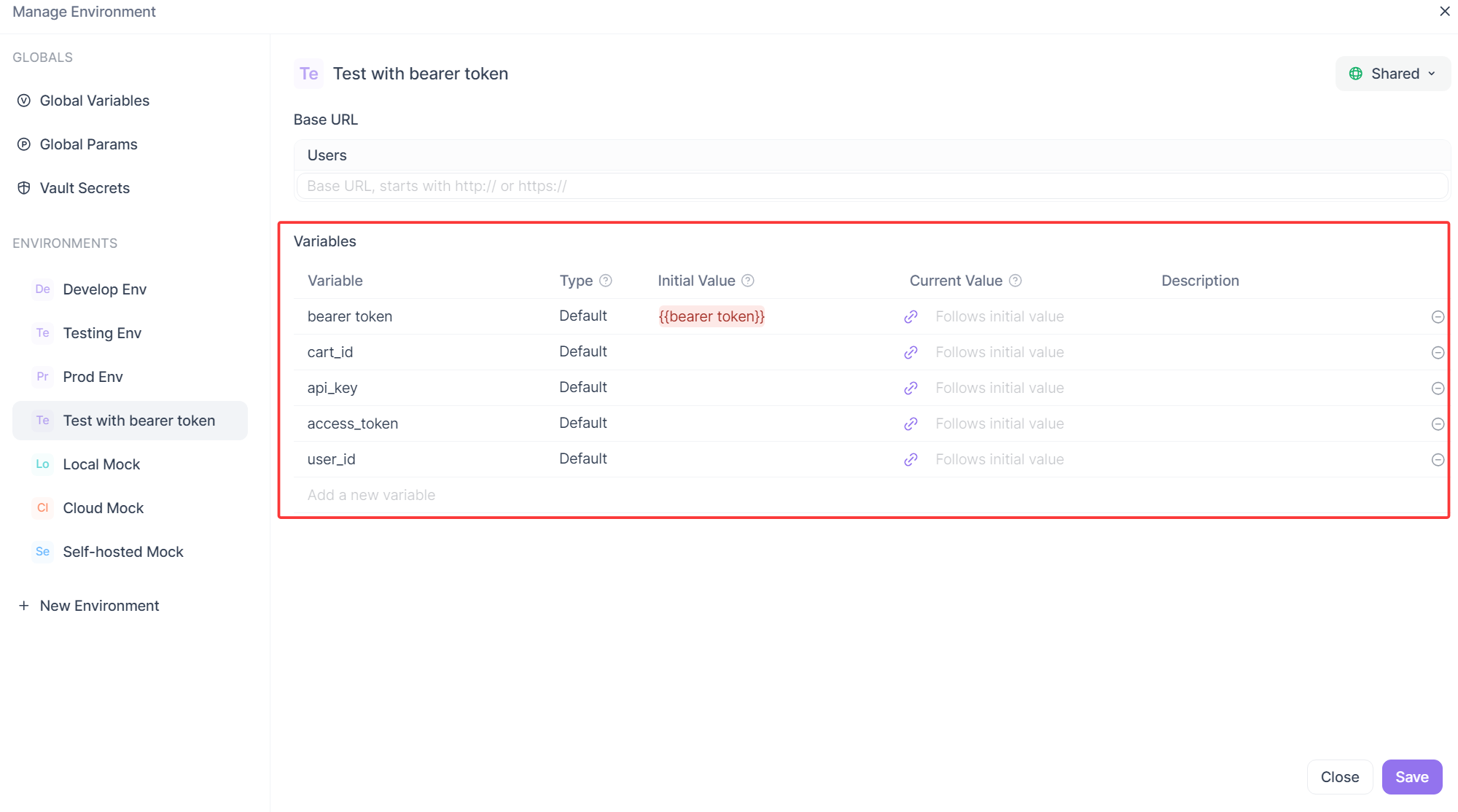
Once you have an environment, you populate it with variables. These are the dynamic pieces of data that will change between environments. The most common ones are:
api_key: A generic API key.access_token: A JWT or OAuth token.user_id: A commonly used ID for testing.
Step 3: Using Variables in Your Requests
This is where the magic happens. Apidog uses the double curly brace syntax {{variable_name}} to denote a variable. You can use these variables anywhere in Apidog:
- Headers (e.g.,
Authorization: Bearer {{access_token}}) - Query Parameters
- Request Body (in both raw and form-data modes)
When you send a request, Apidog automatically replaces those variables with the actual values from your currently selected environment. That means you can switch from local to staging environment with a single dropdown click, and every request in your collection will instantly update with the correct values for that environment.
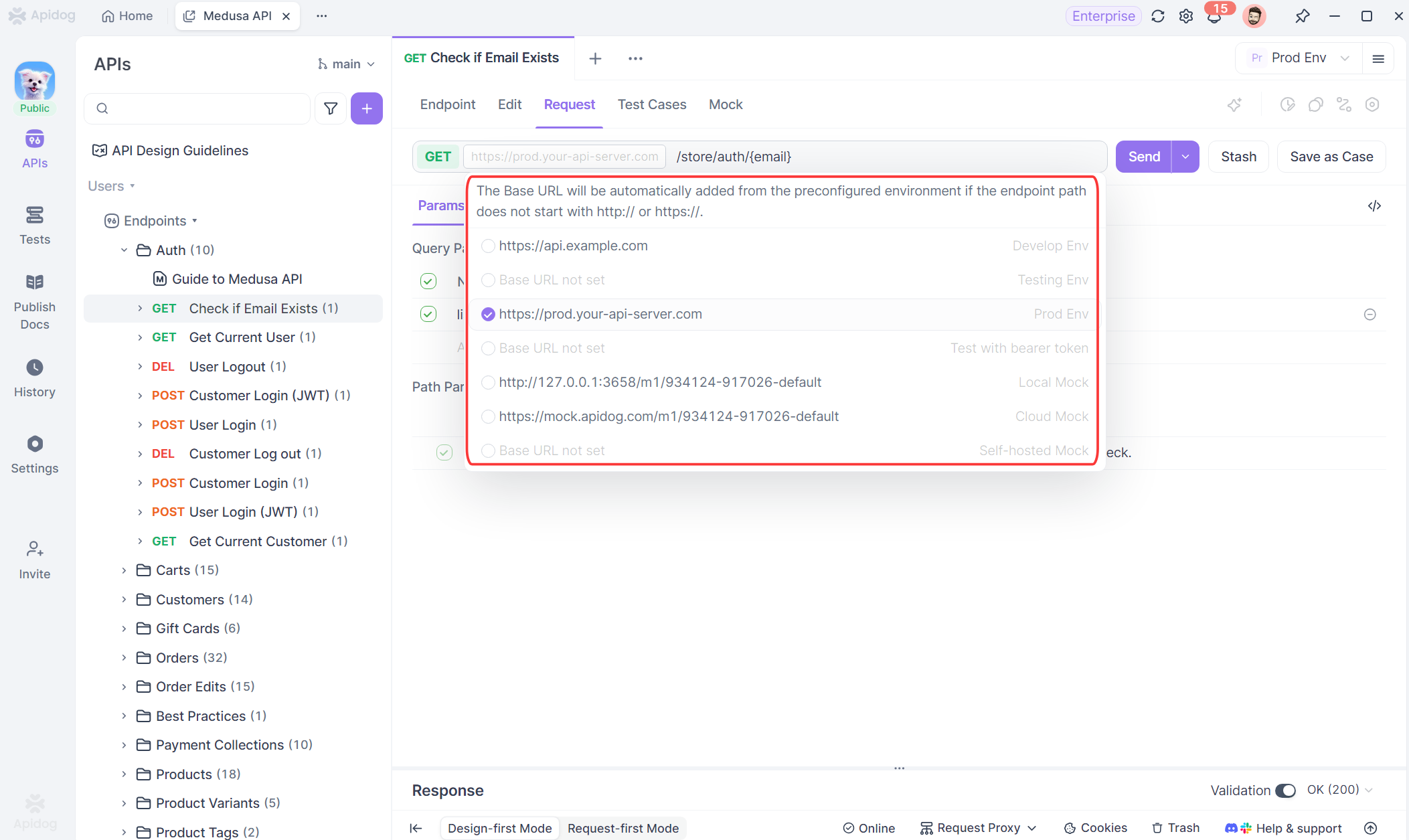
Step 4: Share the Environment Configuration with Your Team
Creating variables is great, but sharing and maintaining them across a team is even more powerful.
With Apidog, you can share environments with everyone on your team. Simply mark the environment as Shared in the top-right corner, and your teammates can start using it right away.
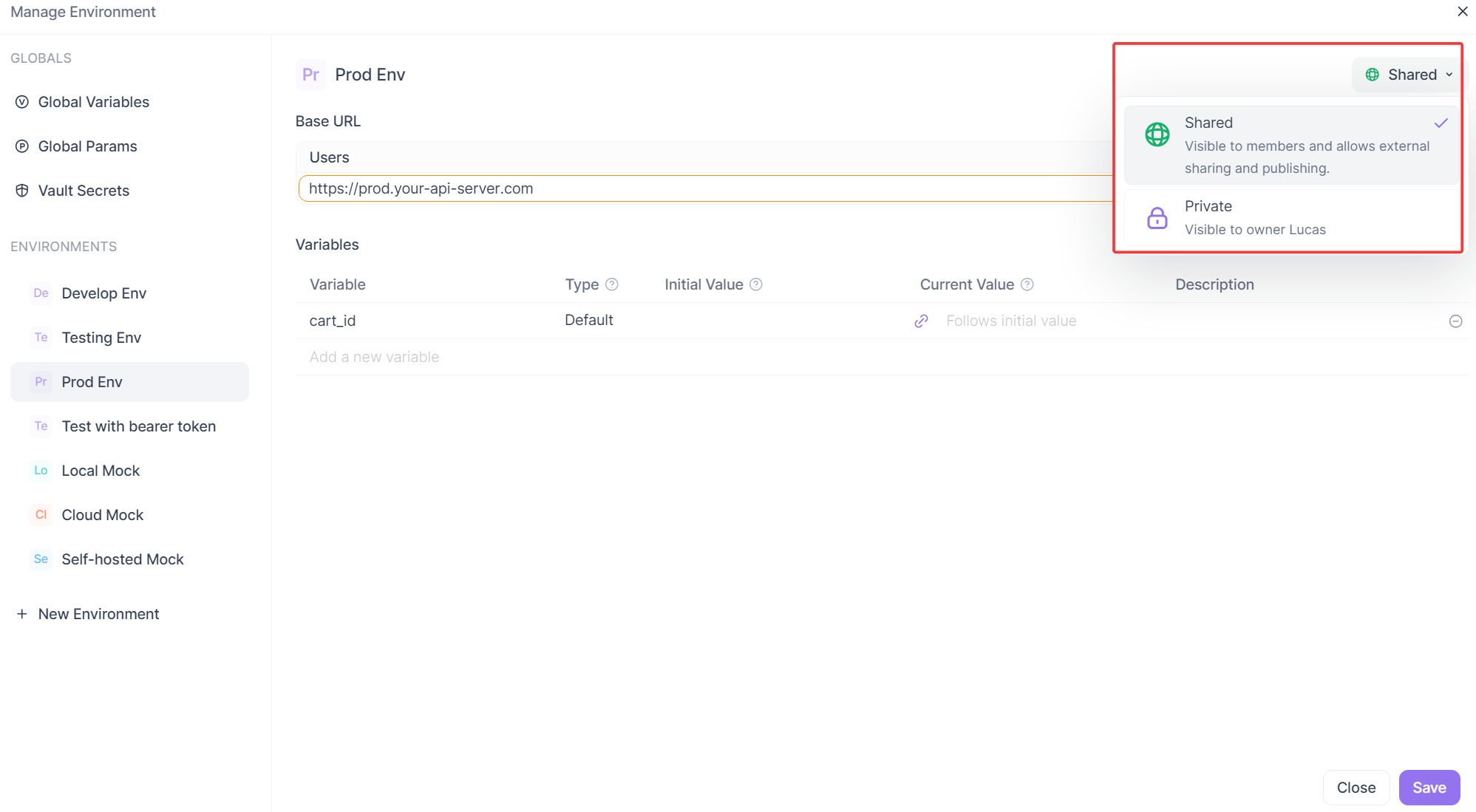

Benefits of Apidog's environment management feature:
- Consistency: Everyone on the team uses the same
Stagingenvironment configuration. There's no more confusion about which URL or test user to use. - Efficiency: When a new backend service is added, one person updates the
base_urlin the shared staging environment, and everyone on the team gets the update automatically. - Security Control: As an admin, you can control who can view and edit these shared environments, preventing accidental misconfigurations.
The Fort Knox for Your Credentials: Vault Secrets
While environment variables are great for efficiency, they are often still visible in plaintext to anyone with access to that environment. For ultra-sensitive data like production API keys, master tokens, or database passwords, you need a higher level of security.
Apidog's Vault Secrets feature takes security to the next level by integrating with enterprise-grade external vault providers. Instead of storing secrets directly in Apidog, you can fetch them from industry-standard vaults like:
This integration ensures your most sensitive credentials remain in your organization's secure vault infrastructure while still being accessible for API testing and development.
How Vault Secrets in Apidog Work?
The workflow is elegantly simple yet highly secure:
- Configure Vault Provider: Administrators configure integration with your external vault at the team or project level in Apidog. This is a one-time setup that connects Apidog to your vault infrastructure.
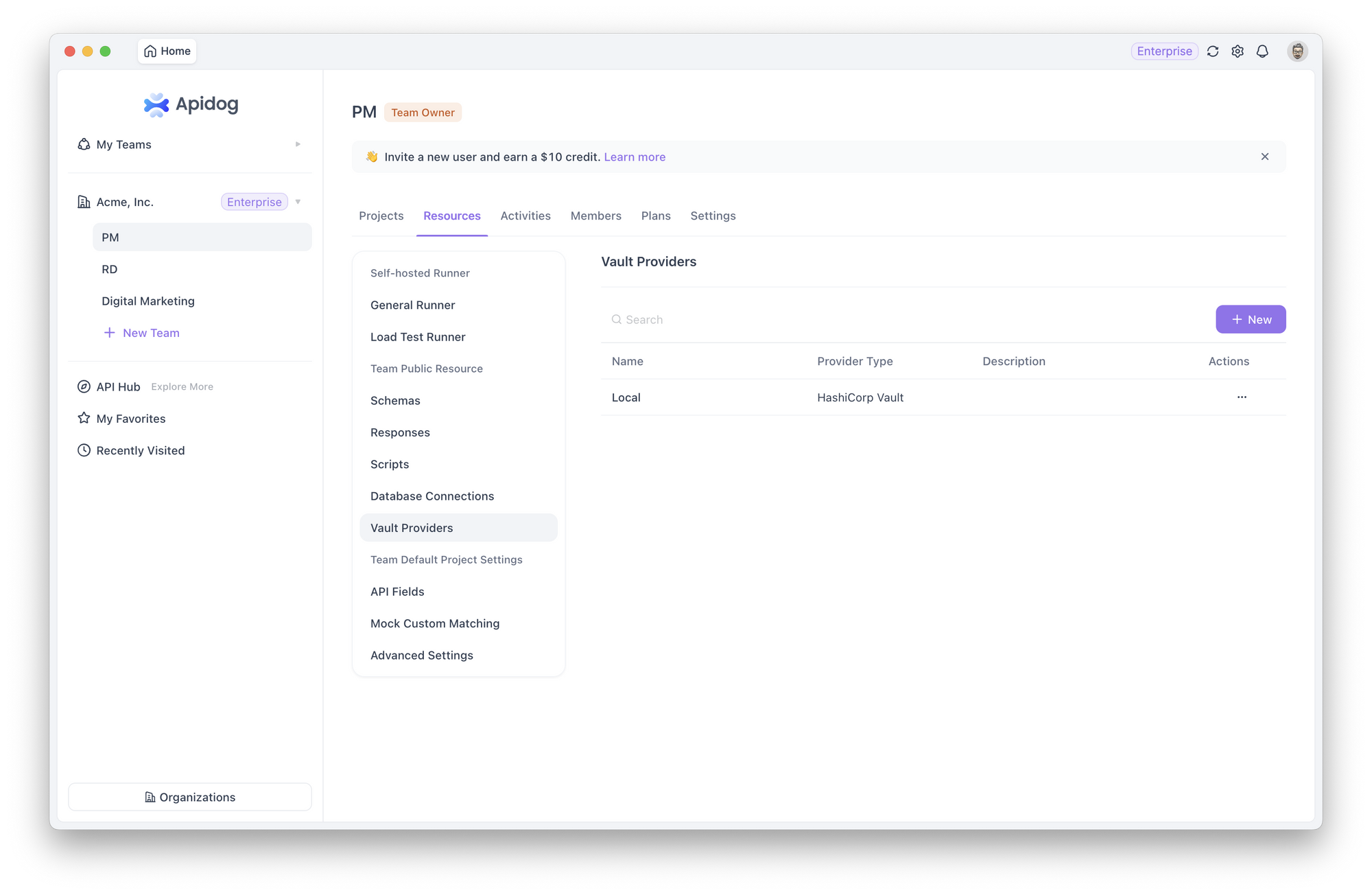
2. Link Secrets: Users link secrets by providing metadata (such as engine, path, and key) that points to secrets stored in the external vault. For example, you might link a secret named prod_payment_gateway_key stored in HashiCorp Vault.
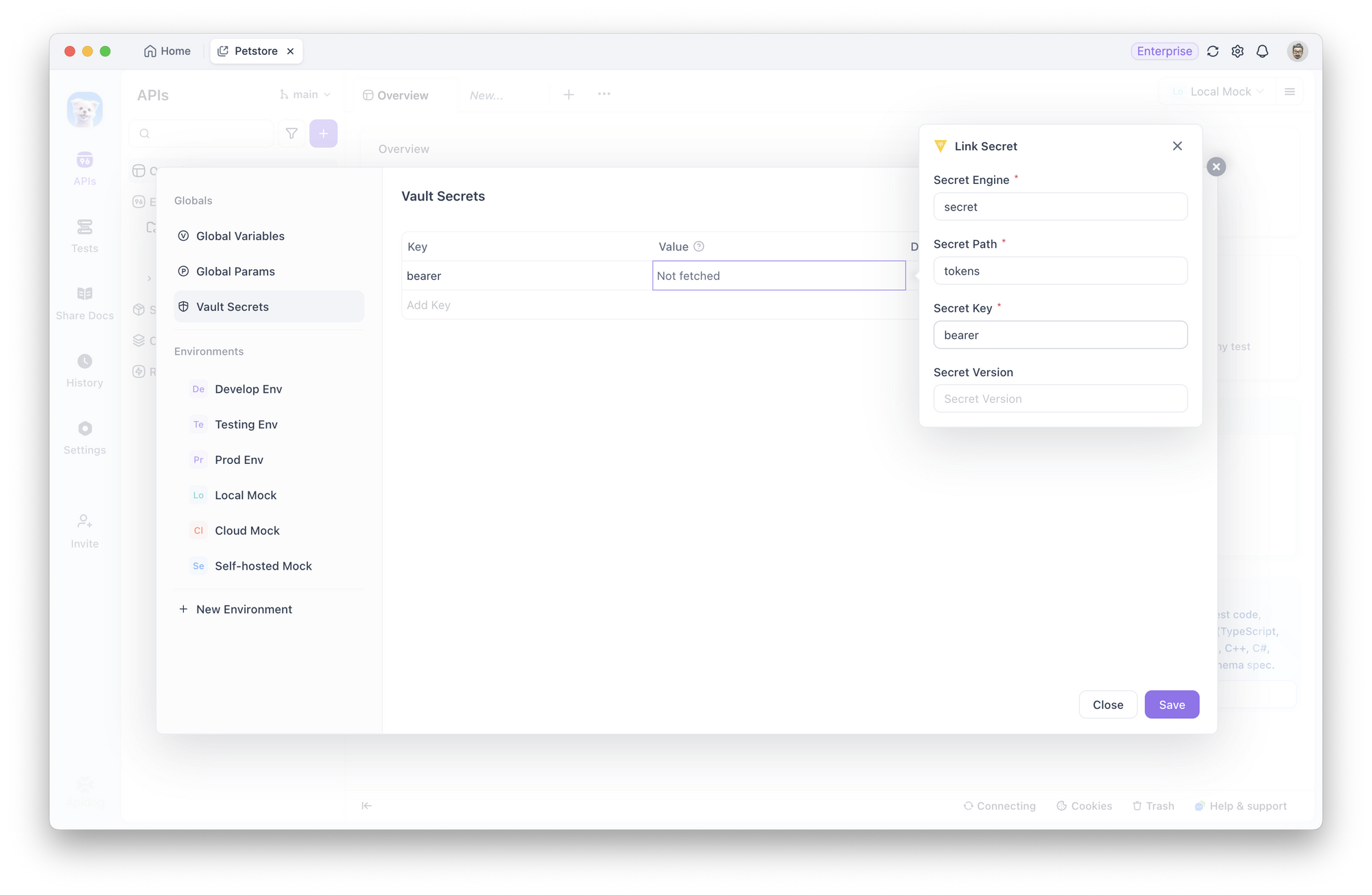
3. Fetch and Encrypt Locally: When you click "Fetch Secrets," Apidog retrieves the secret values and encrypts them locally on your client. Crucially, these secrets are never uploaded to Apidog's servers and are never shared with other team members.
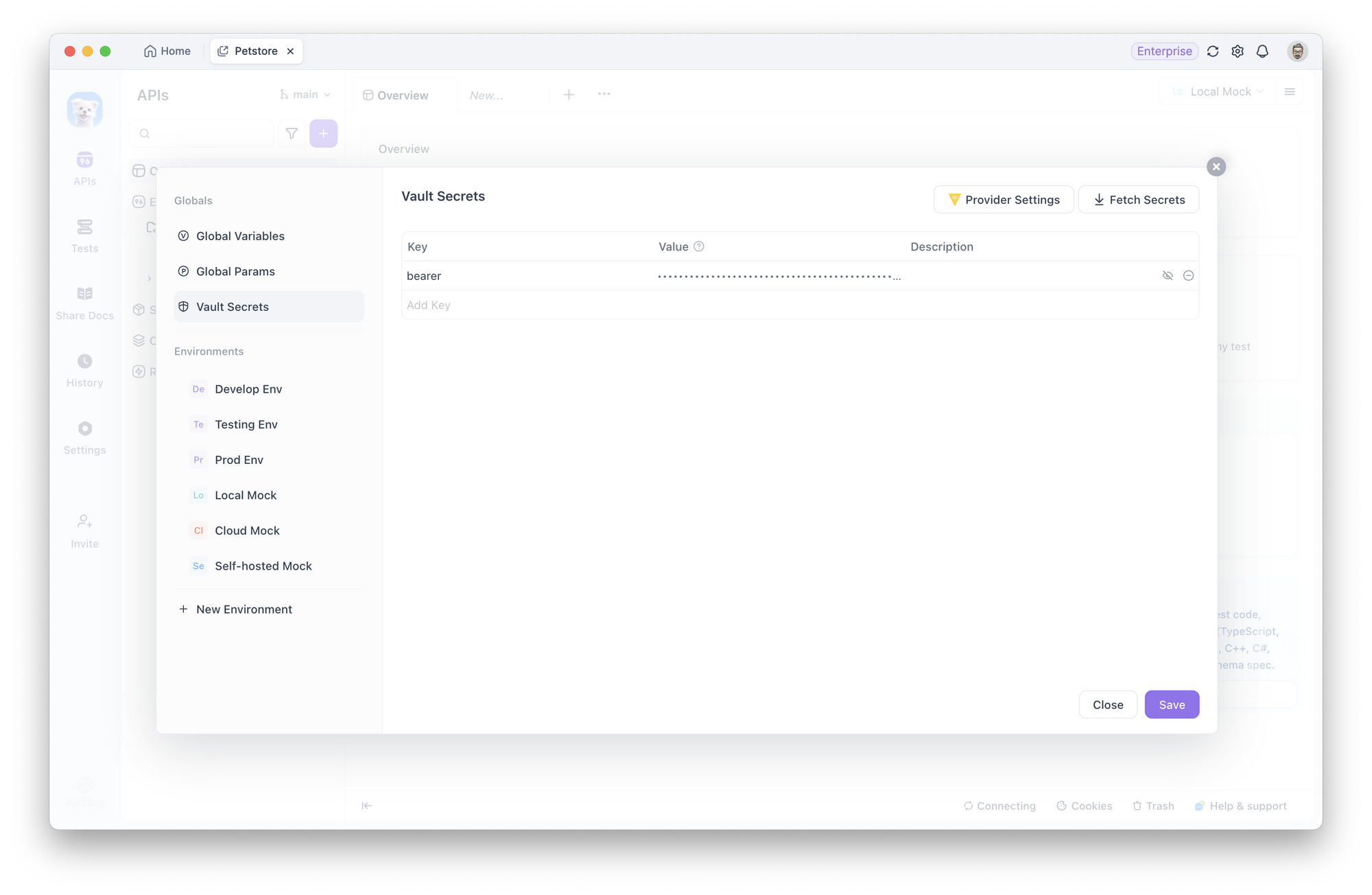
4. Use in Requests: Reference secrets using the syntax {{vault:key}} anywhere variables are supported—in headers, query parameters, or request bodies. In scripts, use await pm.vault.get("key") to access secret values securely.
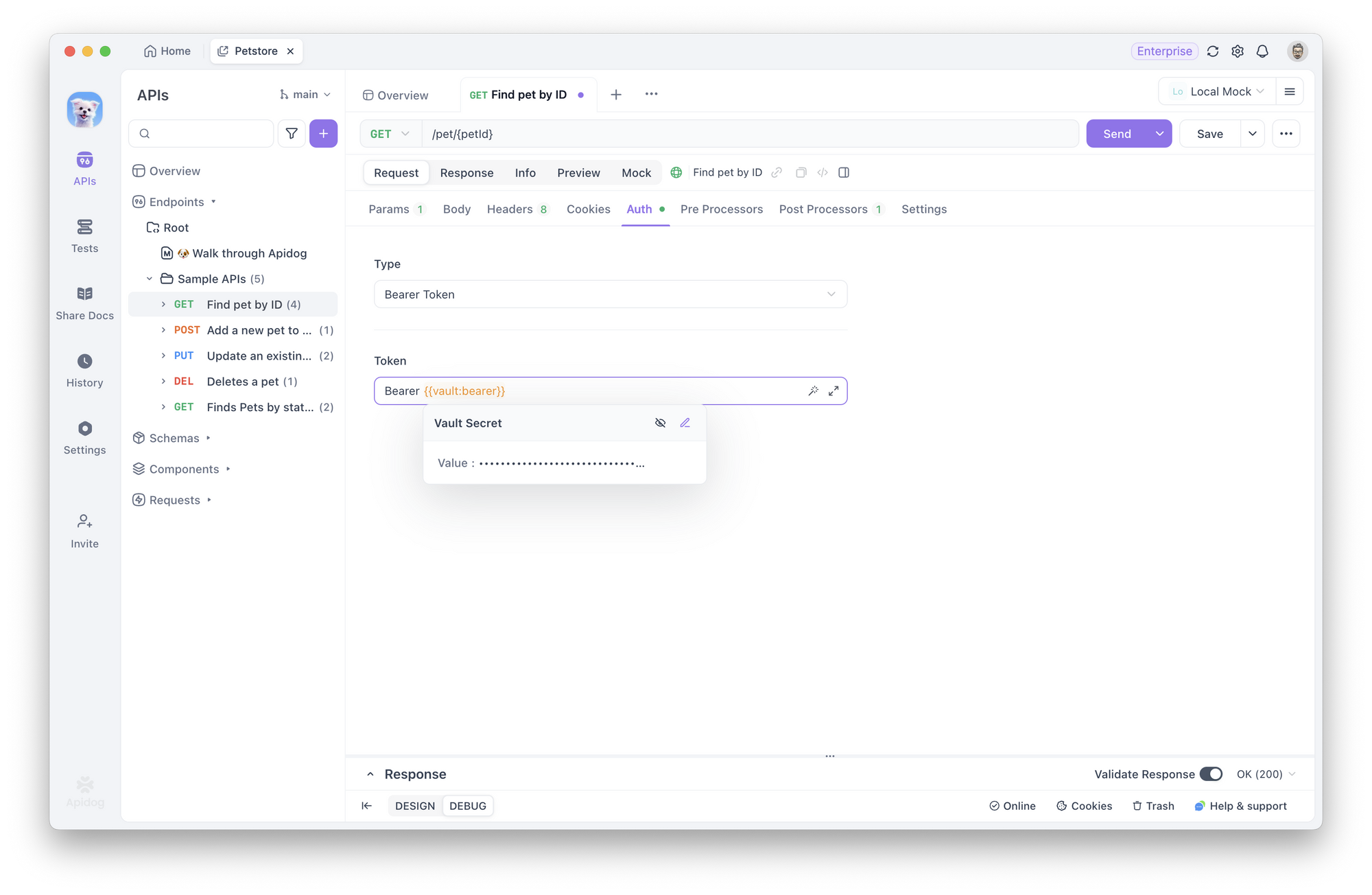
Benefits of Vault Secrets in Apidog
This architecture delivers enterprise-grade security through multiple layers:
- Secrets Stay in Your Vault: The actual secret values remain in your organization's vault infrastructure (HashiCorp, Azure, or AWS), never stored on Apidog's servers.
- Local Encryption: Fetched secrets are encrypted and stored only on your local client, ensuring they remain private and secure.
- Authentication Required: Users must authenticate with the vault provider (via OAuth2.0 or access tokens) to fetch secrets, ensuring proper access control.
- Masked Values: When secrets are printed in console logs, their values are automatically masked to prevent accidental exposure.
- Collaborative Yet Private: While secret values remain private to each user, the variable names and metadata are shared with the team. This means team members can use the same secret references without needing to reconfigure everything, while still maintaining their own secure access to the actual values.
Conclusion: Apidog Is the Future of Secure API Management
The evolution of an API developer is marked by the tools they adopt. Moving from hardcoded values and manual updates to a dynamic, variable-driven system is a quantum leap in productivity. Taking the final step to secure your secrets with a vault is what separates a good workflow from a great, enterprise-ready one.
If you're looking for an API client that goes beyond basic testing one that helps you manage multiple environments, store secrets safely, and collaborate with your team securely, Apidog is the way to go.
Apidog provides this entire spectrum of capability in one cohesive platform. It understands that environments, variables, and secrets aren't separate features; they are interconnected parts of a professional API workflow. By bringing them together with a focus on both usability and security, Apidog doesn't just help you test APIs it helps you build a robust, scalable, and collaborative API practice.
So, stop copying and pasting API keys. Stop worrying about sharing collections. Embrace a tool that's designed for the way modern teams actually work. Your future self and your teammates will thank you for it.



