In today's digital world, applications often need to access user data on other platforms, like social media or cloud storage. Traditionally, this meant users had to re-enter their credentials for each service, raising security concerns and creating a clunky experience. OAuth 2.0 flows offer a more secure and streamlined solution. This article explores the different OAuth flows and helps you choose the right one for your app.
If you wish to learn more about Apidog, try it out for free today by clicking the link below! 👇

What are OAuth 2.0 Flows?
The OAuth 2.0 defines a set of standardized procedures that are known as flows. OAuth 2.0 flows allow applications to obtain limited access to user accounts on an HTTP service by delegating user authentication to the service that holds the user accountant avoiding the need to share credentials directly between the application and service.
Key Entities Involved in OAuth 2.0 Flows
- Resource Owner (RO): This is the end-user. They are the one who owns the account data and grant access to their information on a particular platform. For instance, you might be the resource owner if you're granting a new app permission to access your photos on Facebook.
- Client (C): This is the application requesting access to the user's data. It could be a mobile app, a website, or even another backend service. The client doesn't directly store the user's credentials; instead, it relies on tokens obtained through the OAuth flow.
- Authorization Server (AS): This server is responsible for authenticating the resource owner (usually by prompting them to log in) and issuing access tokens. It acts as a trusted third party in the authorization process. The authorization server is typically controlled by the platform where the user account resides (e.g., Facebook, Google).
- Resource Server (RS): This server holds the protected resources that the client wants to access. These resources could be anything from a user's photo album to a list of contacts or even private documents. The resource server validates the access tokens issued by the authorization server before granting access to the requested resources.
Types of OAuth 2.0 Flows
Authorization Code Flow (Most Secure)
Steps
- A user interacts with the client application and initiates the authorization process.
- The client redirects the user to the authorization server's login page.
- The user logs in and grants access to the requested resources (scopes).
- The authorization server redirects the user back to the client with an authorization code.
- The client sends the authorization code and client credentials to the authorization server to request an access token and (optionally) a refresh token.
- The authorization server verifies the code and credentials, then issues access and refreshes tokens.
- The client finally uses the access token to access protected resources on the resource server.
Pros:
- Most secure flow due to separation of authorization code and access token exchange.
- Refresh tokens enable acquiring new access tokens without user re-authorization.
Cons:
- More complex flow with multiple redirects.
- Not ideal for native mobile apps due to limited browser interaction.
Important Factors to Consider When Choosing an OAuth 2.0 Flow
1. Security Requirements:
This is the top priority. Consider the sensitivity of the data your application needs to access.
- For high-security scenarios: Choose the Authorization Code Flow. It offers the best protection by keeping user credentials separate from the authorization code and access token exchange. Refresh tokens provide a secure way to get new access tokens without requiring the user to re-authorize every time.
- For less sensitive data: You might consider the Implicit Flow for its simplicity. However, be cautious, as access tokens are exposed in the URL fragment, making them less secure. This flow is not recommended for confidential data or long-lived access.
- Client Credentials Flow should only be used for machine-to-machine authorization with limited access needs, as it bypasses user involvement entirely.
2. Application Type:
The type of application you're building will influence the suitable flow.
- Web Applications: These typically have good browser interaction and can leverage the Authorization Code Flow effectively.
- Mobile Apps and Single-Page Applications (SPAs): Limited browser capabilities might make the Authorization Code Flow cumbersome. Consider the Implicit Flow for its simplicity, but be mindful of the security trade-offs. Hybrid approaches combining features of different flows can also be an option for mobile apps.
- Backend Services: Client Credentials Flow can be suitable for machine-to-machine communication between backend services.
3. User Interaction:
The level of user interaction available in your application will affect flow selection.
- Authorization Code Flow and Password Flow both require user interaction for authorization.
- Implicit Flow can function with minimal user interaction on the client side.
- Client Credentials Flow entirely bypasses user interaction as it assumes machine-to-machine communication.
4. Additional Considerations:
- Long-lived access: If your application needs extended access to user data, choose a flow that provides refresh tokens (Authorization Code Flow).
- Authorization Server Policies: Different authorization servers might have limitations or variations on the supported flows. Be sure to consult their documentation.
Apply OAuth 2.0 to Your API for Additional Security
Implementing a form of authentication is a basic need that every API should have, especially if the API is responsible for handling sensitive or private data. Therefore, developers need to have an API tool ready to build, modify, and document APIs. Luckily for you, there is already an API development tool that provides users with all of the functionalities mentioned previously - Apidog.


Setting Up API Authentication On Apidog

With Apidog, you can edit specific APIs' authentication methods. There are several choices for you to select from. To access this part of Apidog, you need to first:
- Select an API.
- Click the
Editheading. - Scroll down to the
Requestsection. - Click the
Authheader. - Finally, select which
Typeof authentication you like. If you wish to set up OAuth 2.0 authentication, then you can select that type.
Example of Using OAuth 2.0 with Apidog and Spotify API
Let's take a look at how we can apply the OAuth 2.0 authentication on the Spotify API by creating a new request!
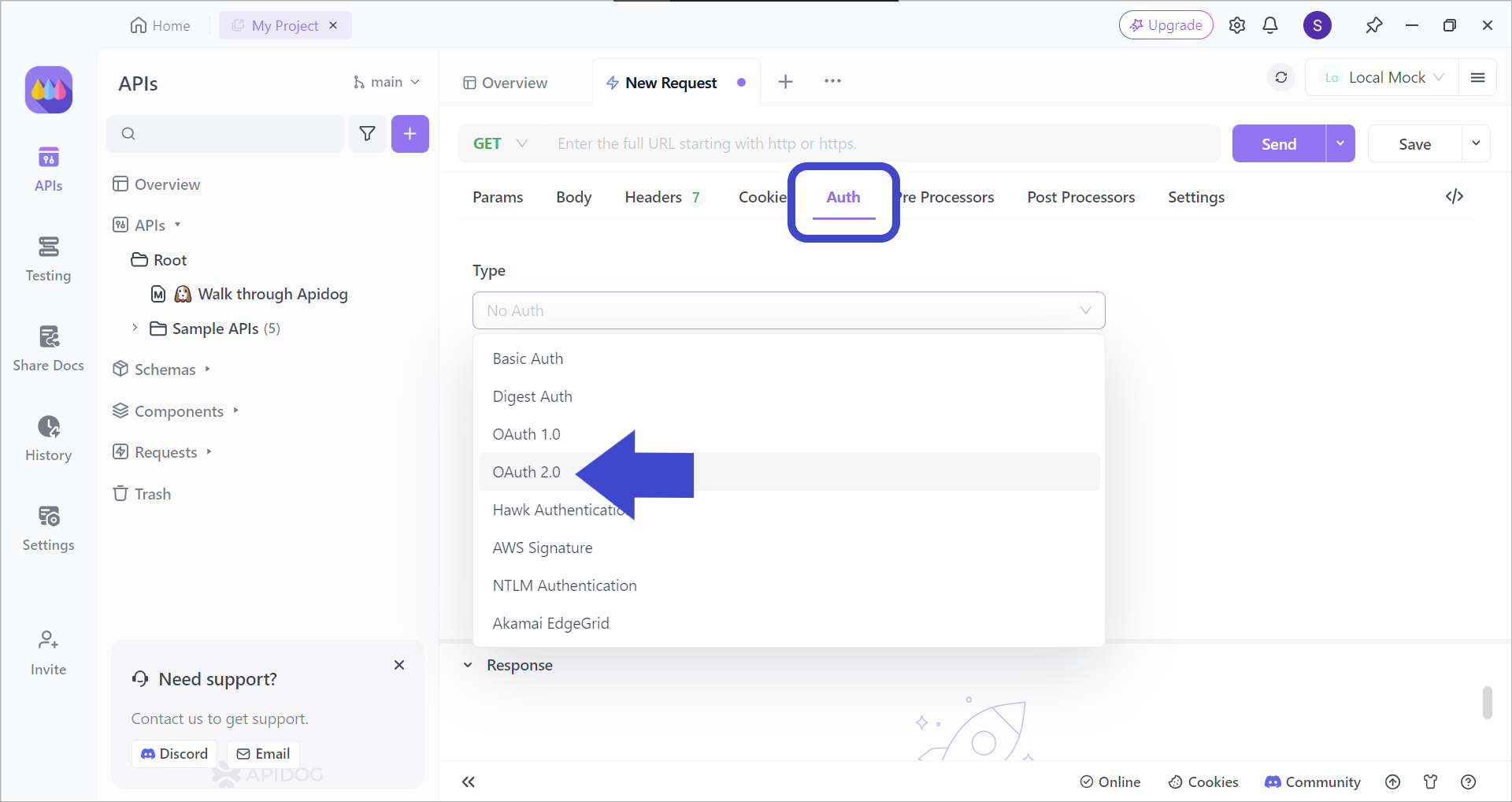
After creating a new request, pick the OAuth 2.0 authentication type, as seen in the image above.

Once you have chosen OAuth 2.0 as your authentication type, proceed by filling in the necessary details, proceed by completing the additional authentication steps that appear on the pop-up window. You should then be able to see your token on Apidog!

Testing API Endpoints Using Apidog
After every modification made during the API development stage, we need to ensure that the API still runs as intended. With Apidog, you can test each API's endpoint.
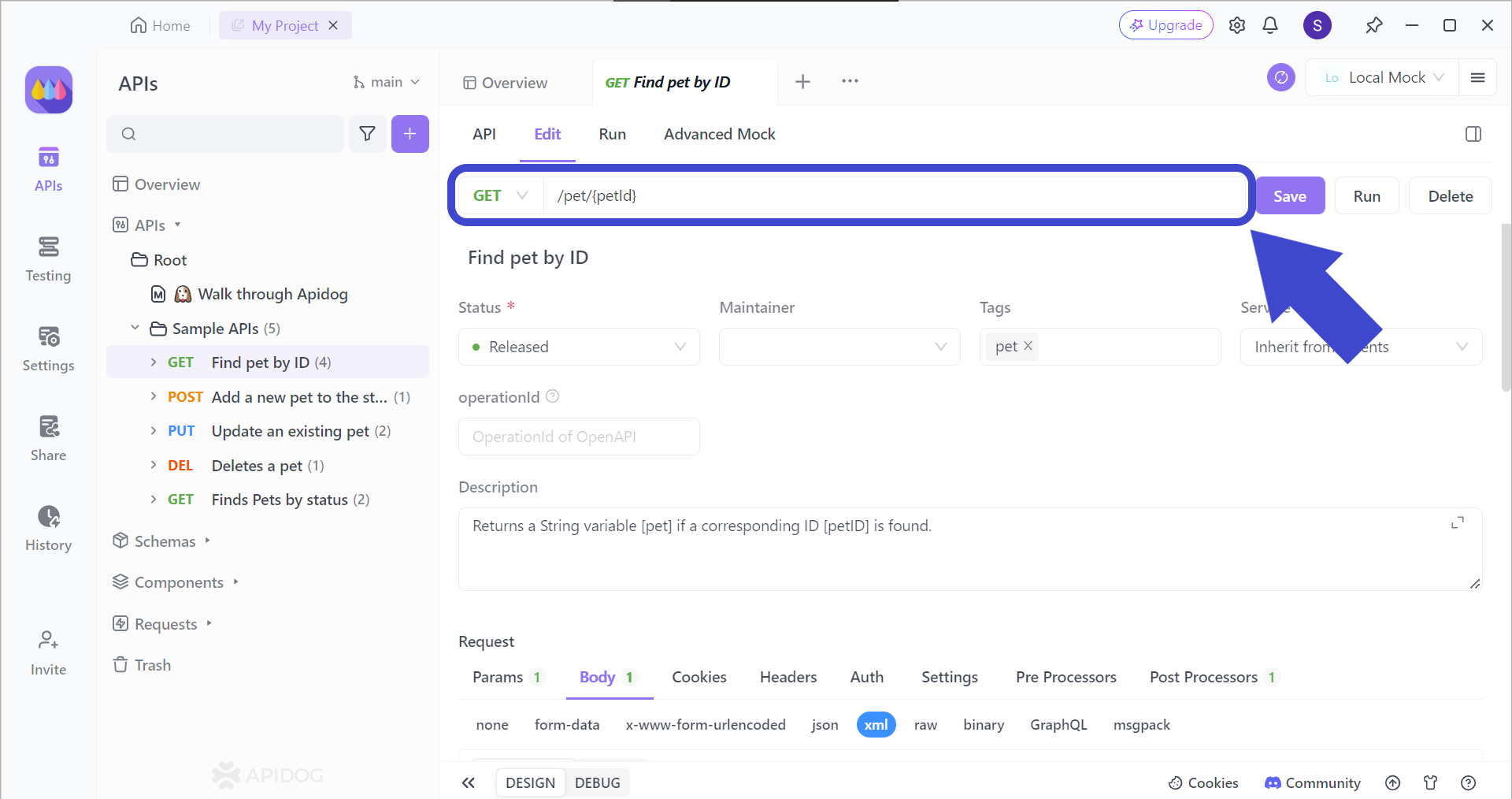
To target the correct API endpoint, you first have to insert the corresponding API endpoint that you want to test. Once you have included the intended API URL, include the parameters that you want to use for the endpoint (if relevant).
If you are still not quite confident about how to test an API endpoint, give this article a read!

Conclusion
OAuth 2.0 flows offer a secure and standardized approach to user authorization across different platforms. By understanding the various flows and their trade-offs, developers can choose the most suitable option for their application's needs. This ensures a balance between security, user experience, and application functionality.
If you are keen on using OAuth 2.0 and wish to implement its authentication for your applications or programs, you can always refer to the official OAuth 2.0 documentation and explore resources provided by popular authorization servers you plan to integrate with. These resources can provide more specific details and best practices tailored to their platform.




