APIs (Application Programming Interfaces) are the backbone of modern software development. They enable different systems to communicate and share data seamlessly. However, with great power comes great responsibility. API security has become crucial as more businesses integrate APIs into their operations. In this blog post, we’ll dive into the common security issues with API frameworks, highlighting key vulnerabilities and how to mitigate them.
Understanding API Security
APIs are designed to be accessed over the internet, which exposes them to various security threats. Ensuring API security means protecting the API itself and the data it handles from unauthorized access and other malicious activities. Let's explore some of the most common security issues with API frameworks.
1. Lack of Authentication and Authorization
One of the most fundamental security issues with APIs is the lack of proper authentication and authorization mechanisms. Without these, anyone can access your API and potentially misuse it.
- Authentication ensures that the entity trying to access the API is who they claim to be.
- Authorization determines what an authenticated entity is allowed to do.
Solution: Implement strong authentication methods such as OAuth, JWT (JSON Web Tokens), or API keys. Additionally, enforce role-based access control (RBAC) to ensure users only have access to the resources they need.
2. Insufficient Rate Limiting
APIs without rate limiting are susceptible to abuse, such as DDoS (Distributed Denial of Service) attacks. Rate limiting controls how many requests a client can make in a given period.
Solution: Implement rate limiting to protect your API from being overwhelmed. This can be done using techniques such as token bucket algorithms or implementing API gateways that handle rate limiting for you.

3. Insecure Data Transmission
Transmitting data over HTTP without encryption exposes it to eavesdropping and man-in-the-middle attacks. Sensitive data, including user credentials and personal information, must be protected during transmission.
Solution: Always use HTTPS to encrypt data in transit. Implementing TLS (Transport Layer Security) ensures that data exchanged between the client and server remains confidential and tamper-proof.
4. Exposure of Sensitive Data
APIs sometimes inadvertently expose sensitive data through verbose error messages, unnecessary data in responses, or improper access controls.
Solution: Minimize data exposure by only returning necessary information. Avoid including sensitive data in URLs and use secure error handling that does not reveal implementation details.
5. Injection Attacks
Injection attacks, such as SQL injection, occur when untrusted data is sent to an interpreter as part of a command or query. This can compromise the entire database.
Solution: Use parameterized queries and prepared statements to prevent injection attacks. Additionally, validate and sanitize all user inputs.
6. Lack of Input Validation
APIs that do not validate input data are vulnerable to various attacks, including injection and cross-site scripting (XSS).
Solution: Implement strict input validation and sanitization. Use whitelisting where possible to ensure only valid data is processed.
7. Improper Error Handling
Exposing detailed error messages can give attackers insights into your API’s structure and potential vulnerabilities.
Solution: Implement generic error messages for clients and log detailed errors internally. This helps maintain security while still providing useful information for debugging.
8. Broken Authentication and Session Management
Weak authentication mechanisms and improper session management can lead to unauthorized access.
Solution: Ensure robust session management by using secure cookies, setting appropriate expiration times, and invalidating sessions after logout or inactivity. Use multi-factor authentication (MFA) to add an extra layer of security.
9. API Endpoint Enumeration
Attackers can discover hidden API endpoints through endpoint enumeration, leading to potential exploitation.
Solution: Avoid predictable endpoint names and implement proper access controls. Use tools to scan your API for unintended exposures.
10. Insufficient Logging and Monitoring
Without proper logging and monitoring, it’s challenging to detect and respond to security incidents.
Solution: Implement comprehensive logging of all API activities and set up real-time monitoring to detect and respond to suspicious activities promptly.
Use Apidog to Ensure Web API Security
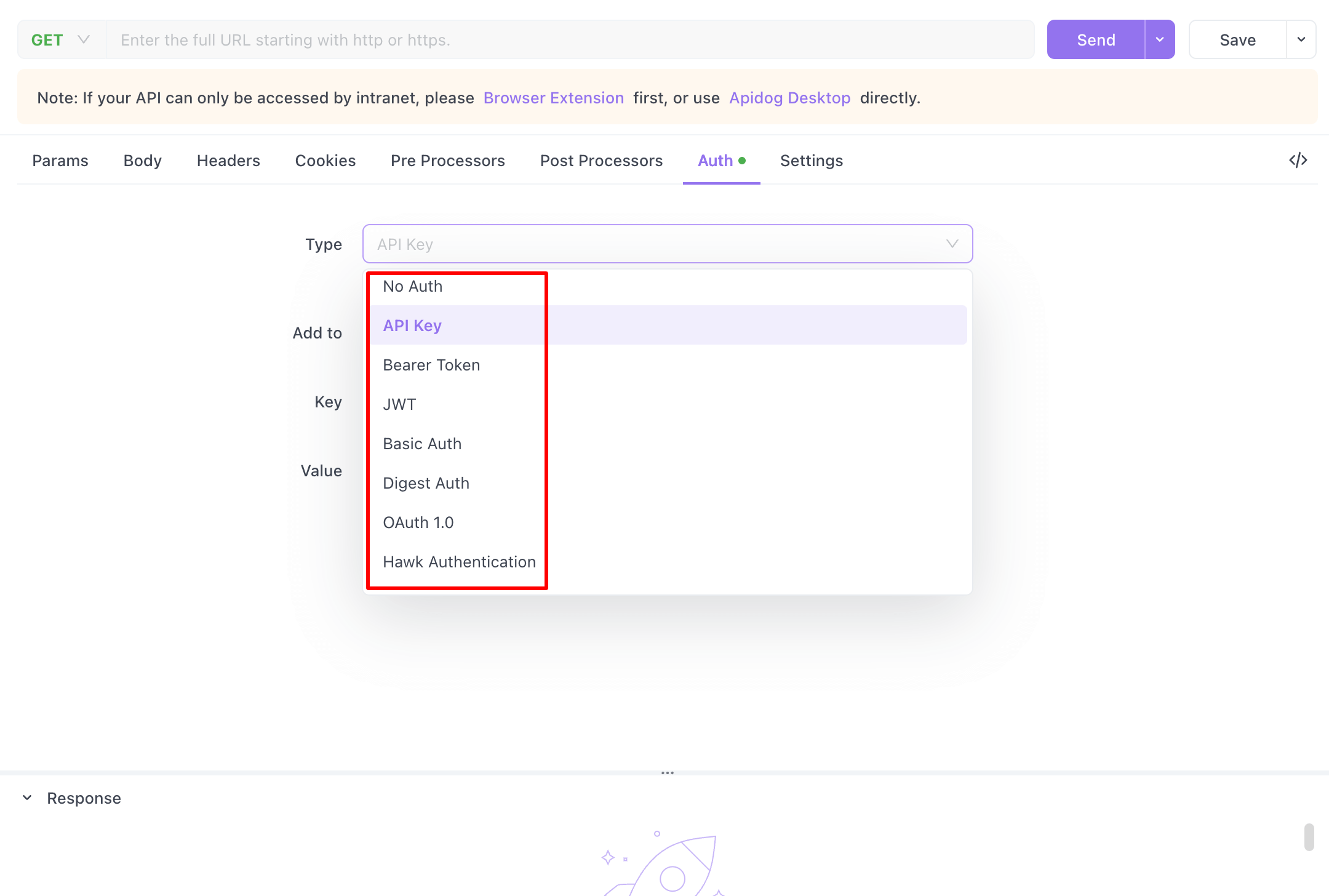
Apidog is a robust Web API security tool that supports various authentication methods to meet different security needs. It includes Bearer Token, Basic Auth, Digest Auth, OAuth 1.0, Hawk Authentication, AWS Signature, NTLM Authentication, and Akamai EdgeGrid. These options help developers secure their APIs effectively, ensuring data protection and compliance with authentication standards.
Enhancing API Security with Apidog's CLI
Apidog's Command Line Interface (CLI) is a powerful tool that enhances API security by enabling developers to interact directly with Apidog from their terminals. This advanced feature offers greater control and flexibility and allows developers to automate tasks, trigger tests, and manage APIs securely. Moreover, the CLI's compatibility with CI/CD tools makes it a vital part of the secure development and deployment process.
Secured Data Transmission with Apidog SSL
SSL (Secure Sockets Layer) is an essential element of secure API communication, and Apidog's CLI doesn't fall short in this aspect. It supports SSL functionality, ensuring all data transmitted between clients and your APIs is encrypted and secure. The added support for custom SSL certificates and automatic SSL certificate management further amplifies the security of your API communication.
Protecting Data with Apidog's Smart Mock Server:
Apidog's Mock Server is a standout feature that enhances API security by simulating API endpoints. It allows developers to perform tests and developments without exposing sensitive data. The mock responses are designed to accurately mimic the actual API's behavior, enabling comprehensive testing while maintaining data security.
Conclusion
Securing your API is a continuous process that requires vigilance and proactive measures. By addressing the common security issues outlined in this post, you can significantly reduce the risk of breaches and ensure the integrity of your API.
For a robust solution that simplifies API security, consider using Apidog. Apidog offers a suite of tools designed to help you build, test, and secure your APIs effectively. Download Apidog for free today and take the first step towards securing your APIs.