In the age of interconnected applications, securely logging into one platform to access another's features has become essential. This is where OAuth steps in, acting as a middleman that facilitates secure authorization between different services. But with two versions - OAuth 1 and OAuth 2 - confusion can arise.

If you wish to apply OAuth 1 or OAuth 2 type authentication to your API, you can use Apidog, a comprehensive API tool that permits users to select the authentication type of their choice.
If you want to learn more about Apidog, come try the platform for free by clicking this button below!

This article delves into a vital comparison between these protocols, highlighting their key differences, strengths, and ideal use cases, to help you understand which reigns supreme in the modern authentication landscape.
What is OAuth 1?
OAuth 1 (defined by the OAuth Core 1.0 specification), is a protocol made for authorization delegation. It permits a resource owner (also called a user) to grant a consumer (also called an application) limited access to their protected resources hosted on a service provider (better known as a website or platform) without revealing their private credentials to the consumer.
Main Benefits Gained from Using OAuth 1
- Improved User Experience: OAuth 1 allowed users to conveniently access features of one platform (consumer) using their existing account on another platform (service provider). This eliminated the need to create separate accounts for each application.
- Enhanced Security: By separating user credentials from the authorization process, OAuth 1 reduced the risk of exposing passwords or other sensitive information to the requesting application. Users are only granted access to specific data within a defined scope, further improving control.
- Standardized Approach: OAuth 1 provided a standardized protocol for authorization, simplifying development for both applications and service providers. This interoperability fostered a more connected web ecosystem.
What is OAuth 2?
OAuth 2 has the same definition as OAuth 1, where it is an authorization framework that enables a third-party application (known as a client) to obtain limited access to an HTTP service (also called as a resource server) on behalf of a resource owner (user), all without exposing the user's credentials.
Main Benefits Gained from Using OAuth 2
OAuth 2.0 has become the dominant protocol for authorization due to several key benefits it offers over its predecessor, OAuth 1.0:
- Simplicity: OAuth 2.0 streamlines the authorization flow compared to OAuth 1.0. It utilizes various grant types depending on the application scenario, making it more flexible and easier to implement.
- Enhanced Security: OAuth 2.0 eliminates the need for shared secrets between the client and resource server, a potential vulnerability in OAuth 1.0. It relies on access tokens with limited lifespans and refresh tokens for extended access, improving overall security.
- Improved Scalability: Managing numerous client applications becomes easier with OAuth 2.0. The use of public/private key cryptography and access tokens eliminates the need for complex shared secret management.
- Flexibility: OAuth 2.0 offers a wider range of grant types catering to different application types. This includes authorization code grants (popular for web applications), password grants (suitable for mobile apps), and client credentials grants (used for server-to-server communication).
- Mobile-Friendliness: OAuth 2.0 is well-suited for mobile applications with its focus on secure token-based access. This allows users to conveniently access features across platforms without re-entering credentials on their mobile devices.
- Wider Adoption: Due to its advantages, OAuth 2.0 has gained wider adoption by major service providers like Google, Facebook, and Twitter. This simplifies integration for developers and provides a consistent user experience across different platforms.
Reasons Behind the Creation of OAuth 2
OAuth 2.0 was created to address the limitations and complexities of its predecessor, OAuth 1.0. Here's a breakdown of the key reasons for its development:
- Complexity: OAuth 1.0's multi-step flow with temporary tokens and shared secrets made it cumbersome to implement and manage, especially for developers.
- Scalability: Maintaining numerous shared secrets for various client applications became a challenge for service providers as the web ecosystem grew.
- Security Concerns: Reliance on shared secrets could be a vulnerability if compromised. Additionally, OAuth 1.0 token exposure posed security risks.

OAuth 2.0 aimed to streamline the authorization process while enhancing security and scalability. Here's how it addressed these issues:
- Simplified Flow: OAuth 2.0 utilizes different grant types depending on the application scenario, reducing complexity and making it more adaptable.
- Eliminated Shared Secrets: By relying on access tokens and public/private key cryptography, OAuth 2.0 removed the need for shared secrets, improving overall security.
- Improved Token Management: Access tokens with limited lifespans and refresh tokens for extended access provided a more secure and manageable approach.
Tabulated Summary of OAuth 1 VS. OAuth 2
| Feature | OAuth 1.0 | OAuth 2.0 |
|---|---|---|
| Authorization Flow | Complex, multi-step with temporary tokens | Simpler, various grant types depending on scenario |
| Security | Relies on shared secrets (potential vulnerability) | Eliminates shared secrets, uses access tokens with limited lifespan and refresh tokens |
| Scalability | Challenging to manage numerous shared secrets | More scalable with public/private key cryptography |
| Flexibility | Limited grant types | Wider range of grant types for different applications |
| Mobile-Friendliness | Less suitable for mobile apps | Well-suited for mobile apps with token-based access |
| Adoption | Less widespread adoption | Wider adoption by major service providers |
| Focus | Secure access with complex handshake | Streamlined, secure, and flexible authorization |
| Ideal Use Cases | Legacy applications requiring complex access control | Modern web and mobile applications, wider range of scenarios |
Apidog - Providing Users the Freedom to Choose Authentication Type For Your API
API tools usually have limitations on what they can provide API developers. However, Apidog, an all-in-one API development tool, can provide users with the option to select OAuth 1, OAuth 2, or other authentication types - whichever the developer desires!


Creating an API from Scratch with Apidog
Creating APIs with Apidog has never been easier! With Apidog and your ideas, you can produce APIs in a matter of clicks!
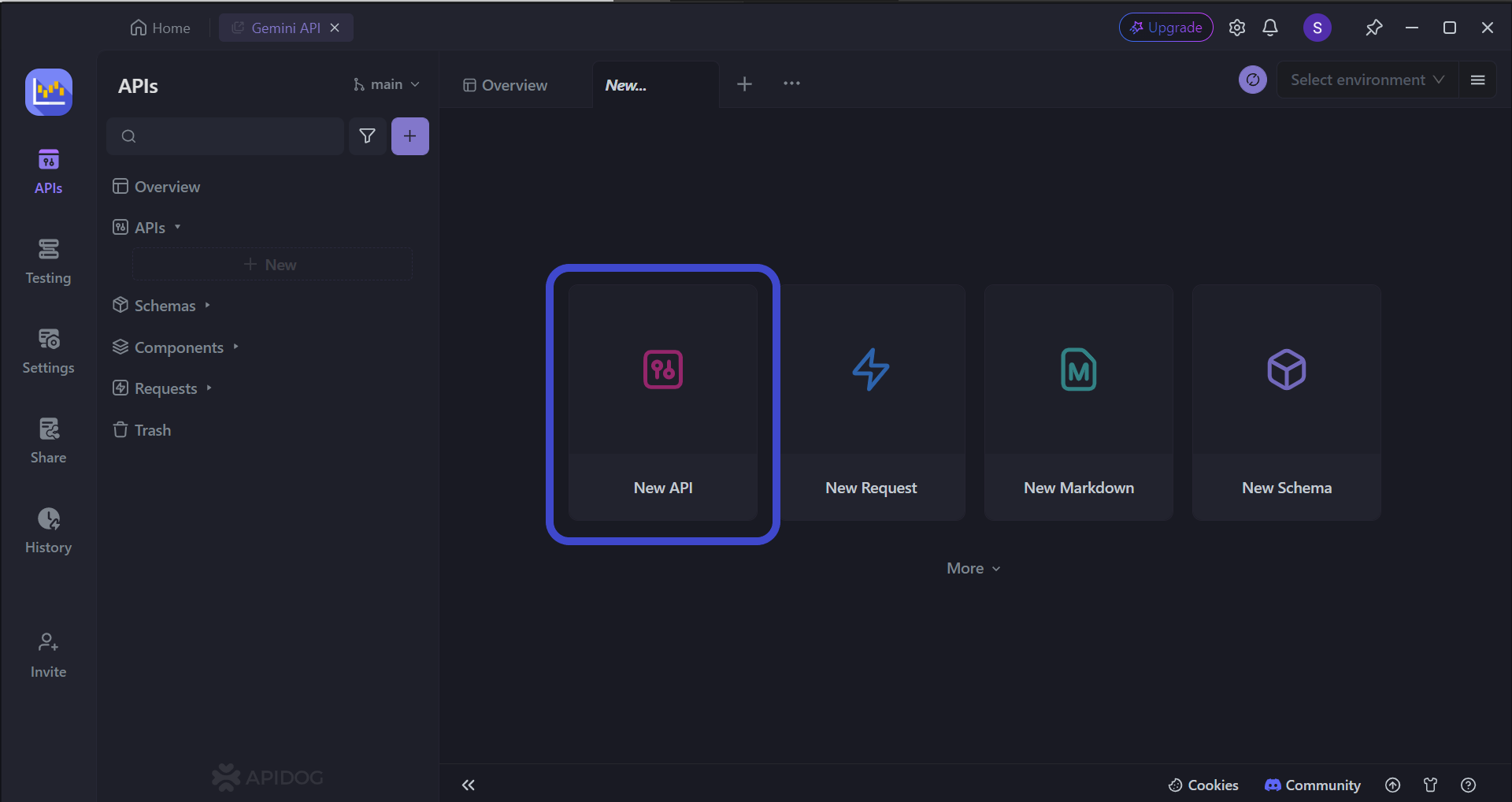
Begin by pressing the New API button, as shown in the image above.
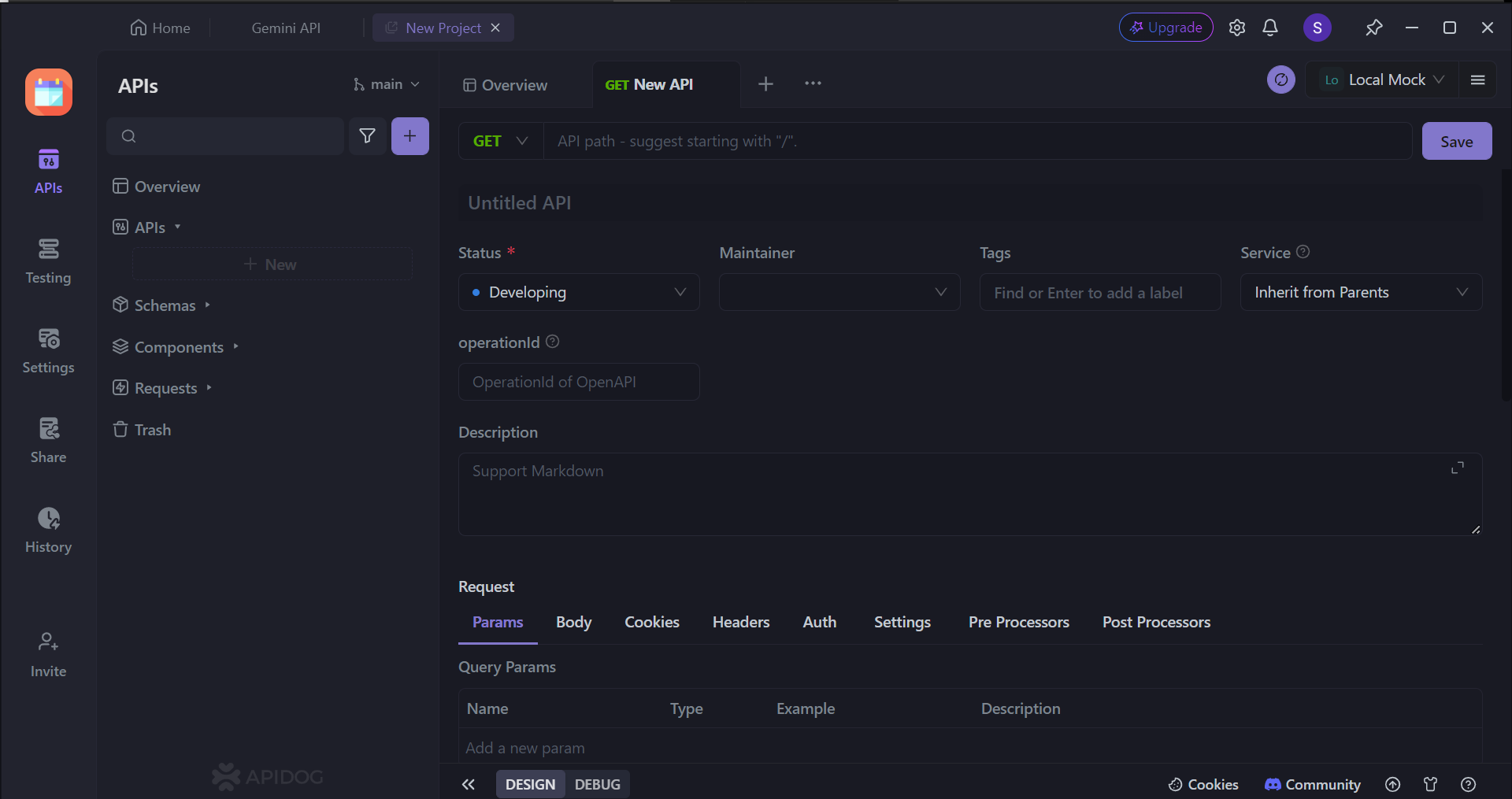
Next, you can select many of the API's characteristics. On this page, you can:
- Set the HTTP method (GET, POST, PUT, or DELETE)
- Set the API URL (or API endpoint) for client-server interaction
- Include one/multiple parameters to be passed in the API URL
- Provide a description of what functionality the API aims to provide.
To provide some assistance in creating APIs in case this is your first time creating one, you may consider reading these articles to understand the best practices for making REST APIs (or APIs in general):


Setting Up API Authentication On Apidog
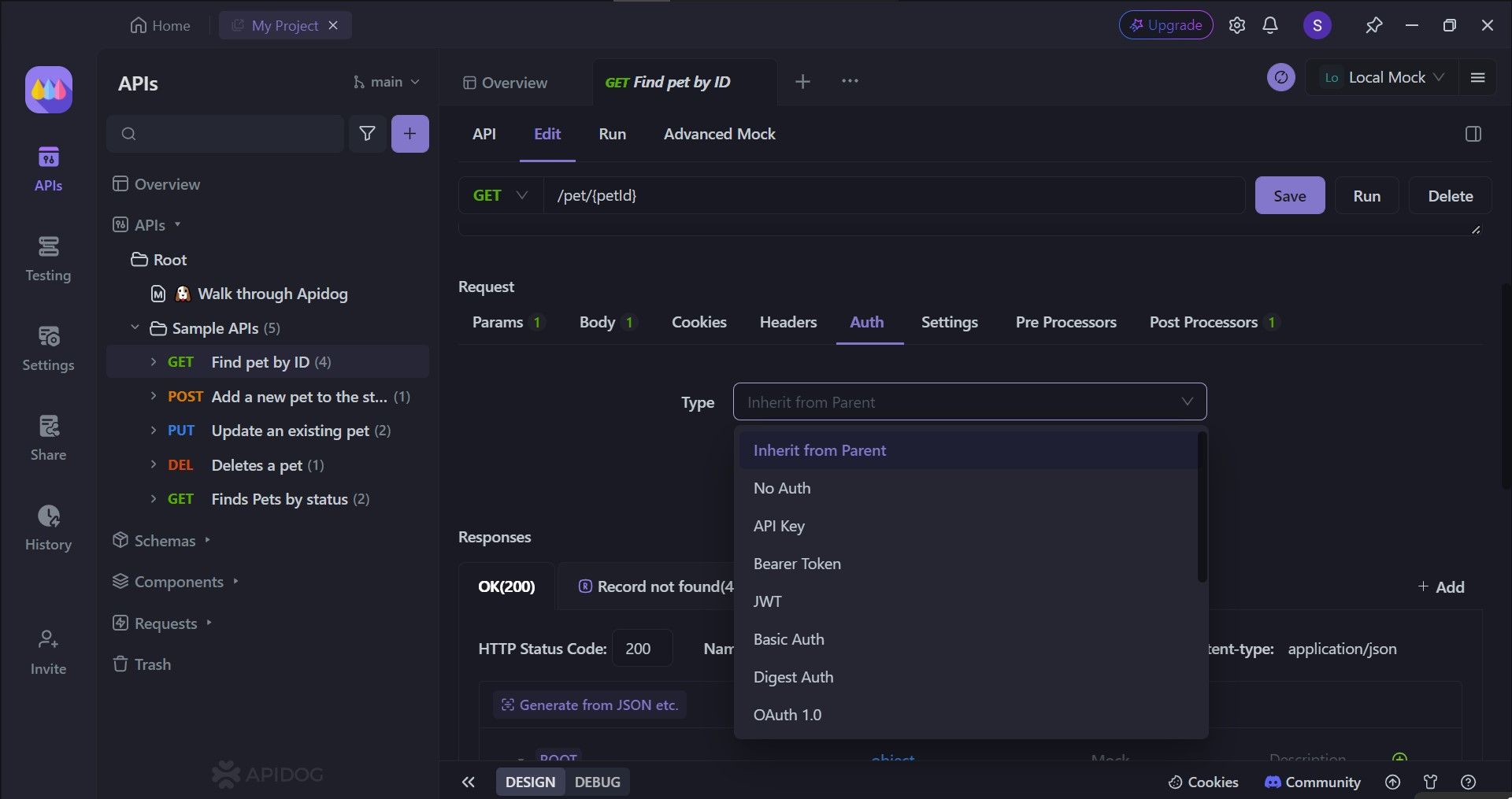
With Apidog, you can edit specific APIs' authentication methods. There are several choices for you to select from. To access this part of Apidog, you need to first:
- Select an API.
- Click the
Editheading. - Scroll down to the
Requestsection. - Click the
Authheader. - Finally, select which
Typeof authentication you like.
Conclusion
while OAuth 1.0 paved the way for secure authorization, its complexity and reliance on shared secrets limited its scalability and user experience. OAuth 2.0 emerged as a more streamlined and secure solution, addressing these shortcomings.
With its simplified flow, a wider range of grant types, and focus on token-based access, OAuth 2.0 caters perfectly to the needs of modern web and mobile applications. Its wider adoption by major service providers further solidifies its position as the dominant protocol for secure and convenient user authorization in today's interconnected digital world.
Together with Apidog, you can effortlessly select the proper authentication type for your API. Ensure that your API has the proper security to promote consumer trust!




