The OAuth 2.0 authorization framework underpins secure authorization by offering a mechanism for applications to acquire limited access to user accounts on an HTTP service. This guide dives into the various grant types utilized within OAuth 2.0, which dictate the way client applications secure access tokens to access user resources on a resource server.
If you wish to learn more about Apidog and its comprehensive features, click the button below to begin! 👇

Before venturing deeper into OAuth 2.0's grant types, let's take a brief recap on what OAuth 2.0 is.
What is OAuth 2.0?
OAuth 2.0 is an industry-standard authorization protocol. It facilitates secure access delegation between applications (clients) and user accounts hosted by separate services (resource servers). This allows users to grant applications permission to access their information on the resource server without directly sharing their credentials.

What are OAuth 2.0 Grant Types?
The OAuth 2.0 authorization framework is a type of mechanism that defines how client applications acquire access tokens. These access tokens are crucial for assessing user resources hosted on a separate server (also known as the resource server). Through employing grant types, OAuth 2.0 can ensure secure authorization without requiring its users to expose their credentials to the client application.
Detailed Breakdown of the Different OAuth 2.0 Grant Types
1. Authorization Code Grant: This widely used flow prioritizes security. It involves a four-step exchange:
- The user consents to the client application accessing their resources.
- The authorization server returns a temporary authorization code to the client.
- The client exchanges this code for an access token from the authorization server.
- The access token is used by the client to access user resources on the resource server.
Pros: Highly secure due to the separation of authorization code and access token. Ideal for server-side applications with secure storage for the client's secret.
Cons: Requires multiple redirects between the client application, authorization server, and resource server.
2. Resource Owner Password Credentials Grant: This method leverages the user's login credentials directly.
- The client application obtains the user's username and password.
- These credentials are sent to the authorization server for verification and token exchange.
- Upon successful verification, the client receives an access token.
Pros: Straightforward implementation, particularly suited for trusted first-party applications.
Cons: Less secure as it exposes user credentials. Not recommended for public client applications due to security risks.
3. Client Credentials Grant: Designed for applications acting on their own behalf, not a specific user.
- The client application uses its unique ID and secret to directly request an access token from the authorization server.
Pros: Efficient for machine-to-machine interactions where user involvement isn't necessary.
Cons: Access granted is on behalf of the application itself, not a specific user. Requires careful consideration of the permissions granted.
4. Implicit Grant: Often used in mobile or single-page applications, it simplifies the flow by returning the access token directly to the client application.
Pros: Streamlined user experience due to the single redirect.
Cons: Less secure as the access token is exposed to the client application, potentially vulnerable to theft. Not recommended for applications where sensitive data is involved.
5. Refresh Token Grant: Provides a mechanism to obtain new access tokens without requiring user re-authentication.
- When an access token expires, the client application uses a refresh token obtained during the initial flow to request a new access token from the authorization server.
Pros: Enhances user experience by eliminating frequent login prompts.
Cons: Introduces another token that needs to be securely managed.
How to Choose the Correct OAuth 2.0 Grant Type for Your API
1. Security Needs:
- When prioritizing security: Choose the Authorization Code Grant. This flow separates the authorization code and access token, minimizing risk even if the code is intercepted.
- If you have lower security concerns and a trusted client application: The Resource Owner Password Credentials Grant might be suitable, but proceed with caution as user credentials are directly involved.
2. User Experience:
- If seamless user experience is a must: The Implicit Grant delivers a swift flow with a single redirect. However, keep in mind that the exposed access token raises security concerns.
- Are you trying to balance convenience with security? The Authorization Code Grant offers a good compromise, although it involves more redirects.
3. Client Application Type:
- Does the client application have a secure server-side storage (e.g., web application)? The Authorization Code Grant and Client Credentials Grant are both viable options.
- Client is a public application (e.g., mobile app)? The Authorization Code Grant with Proof Key for Code Exchange (PKCE) is recommended for enhanced security. PKCE eliminates the risk of authorization code theft even in public environments.
- Machine-to-machine communication? The Client Credentials Grant reigns supreme here, granting access tokens directly to the client application itself.
Remember:
- Sensitive data? Always prioritize security and avoid the Implicit Grant.
- Refresh tokens enhance user experience by reducing login prompts, but introduce another management layer.
Choose OAuth 2.0 Authentication for Your API with Apidog
Apidog is an all-in-one API development platform that enables developers to build, test, mock, and document APIs. With access to functionalities for the entire API lifecycle, API developers using Apidog will no longer have to worry about software compatibility when moving around their API files from one application to another!


Building APIs from Scratch with Apidog
If you need an API tool to help you create APIs, Apidog has got you covered. Take a look at this section to understand how you can use Apidog to create APIs in no time.
Begin by pressing the New API button, as shown in the image above.
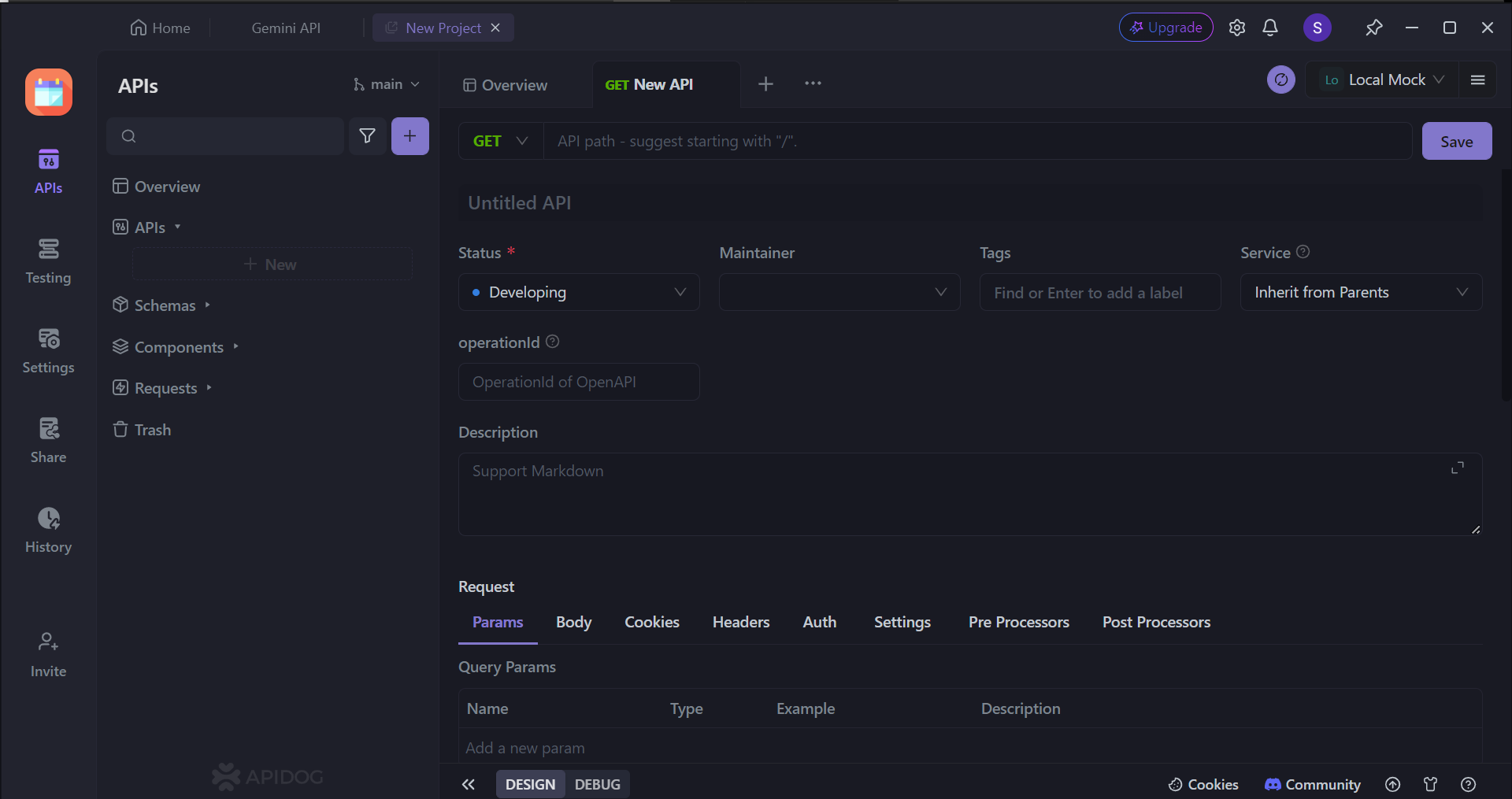
Next, you can select many of the API's characteristics. On this page, you can:
- Set the HTTP method (GET, POST, PUT, or DELETE)
- Set the API URL (or API endpoint) for client-server interaction
- Include one/multiple parameters to be passed in the API URL
- Provide a description of what functionality the API aims to provide.
To provide some assistance in creating APIs in case this is your first time creating one, you may consider reading these articles to understand the best practices for making REST APIs (or APIs in general):


Selecting OAuth 2.0 Authentication with Apidog
With Apidog's simple and intuitive user interface, you can easily choose OAuth 2.0 - or any other authentication type - in just a matter of seconds!
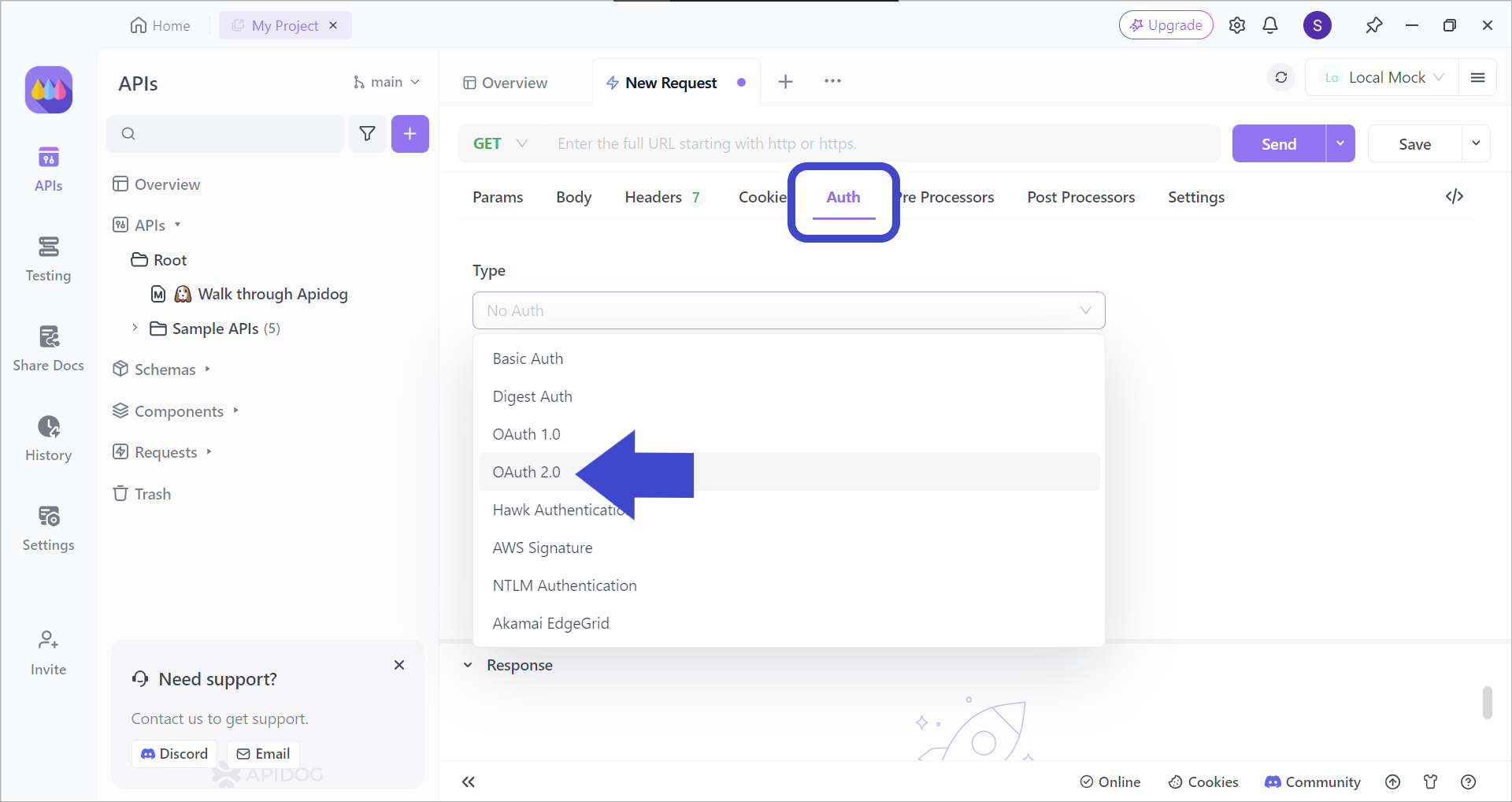
After creating a new request, pick the OAuth 2.0 authentication type, as seen in the image above. This will ensure that your APIs will have better security!
Conclusion
Mastering OAuth 2.0 grant types empowers developers to craft secure and user-friendly authorization workflows for their applications. By carefully evaluating factors like security posture, user experience, and client application type, developers can select the most appropriate grant type. This selection ensures a balance between robust access control and a seamless user journey.
Understanding grant types is an essential skill for developers working with OAuth 2.0. By leveraging the knowledge presented in this guide, developers can make informed decisions when designing secure and efficient authorization mechanisms for their applications.
![[Guide] OAuth 2.0 Grant Types](https://assets.apidog.com/blog-next/2026/02/oauth-2-grant-types.png)



