In the digital age, secure authentication mechanisms are paramount for protecting sensitive information and ensuring that only authorized users can access systems and data. Kerberos, a network authentication protocol, stands out as a robust solution widely adopted by enterprises to enhance security in distributed computing environments. Originally developed by the Massachusetts Institute of Technology (MIT) in the 1980s, Kerberos has become a standard in securing interactions within client-server architecture, particularly in environments like Windows, Linux, and Unix.
This blog delves into the core concepts, functionality, and applications of Kerberos authentication, highlighting why it remains a critical component in modern cybersecurity.
What is Kerberos Authentication?
Kerberos is an authentication protocol that uses secret-key cryptography to provide secure authentication for client-server applications. Named after the mythological three-headed dog that guards the gates of the underworld, Kerberos is designed to protect network services from unauthorized access while ensuring the integrity and confidentiality of data.
Kerberos operates on the basis of tickets, which allow users to prove their identity to services in a network without transmitting passwords over the network. This ticket-based system reduces the risk of password interception by malicious actors.
How Does Kerberos Authentication Work?
Kerberos authentication involves a series of steps that ensure secure communication between the client, the server, and a trusted third-party entity known as the Key Distribution Center (KDC). The KDC is a critical component of the Kerberos protocol and is composed of two main services: the Authentication Server (AS) and the Ticket Granting Server (TGS).
Here’s a simplified overview of the Kerberos authentication process:
Initial Authentication Request:
- The client sends a request to the AS, requesting access to a service.
- The AS verifies the client’s credentials (typically a username and password).
- If the credentials are valid, the AS issues a Ticket Granting Ticket (TGT), encrypted with the client’s secret key, and a session key. The TGT is used to request access to various services without needing to authenticate repeatedly.
Service Request:
- The client uses the TGT to request a service ticket from the TGS.
- The TGS validates the TGT and issues a service ticket, which the client can use to authenticate to the specific service.
Service Access:
- The client presents the service ticket to the desired service.
- The service verifies the ticket and grants the client access.
This process minimizes the need for repeatedly transmitting sensitive information, such as passwords, across the network, thus enhancing security.
Key Features of Kerberos Authentication
Kerberos authentication offers several features that make it a preferred choice for secure network authentication:
- Mutual Authentication: Both the client and the server authenticate each other, ensuring that both parties are legitimate.
- Ticket-Based System: The use of tickets reduces the need for transmitting passwords over the network, lowering the risk of interception.
- Single Sign-On (SSO): Users authenticate once with the AS, and can then access multiple services without re-entering credentials, improving user experience and security.
- Time-Based Tickets: Kerberos tickets have a limited lifespan, reducing the risk of replay attacks.
- Encryption: All communication between the client, server, and KDC is encrypted, protecting against eavesdropping and tampering.
Applications of Kerberos Authentication
Kerberos is widely used in various environments due to its robust security features and scalability. Some common applications include:
- Enterprise Networks: Kerberos is often integrated with Active Directory in Windows environments to manage authentication across large enterprise networks.
- UNIX/Linux Systems: Many UNIX and Linux distributions include Kerberos as a standard authentication mechanism.
- Email Systems: Kerberos can be used to secure email servers, ensuring that only authenticated users can access their mail.
- Web Services: Some web applications use Kerberos to authenticate users securely, especially in enterprise environments.
Advantages and Limitations of Kerberos Authentication
While Kerberos offers significant security advantages, it is essential to understand its limitations to make informed decisions about its deployment.
Advantages:
- Enhanced Security: Kerberos' use of encryption and mutual authentication provides strong protection against unauthorized access.
- Scalability: Kerberos can handle authentication for large networks with thousands of users.
- Interoperability: Kerberos is compatible with multiple operating systems, making it versatile in mixed environments.
Limitations:
- Complexity: Setting up and maintaining a Kerberos environment can be complex and requires a thorough understanding of its components.
- Dependency on Time Synchronization: Kerberos relies on accurate time synchronization between the client, server, and KDC, as tickets have time-based validity.
- Single Point of Failure: The KDC is a critical component; if it fails, the entire authentication system can be compromised.
Attaching Kerberos Authentication to API Requests with Apidog
Apidog now supports Kerberos Authentication, enabling secure network authentication for API requests, particularly in enterprise environments. To activate this feature, ensure your system has valid Kerberos credentials—whether on Windows, macOS, or Linux. This feature is exclusive to the Apidog client and requires the configuration of the Service Principal Name (SPN) in the format HTTP/hostname.domain.local@realm.name.
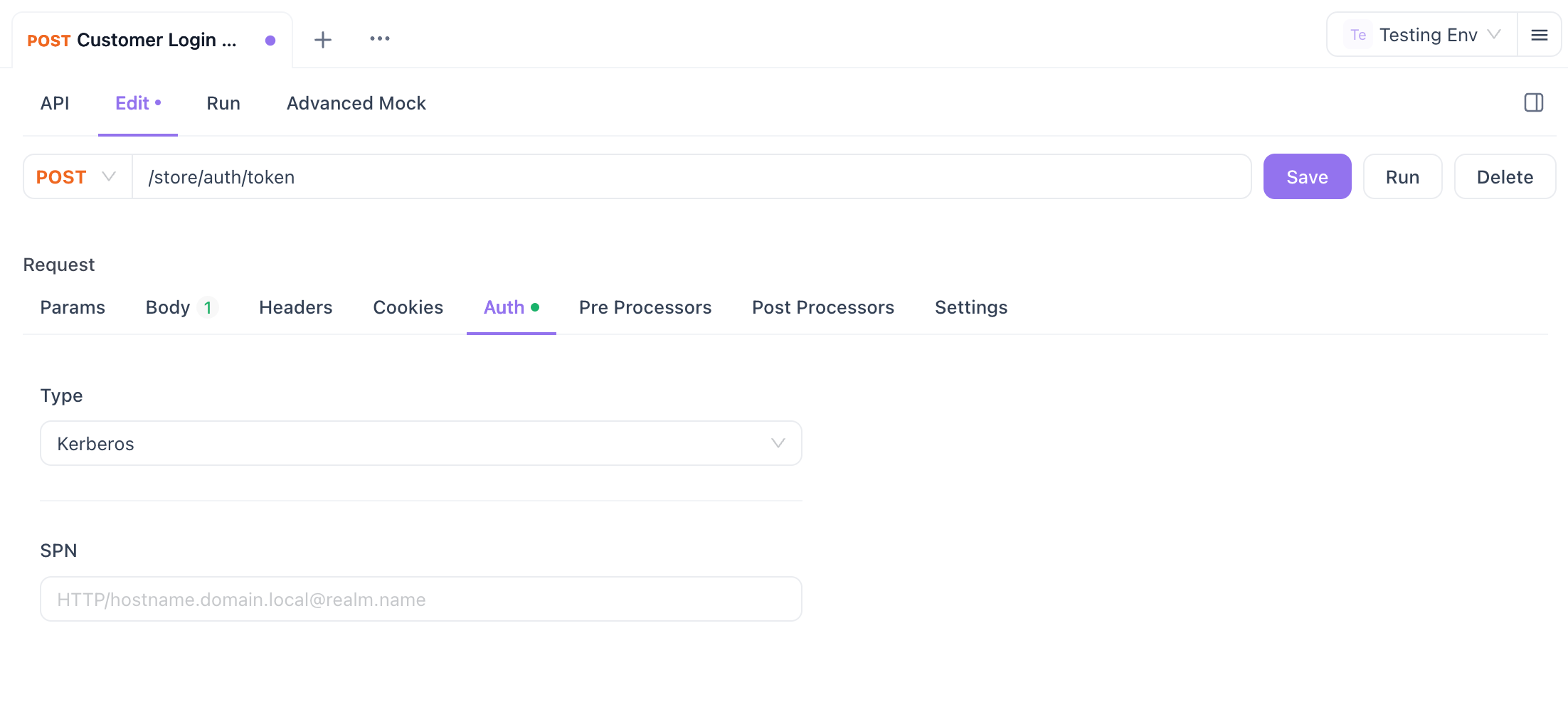
To use this feature, navigate to the Auth tap on the API request panel, choose Kerberos Authentication and enter the SPN:

Once configured, Apidog will handle authentication seamlessly, offering enhanced security for your API workflows.
Conclusion
Kerberos authentication remains a cornerstone of secure network authentication, especially in enterprise environments where security and scalability are paramount. By leveraging a ticket-based system, mutual authentication, and encryption, Kerberos offers a robust solution to the challenges of protecting sensitive information in a distributed computing environment. While it has its complexities and limitations, when implemented correctly, Kerberos can significantly enhance the security posture of an organization.
Understanding how Kerberos works and its applications can empower IT professionals to design and maintain more secure and reliable authentication systems, ensuring that only authorized users gain access to critical resources. As cyber threats continue to evolve, the importance of strong authentication mechanisms like Kerberos cannot be overstated.
FAQs
1. What is Kerberos, and how does it function?
Kerberos is a network authentication protocol designed to provide secure authentication in distributed computing environments. It operates using a trusted third-party system known as the Key Distribution Center (KDC) to verify both clients and servers. The KDC issues tickets that authenticate the identities of clients and servers, enabling secure communication and blocking unauthorized access.
2. Can you provide an example of a Kerberos application?
A prominent example of a Kerberos application is the authentication system utilized by Microsoft Active Directory. In Windows domains, Kerberos serves as the foundational protocol for authentication, ensuring secure access to network resources and services for users.
3. What are the advantages of using Kerberos?
Here are some key benefits of implementing Kerberos for authentication:
- Enhanced Security: Kerberos employs encryption and mutual authentication to protect the integrity and confidentiality of authentication exchanges.
- Single Sign-On (SSO): After initial authentication, users can access multiple services and resources without re-entering their credentials, which boosts convenience and productivity.
- Centralized Authentication: Kerberos centralizes the authentication process, minimizing the need for individual credential management across different services and systems.
- Scalability: Kerberos is capable of supporting large-scale environments, efficiently managing authentication for a significant number of users and services.
4. What distinguishes Kerberos from KDC?
Kerberos refers to the authentication protocol itself, while KDC stands for Key Distribution Center. The KDC is a centralized server that implements the Kerberos protocol and consists of two primary components: the Authentication Server (AS) and the Ticket-Granting Server (TGS). The AS handles initial authentication and issues Ticket-Granting Tickets (TGTs), while the TGS provides service tickets for accessing specific services. In essence, Kerberos is the protocol, and the KDC is the server that operates that protocol.