OAuth 2.0 has emerged as a dominant protocol for secure authorization. This critical framework governs how applications access user data and resources on external platforms. A central component of OAuth 2.0 is the access token, acting as a digital key that unlocks specific API resources on a user's behalf.

Not only can you choose the authentication type for your API, but you can also build, test, mock, and document APIs with Apidog. To learn more about Apidog, click the button below!

Understanding how access tokens function is fundamental for developers seeking to build secure and robust applications that leverage external APIs.
What is OAuth 2.0?
OAuth 2.0 acts as a secure authorization layer, enabling third-party applications to access a user's resources on a server without requiring the user's credentials. It establishes a standardized method for users to grant controlled access to their data, eliminating the need to share their login information with other applications.

Definition of an Access Token
In the context of APIs (Application Programming Interfaces), an access token within the OAuth 2.0 framework can be formally defined as:
- A short-lived, opaque string: This implies the token does not contain human-readable information about its purpose or content.
- Issued by an Authorization Server: This server, distinct from the API itself, is responsible for verifying the legitimacy of access requests and issuing tokens upon successful authorization.
- Granting controlled access to specific API resources: The access token defines the scope of access, specifying which resources within the API the client application is authorized to interact with.
- Presented to the Resource Server: This server stores the protected resources and validates the access token before granting access to the requested resources.
- Associated with a specific resource owner and client: The token ties the access permission to a particular user and the application requesting access on their behalf.
- Having a defined lifespan: Access tokens are not permanent and typically expire shortly, requiring a refresh process to maintain ongoing access.
OAuth 2.0 Access Token's Functions
An OAuth 2.0 access token acts like a digital key granted to an application by an authorization server, after the user's consent. This token allows the application to access specific resources on the user's behalf on an API (Application Programming Interface) in a secure way. Here's why access tokens are important:
- Security: Access tokens eliminate the need for users to share their login credentials with applications. This reduces the risk of phishing attacks and unauthorized access to a user's data.
- Controlled Access: Access tokens can be granted with specific scopes, limiting the resources an application can access on a user's behalf. This ensures applications only have access to the data they need to function.
- Standardization: OAuth 2.0 is a widely adopted protocol, ensuring a consistent way for applications to request access to user data across different platforms.
In essence, access tokens provide a secure and controlled way for applications to interact with user data on APIs.
How to Obtain an OAuth 2.0 Access Token
Obtaining an OAuth 2.0 access token involves a multi-step flow between different parties defined in the protocol. Here's a simplified breakdown:
Client Registration: The application developer first registers their application with the authorization server of the API provider. This registration process establishes a trusted relationship and generates unique client credentials (client ID and client secret) used for authorization requests.
User Authorization: When a user interacts with the application and wants to grant access to their data on the API, the application redirects the user to the authorization server. This redirection typically includes the client ID, desired access scopes (specific resources the application needs), and a redirect URI (where the user will be returned after authorization).
Authorization Grant: On the authorization server, the user is presented with a consent screen outlining the requested access details. Upon user approval, the authorization server generates a temporary authorization code and redirects the user back to the predefined redirect URI within the application.
Token Request: The application receives the authorization code from the redirect URI and sends a token request back to the authorization server. This request typically includes the client ID, client secret (passed securely), and the authorization code received from the previous step.
Access Token Grant: The authorization server validates the request and, if successful, issues an access token and potentially a refresh token (used to obtain new access tokens when the original expires). The access token and any refresh token are returned to the application.
Important points to remember:
- The specific steps and details may vary slightly depending on the implementation of the OAuth 2.0 flow by the API provider.
- Security best practices are crucial throughout the process, especially regarding handling client secrets.
- This is a simplified overview, and there are different grant types within OAuth 2.0 suitable for various application scenarios.
Set Your API's Authentication with Apidog
Apidog is a comprehensive API development platform that provides users with a simple yet intuitive development environment for their API development processes.


Selecting OAuth 2.0 Authentication with Apidog
With Apidog's simple and intuitive user interface, you can easily choose OAuth 2.0 - or any other authentication type - in just a matter of seconds!
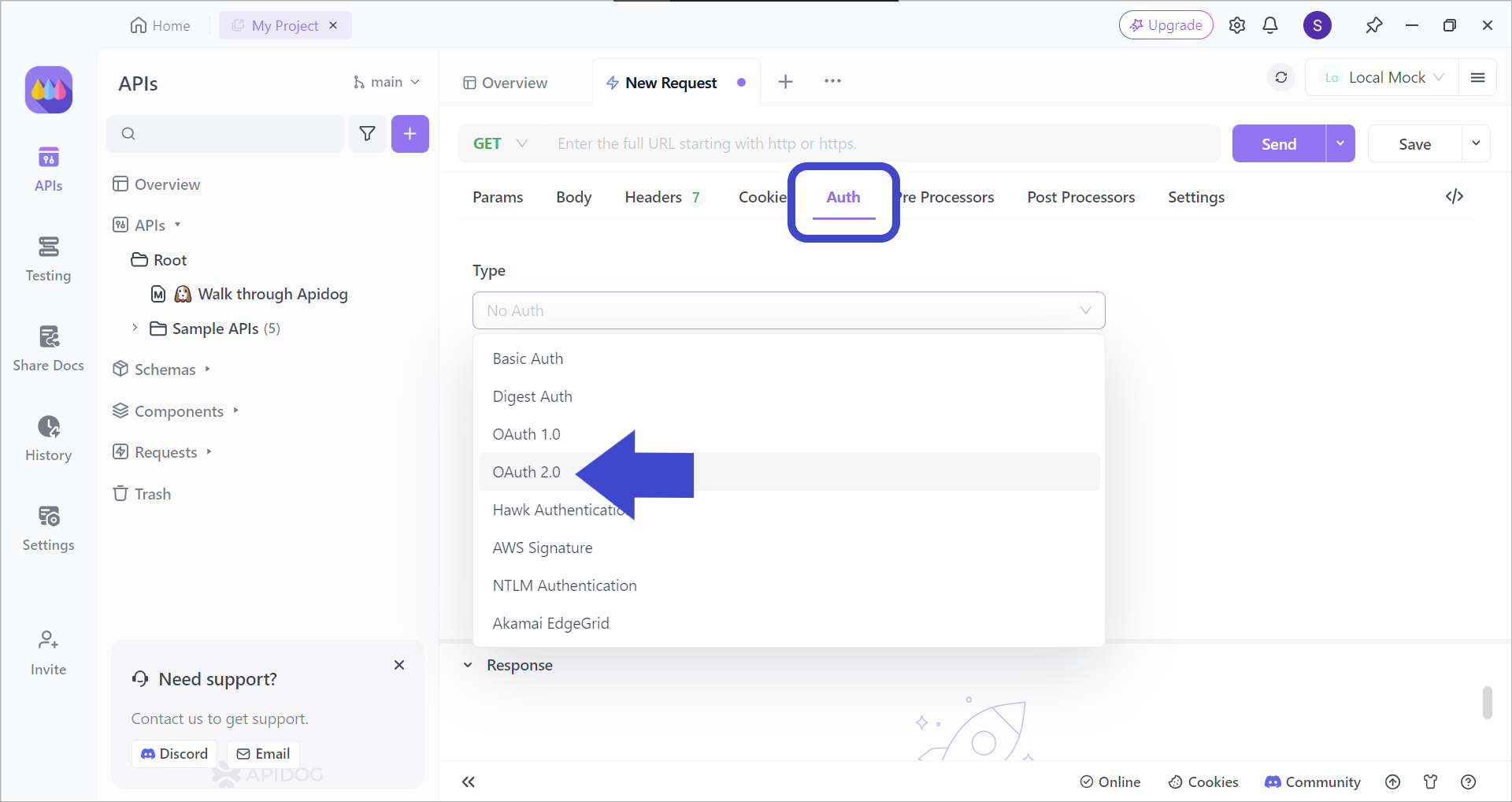
After creating a new request, pick the OAuth 2.0 authentication type, as seen in the image above. This will ensure that your APIs will have better security!
API Endpoints Testing With Apidog
Maintaining API functionality throughout development is crucial. Apidog empowers you to thoroughly test each endpoint within your API after every modification.
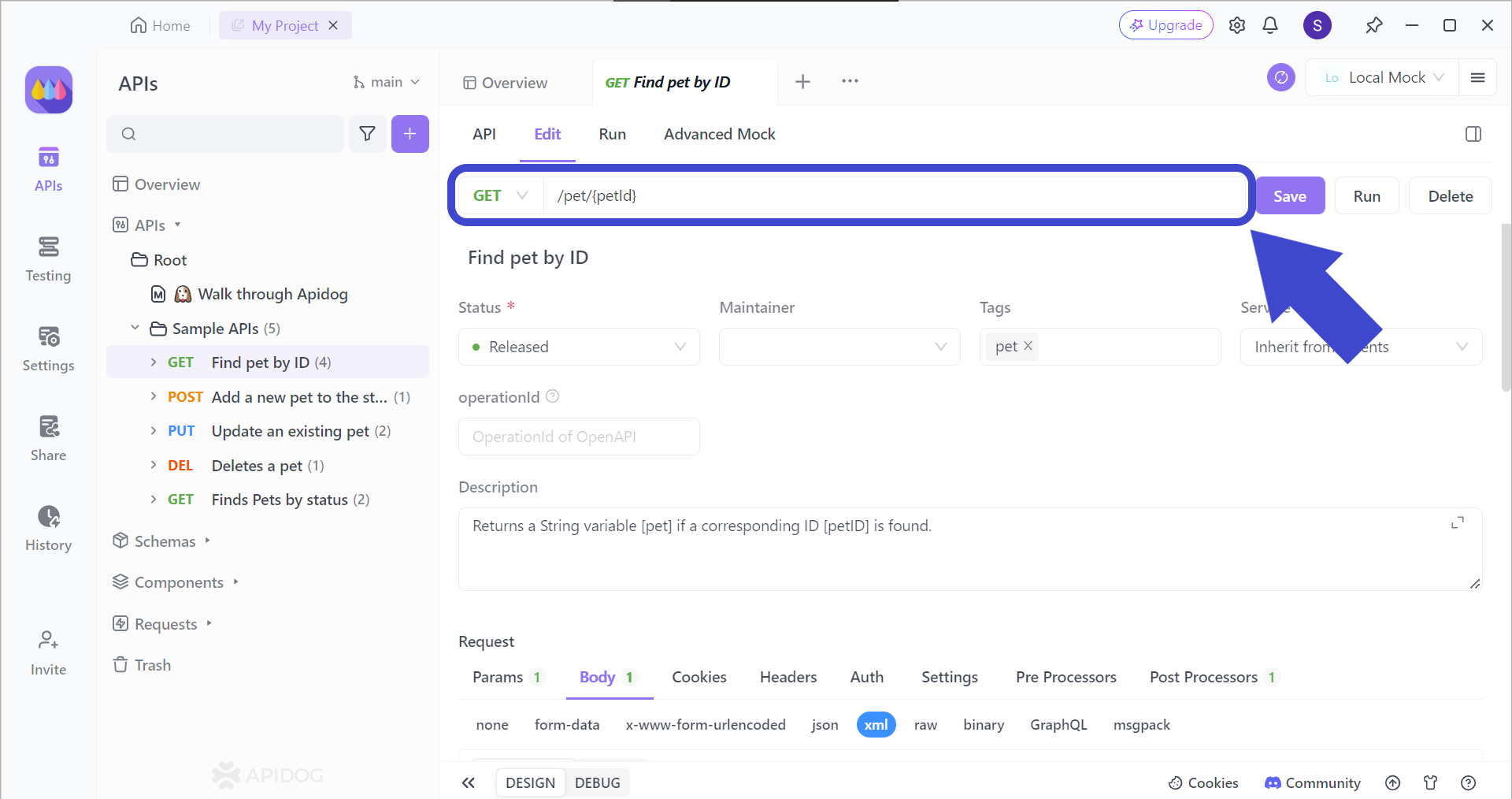
Initiating an API endpoint test requires specifying the target URL. Additionally, relevant parameters for the endpoint, if any, should be included. Also, for those unfamiliar with API endpoint testing, you can refer to this article which provides a comprehensive guide.

Conclusion
OAuth 2.0 access tokens have become the cornerstone of secure API authorization in the modern web landscape. By eliminating the need for shared user credentials, they offer a robust and standardized approach to granting controlled access to user data. This not only enhances security but also empowers users to manage how their data is accessed by third-party applications. As the development of APIs continues to flourish, understanding the role and functionality of access tokens remains paramount for developers seeking to build secure and user-centric applications that leverage the power of external APIs.
For developers venturing into the realm of OAuth 2.0, a plethora of resources are available to delve deeper into the intricacies of the various grant types and implementation details. By mastering this framework, developers can ensure their applications seamlessly interact with APIs while prioritizing the security and privacy of user data.




