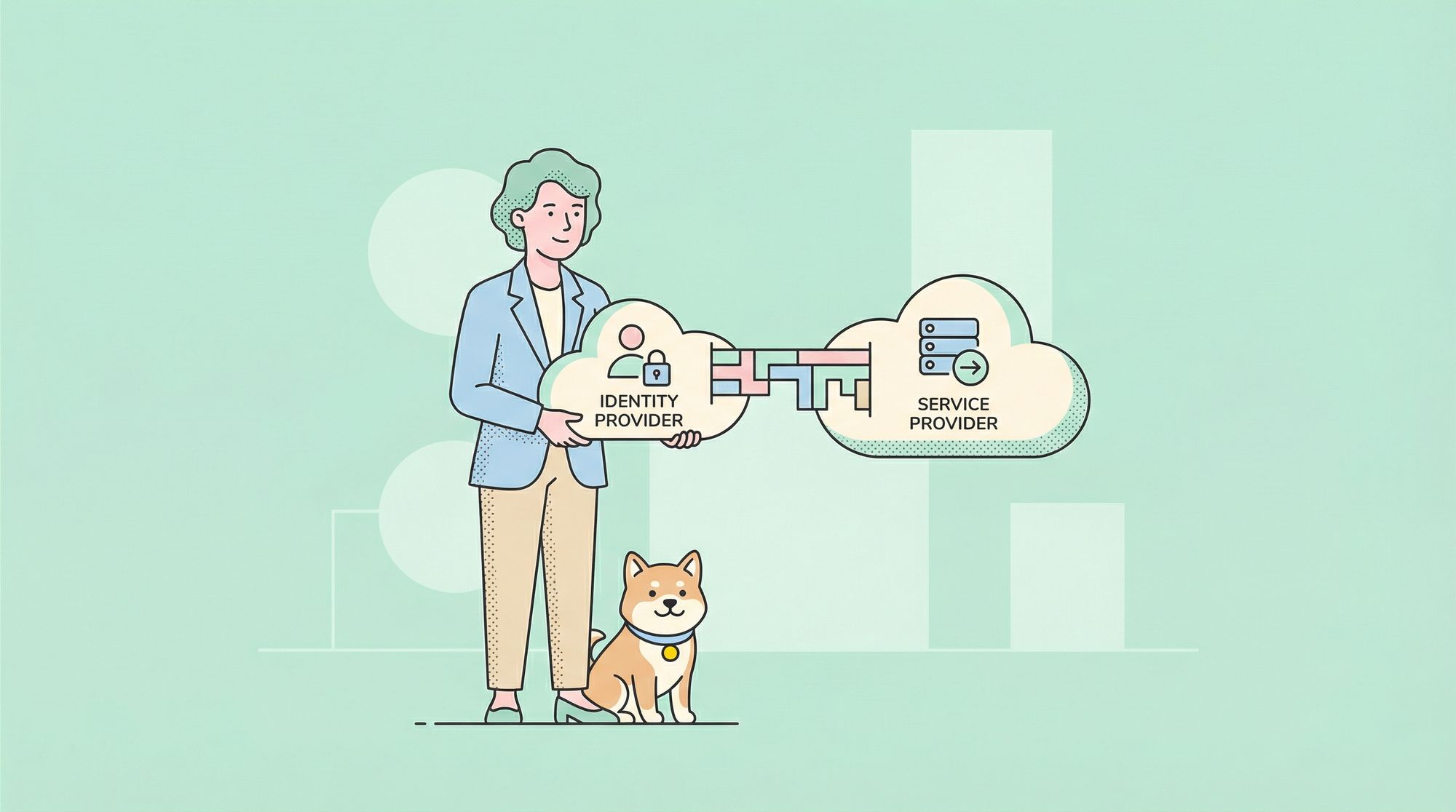
In the rapidly evolving world of digital identity management, a System for Cross-domain Identity Management (SCIM) has emerged as a critical standard. SCIM provides a unified and streamlined approach to managing user identities and access permissions across multiple platforms. By automating the creation, updating, and deletion of user accounts, SCIM reduces the workload on IT departments and enhances security and compliance measures. This article offers a comprehensive guide on how businesses can implement SCIM to optimize their identity management processes.
Introduction to SCIM Implementation
SCIM is a protocol designed to simplify identity management by enabling secure, automated, and scalable user account provisioning and de-provisioning. It serves as a bridge between identity providers (IdP) and service providers, ensuring that user data is consistently synchronized across all applications and services. The implementation of SCIM is becoming increasingly important for organizations that rely on multiple SaaS applications and need to maintain robust security protocols.
Why Implement SCIM?
- Automates Identity Management: SCIM reduces manual effort by automating user lifecycle management.
- Enhances Security: By ensuring consistent access control, SCIM minimizes security risks.
- Improves Compliance: SCIM helps organizations meet regulatory requirements by providing a standardized approach to identity management.
- Scalability: SCIM supports the needs of growing businesses by efficiently managing large numbers of user accounts.
Preparing Your System for SCIM Integration
Before diving into the SCIM implementation process, proper preparation is crucial. A successful SCIM integration requires a clear understanding of your organization’s current identity management landscape, as well as a plan to adapt to SCIM standards.
Assessing Current Identity Management Systems
- Identify Existing Solutions: Evaluate the current identity and access management (IAM) solutions in use. Determine if your organization is using a custom-built system or a commercially available solution.
- Evaluate Compatibility: Ensure that existing systems and applications support SCIM or can be configured to do so. Many modern IAM solutions come with SCIM support, but older or custom solutions may require additional configurations.
- Map User Data: Analyze how user data is stored and structured within your organization. Understanding user attributes and data formats is essential for mapping them to SCIM standards.
Setting Goals and Objectives
- Define Objectives: Clearly outline the goals of implementing SCIM. This could range from reducing IT workload to improving security and compliance.
- Identify Stakeholders: Engage stakeholders, including IT teams, security officers, and compliance managers, to ensure that all relevant parties are aligned with the objectives of the SCIM implementation.
- Develop a Roadmap: Create a step-by-step plan that outlines the key stages of the SCIM implementation process, including timelines and resource allocation.
Key Steps in Setting Up SCIM
Implementing SCIM involves several crucial steps. Each stage must be executed carefully to ensure a smooth integration process.
Step 1: Select a SCIM-Compatible Identity Provider
- Choose the Right IdP: Select an identity provider that supports SCIM. Popular choices include Okta, Azure AD, and Google Identity. These providers offer built-in SCIM support, making integration more straightforward.
- Evaluate Features: Ensure that the chosen IdP provides robust SCIM features, including support for user provisioning, de-provisioning, and synchronization.
Step 2: Configure SCIM Endpoints
- Define Endpoints: Establish SCIM endpoints that will facilitate communication between the identity provider and service providers. These endpoints will handle requests for creating, updating, and deleting user accounts.
- Secure Endpoints: Implement security measures such as OAuth tokens and HTTPS to protect SCIM endpoints from unauthorized access.
Step 3: Map User Attributes
- Identify User Attributes: Determine which user attributes need to be managed through SCIM. Common attributes include username, email, first name, last name, and department.
- Attribute Mapping: Map these attributes to the SCIM schema. This mapping ensures that user data is accurately synchronized across all platforms.
Step 4: Implement SCIM Provisioning
- Set Up Provisioning Rules: Define rules for when and how user accounts should be provisioned or de-provisioned. For example, create rules for automatically deactivating user accounts when employees leave the organization.
- Test Provisioning: Conduct thorough testing to verify that provisioning and de-provisioning actions are executed correctly. Test different scenarios to ensure that all edge cases are covered.
Step 5: Monitor and Maintain SCIM Integration
- Continuous Monitoring: Regularly monitor SCIM logs and activity to identify potential issues. Monitoring helps in maintaining the health of the SCIM implementation.
- Updates and Maintenance: Keep SCIM configurations up to date with the latest standards and security patches. Regular maintenance ensures that the SCIM implementation remains secure and efficient.
Apidog Supports SCIM
Apidog, a leading API management, documentation and testing platform, fully supports SCIM, making it easier for organizations to integrate robust identity management into their workflows. By leveraging Apidog’s SCIM capabilities, businesses can seamlessly manage user provisioning, de-provisioning, and synchronization across all connected applications.
Apidog offers a user-friendly interface for configuring SCIM endpoints and mapping user attributes, ensuring smooth and secure data exchange. With Apidog, organizations benefit from automated identity processes, reducing manual effort and enhancing overall security.

By incorporating SCIM support, Apidog not only simplifies identity management but also helps organizations maintain compliance with industry standards, making it an ideal choice for businesses looking to streamline their API and identity management solutions.
Common Challenges and How to Overcome Them
Implementing SCIM can present several challenges. Being aware of these common pitfalls and knowing how to address them can lead to a more successful deployment.
Challenge 1: Compatibility Issues
- Problem: Not all applications and systems may support SCIM out-of-the-box.
- Solution: Choose SCIM-compliant applications or consider developing custom connectors for legacy systems. Working closely with vendors to understand their SCIM compatibility can also help mitigate compatibility issues.
Challenge 2: Data Consistency and Synchronization
- Problem: Ensuring consistent and accurate data synchronization across multiple systems can be challenging.
- Solution: Regularly audit user data to identify inconsistencies. Utilize automated synchronization features and monitor SCIM logs to detect and resolve synchronization issues promptly.
Challenge 3: Security Concerns
- Problem: Exposing SCIM endpoints can create security vulnerabilities if not managed correctly.
- Solution: Implement robust security measures, including OAuth tokens, HTTPS encryption, and regular security audits. Use role-based access controls to limit access to SCIM endpoints.
Best Practices for SCIM Implementation
Following best practices can ensure a smooth and effective SCIM implementation. These practices not only streamline the process but also enhance security and reliability.
Establish Clear Governance
- Develop SCIM Policies: Create policies that define how SCIM will be used within the organization. These policies should outline procedures for user provisioning, de-provisioning, and data synchronization.
- Assign Roles and Responsibilities: Clearly define the roles and responsibilities of team members involved in SCIM implementation and management. This ensures accountability and clarity.
Conduct Regular Audits
- Audit User Data: Regularly audit user data to ensure accuracy and compliance with SCIM standards. Identify and resolve discrepancies promptly.
- Review SCIM Logs: Monitor SCIM activity logs for any unusual behavior or errors. Regular reviews help in early detection of potential issues.
Train IT Staff and End-Users
- IT Training: Provide training to IT staff on SCIM implementation and management. Ensure they are familiar with SCIM protocols, endpoint security, and troubleshooting techniques.
- User Awareness: Educate end-users about the importance of accurate data and secure practices. This awareness helps maintain the integrity of the SCIM system.
Conclusion: Ensuring Successful SCIM Deployment
Implementing SCIM can significantly improve identity management within an organization by automating user account provisioning and enhancing security. By carefully preparing for integration, following a structured implementation process, and adhering to best practices, businesses can ensure a successful SCIM deployment. Continuous monitoring, regular audits, and stakeholder engagement are key to maintaining the effectiveness of SCIM over time.
In summary, SCIM provides a scalable and efficient solution for managing user identities across multiple platforms. It simplifies the process, reduces IT workload, enhances security, and ensures compliance with industry standards. For organizations looking to streamline their identity management processes, SCIM is a critical tool that offers significant benefits.
Implementing SCIM may seem complex, but with careful planning and execution, businesses can reap the rewards of a more efficient and secure identity management system.