Are you confused about JWT and Bearer tokens? Don’t worry; you’re not alone! In the world of APIs and secure communication, these terms often come up. However, understanding their differences and knowing when to use each can be tricky. In this blog post, we will break down JWT and Bearer tokens in a simple, conversational tone. By the end, you’ll be well-versed in the “JWT vs. Bearer token” debate.
What are Tokens and Why Do We Need Them?
In the simplest terms, a token is a piece of data used to authenticate and authorize users. Imagine you are at a concert. To get in, you need a ticket. Similarly, to access an API, you need a token. Tokens ensure that only authorized users can access certain resources, adding an essential layer of security.
But wait, aren’t there different types of tokens? Yes, indeed! Among them, JWT (JSON Web Tokens) and Bearer tokens are the most popular. Understanding the nuances between them can help you choose the right one for your needs.
JWT (JSON Web Tokens)
What is a JWT?
JWT stands for JSON Web Token. It’s a compact, URL-safe means of representing claims to be transferred between two parties. This is especially useful in the context of APIs where you need to secure data transmission between a client and a server.
How Does a JWT Work?
A JWT consists of three parts:
- Header: Contains metadata about the token, such as the type of token and the algorithm used for signing it.
- Payload: Contains the claims. Claims are statements about an entity (typically, the user) and additional data.
- Signature: This is used to verify that the sender of the JWT is who it says it is and to ensure that the message wasn’t changed along the way.
When a client sends a request to a server, it includes the JWT in the request header. The server then verifies the token and, if valid, processes the request. If the token is invalid or expired, the server rejects the request.
Benefits of Using JWT
- Compact: Being small in size, JWTs are perfect for being passed around in URLs, HTTP headers, or inside cookies.
- Self-contained: JWTs carry all the information needed for authentication, which means no need to query the database multiple times.
- Scalable: Ideal for modern web applications where scalability is crucial.
Drawbacks of JWT
- No Token Revocation: Once a JWT is issued, it cannot be revoked easily until it expires.
- Payload Size: As the payload increases, the size of the token also increases, which can affect performance.
Bearer Tokens
What is a Bearer Token?
A Bearer token is a security token. With a Bearer token, the party in possession of the token (the “bearer”) is given access to the resource without further identification. Essentially, “If you have it, you can use it.”
How Does a Bearer Token Work?
Bearer tokens are typically generated by an authentication server and passed to the client. The client then includes the token in the HTTP Authorization header when making requests to access protected resources.
Unlike JWTs, Bearer tokens do not have a standardized structure. They are opaque to clients, meaning that clients should not attempt to decode or interpret them.
Benefits of Using Bearer Tokens
- Simplicity: Easy to implement and use.
- Flexibility: Can be used with various authentication mechanisms.
- Secure: Since the token is opaque, clients cannot tamper with its content.
Drawbacks of Bearer Tokens
- Stateless: Without additional infrastructure, tokens cannot be revoked.
- Lack of Standardization: Bearer tokens do not have a standardized format, which can lead to inconsistency.

JWT vs. Bearer Token: Key Differences
Structure and Information
- JWT: Structured with three parts (header, payload, signature) and carries information within the token itself.
- Bearer Token: Opaque and doesn’t contain information about the user or claims.
Usability
- JWT: Can be used for both authentication and information exchange. Ideal for stateless sessions.
- Bearer Token: Primarily used for authentication. Suitable for simpler use cases where token revocation is not a concern.
Security
- JWT: Offers strong security with its signature, but once issued, it cannot be revoked easily.
- Bearer Token: Simpler but requires additional mechanisms for revocation and management.

When to Use JWT vs. Bearer Token
Deciding whether to use a JWT or Bearer token depends on your specific use case:
Use JWT if:
- You need a self-contained token that can carry information between parties.
- You require a token that is compact and can be passed around easily.
- You need a token that can be verified without querying a database.
Use Bearer Token if:
- You need a simple authentication mechanism.
- You prefer opaque tokens for security reasons.
- You have infrastructure in place to manage token revocation.
Best Practices for Using Tokens
Regardless of whether you choose JWT or Bearer tokens, here are some best practices to follow:
- Secure Transmission: Always use HTTPS to ensure tokens are transmitted securely.
- Token Expiry: Implement token expiration to reduce the risk of token theft.
- Revocation: Develop a strategy for token revocation, especially if using long-lived tokens.
- Storage: Store tokens securely. Avoid local storage if possible; consider using HTTP-only cookies.
Introducing Apidog: Your API Management Companion
Managing tokens, especially in a complex API ecosystem, can be challenging. That’s where Apidog comes in. Apidog is a powerful tool designed to help you manage your APIs efficiently. Whether you are working with JWT, Bearer tokens, or any other type of token, Apidog provides robust features to simplify your workflow.
JWT in Apidog
Apidog is a user-friendly API development and testing tool that excels in managing JSON Web Tokens (JWT). With its intuitive interface, Apidog simplifies the process of handling JWTs, providing automatic support for token generation, dynamic management, and seamless inclusion in API requests.

This tool streamlines the JWT-related aspects of API development, allowing developers to focus on efficient testing and integration within their workflows.
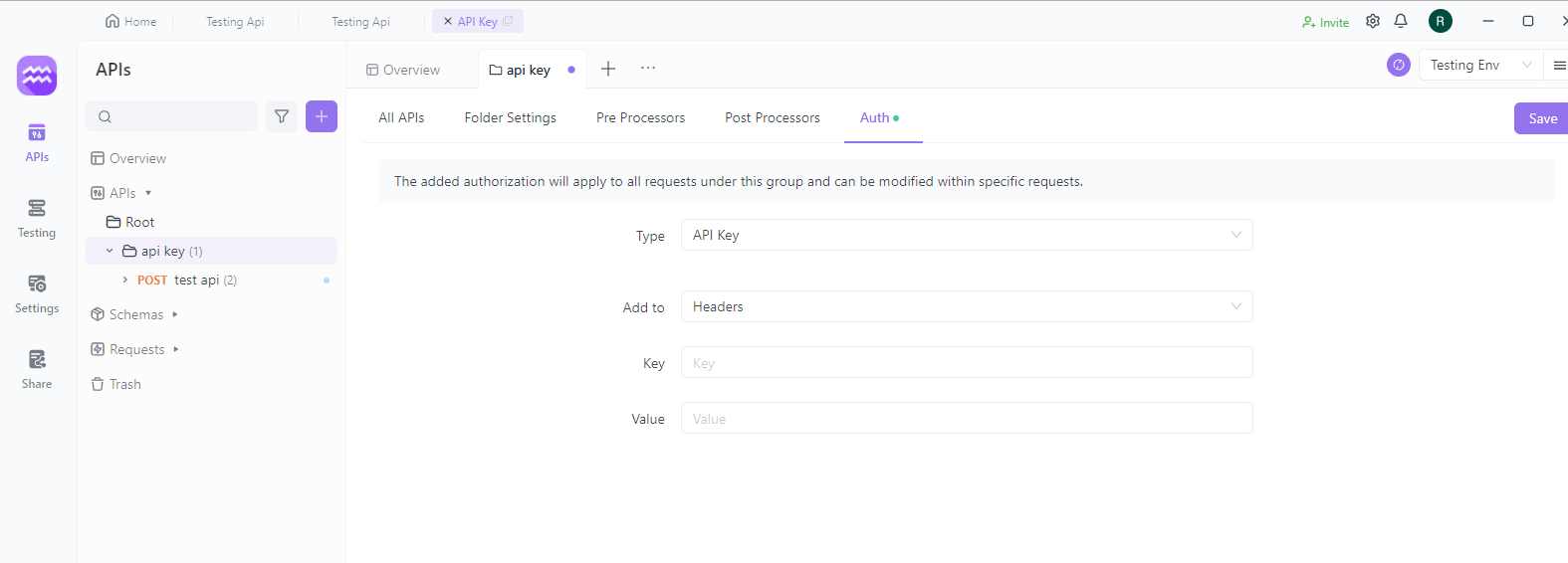
How to Authenticate Bearer Token in Apidog
When unit testing an API in Apidog, the Bearer Token authentication method is very simple.
Open an existing API in Apidog, switch to "Debug" mode, select "Request" > "Auth", specify the type as "Bearer Token", and enter the Token in the input box at the bottom to submit.
It's important to note that bearer tokens should be kept secure and not shared unnecessarily. They should also be periodically rotated or revoked as required for security purposes.
Conclusion
Understanding the differences between JWT and Bearer tokens is crucial for securing your APIs effectively. JWTs offer a structured, self-contained way to transmit information, while Bearer tokens provide a simple and flexible authentication method. Depending on your needs, you can choose the token type that best fits your application.
By following best practices and leveraging tools like Apidog, you can ensure that your API remains secure and efficient. So, go ahead and explore the world of tokens with confidence!