When building applications, third-party APIs are invaluable for enhancing application functionality and fostering integration, but they also introduce significant security risks that can endanger both data integrity and user privacy. This article focuses on the security challenges posed by third-party APIs, offering best practices for protecting your systems. We'll examine real-world case studies of security breaches to underscore the importance of robust API security measures and discuss the legal and compliance aspects critical to maintaining user trust and data protection.
Understanding the Risks
Integrating third-party APIs into your applications offers numerous benefits, but it also introduces several security risks. Here’s an in-depth look at the potential dangers:
Data Breaches
When you use third-party APIs, sensitive data often travels between your application and the third-party service. If the API isn't adequately secured, this data can be intercepted by malicious actors, leading to data breaches. Ensuring that APIs use encryption protocols such as HTTPS is crucial to protect this data in transit.
Unauthorized Access
Without proper authentication and authorization mechanisms, third-party APIs can become gateways for unauthorized access. Malicious users can exploit vulnerabilities to gain access to your systems and data. Implementing robust authentication methods like OAuth and API keys helps mitigate this risk by ensuring only authorized users can access your APIs.
Dependency on External Security
When you rely on third-party APIs, you're also relying on the security practices of the API provider. If their security measures are inadequate, your application becomes vulnerable. Regularly review the security policies and practices of your third-party providers to ensure they align with your standards.
Inadequate Input Validation
Third-party APIs can be susceptible to various injection attacks if they do not properly validate input. Attackers can exploit these vulnerabilities to execute malicious code or manipulate data. Ensuring that both your application and the API provider validate and sanitize inputs can prevent such attacks.
Rate Limiting and Abuse
APIs that do not implement rate limiting are vulnerable to abuse. Malicious actors can overwhelm your system with excessive requests, leading to denial of service attacks. Implementing rate limiting and throttling mechanisms helps to control the volume of requests and protect against abuse.
Monitoring and Logging
A lack of proper monitoring and logging can leave your application blind to malicious activities. Without these measures, detecting and responding to security incidents becomes challenging. Ensuring comprehensive monitoring and logging of API usage allows you to detect anomalies and respond to potential threats promptly.
Third-Party API Breaches
Even if your application is secure, a breach in the third-party API provider's system can affect you. This risk underscores the importance of choosing reputable API providers who adhere to stringent security standards and regularly audit their security practices.
Understanding these risks is the first step toward implementing effective security measures for third-party APIs. By recognizing and addressing these vulnerabilities, you can better protect your data and users from potential security threats.
Best Practices for API Security
Securing third-party APIs is crucial to safeguarding your application and its users. Here, we’ll explore comprehensive best practices to help you strengthen your API security. Each point is detailed with explanations and, where appropriate, illustrative stories to make the concepts clear and relatable.
Authentication and Authorization
Here, we’ll explore comprehensive best practices to help you strengthen your API security. Each point is detailed with explanations and, where appropriate, illustrative stories to make the concepts clear and relatable.
- OAuth: OAuth is a widely adopted authorization framework that allows third-party services to exchange tokens for access to your API without exposing user credentials. For instance, when you log in to a new app using your Google or Facebook account, OAuth is handling the authentication process seamlessly.
- API Keys: API keys are unique identifiers assigned to a user, application, or device accessing an API. They are simple to implement but should be treated with caution. For example, consider an e-commerce platform using an API key to allow third-party logistics providers to access shipment details. If this key is compromised, the logistics provider’s access must be immediately revoked.
- Tokens: Use tokens with expiration dates for enhanced security. Tokens should be short-lived and require renewal. This practice ensures that even if a token is intercepted, it will soon become useless.
Data Encryption
Data encryption is vital to protect sensitive information from being accessed by unauthorized parties. Encryption ensures that data remains confidential and intact, whether it is being transmitted between systems or stored at rest. Implementing robust encryption practices helps prevent data breaches and maintains user trust.
- HTTPS: Always use HTTPS to encrypt data transmitted between your application and the API server. This prevents eavesdropping and man-in-the-middle attacks. For example, when you see a padlock icon in your browser’s address bar while visiting a secure website, it indicates that HTTPS is protecting your data.
- Data Encryption at Rest: Encrypt sensitive data stored on servers or databases. For instance, a healthcare app storing patient records should use encryption to protect this data both in transit and at rest. This ensures that even if data is compromised, it remains unreadable without the decryption key.
Rate Limiting and Throttling
- Rate Limiting: Set limits on the number of requests a client can make to your API within a specific time frame. For instance, a weather service API might limit users to 100 requests per hour to prevent overload and abuse.
- Throttling: Implement throttling to control the request rate, ensuring that your API can handle high traffic without crashing. Throttling helps maintain performance during peak usage times. For example, during a major product launch, throttling can prevent a sudden surge in traffic from overwhelming the API.
Input Validation
- Prevent Injection Attacks: Always validate and sanitize inputs to prevent SQL injection, cross-site scripting (XSS), and other injection attacks. For instance, if an API endpoint receives user input for a search query, ensure that the input is sanitized to remove any harmful code.
- Use Libraries and Frameworks: Utilize established libraries and frameworks that handle input validation. For example, using Django’s form validation or JavaScript’s built-in validation functions can help protect against common vulnerabilities.
Monitoring and Logging
- Comprehensive Logging: Maintain detailed logs of API requests, including timestamps, IP addresses, request types, and responses. This information is invaluable for detecting suspicious activities. For instance, if you notice an unusually high number of failed login attempts from a single IP address, it could indicate a brute-force attack.
- Real-Time Monitoring: Implement real-time monitoring tools to track API performance and security incidents. Tools like Prometheus, Grafana, or commercial solutions like Datadog can help you visualize and respond to anomalies quickly.
Secure Coding Practices
- Input Validation: Always validate inputs on both the client and server sides. This double-checks inputs for malicious code or data that could exploit vulnerabilities.
- Avoid Hardcoding Secrets: Never hardcode sensitive information, such as API keys or passwords, in your code. Use environment variables or secure vaults like AWS Secrets Manager or Infisical.
Regular Security Audits and Updates
- Conduct Regular Audits: Perform regular security audits and code reviews to identify and fix vulnerabilities. For example, a financial app might undergo quarterly security audits to ensure compliance with the latest security standards.
- Keep Software Updated: Ensure that all dependencies and libraries are up-to-date with the latest security patches. Vulnerable software can be an easy target for attackers. For instance, updating a vulnerable version of a library in your application can prevent exploits that have been patched in newer versions.
How Apidog can help us:
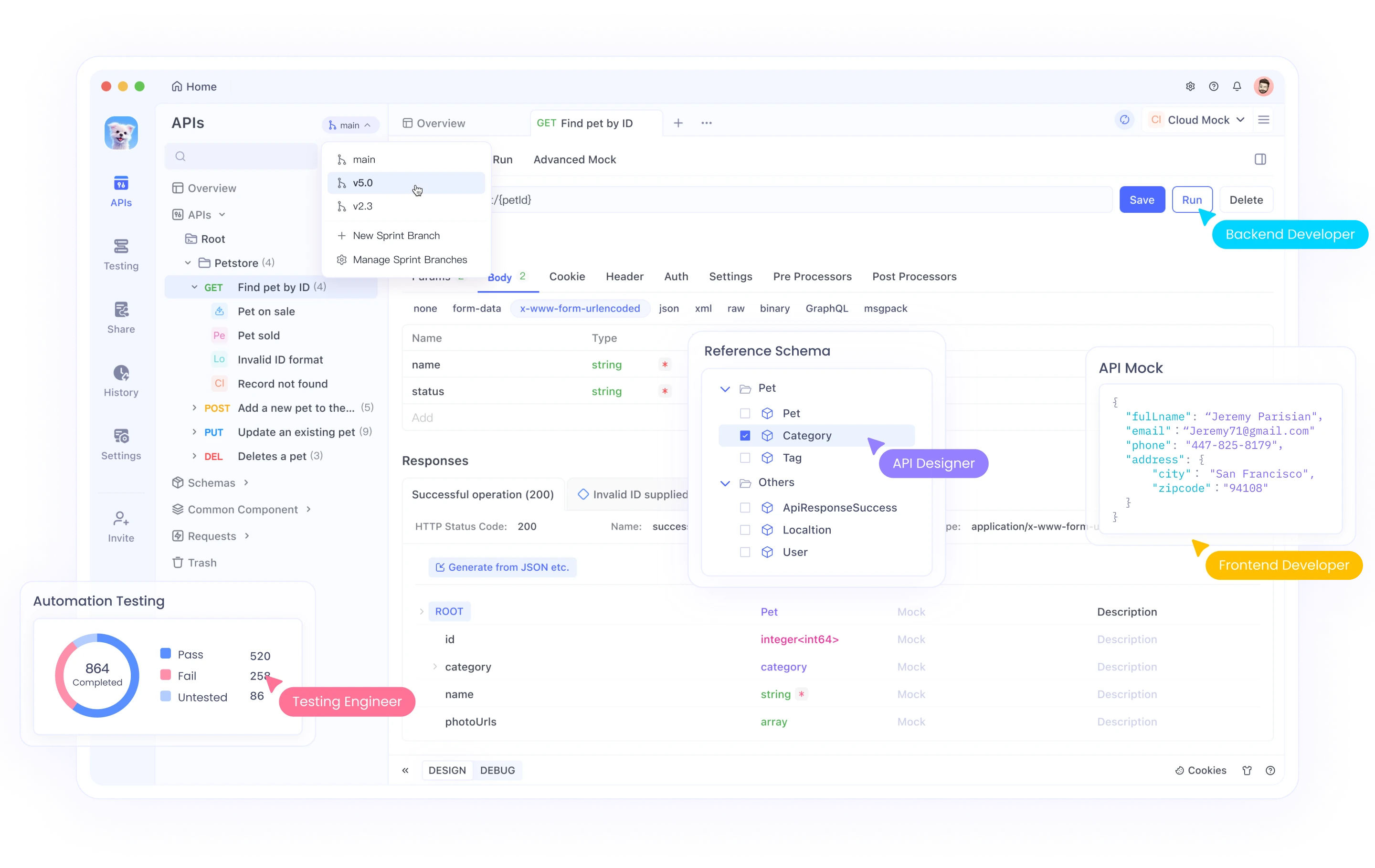
Apidog enhances API security by offering robust documentation, automated testing, and real-time monitoring. Apidog also aids in compliance with industry standards like GDPR and HIPAA, ensuring your APIs protect user data effectively.
Additionally, Apidog supports team collaboration, fostering a security-focused development environment. By integrating Apidog, you can build secure, reliable, and compliant APIs, protecting your data and users from various security threats.
Conclusion:
By following these best practices, you can significantly enhance the security of your third-party APIs, protecting your application and users from various threats. Implementing robust authentication, encryption, rate limiting, and thorough monitoring, along with adhering to legal requirements and continuously updating your security measures, will help you build a secure and resilient API ecosystem for you and your users.




