Many applications rely on APIs (Application Programming Interfaces) to exchange data and functionality. But with this convenience comes the responsibility of securing these interactions. Two critical concepts in API security are authentication and authorization, which often get confused. This article will explain the subtle differences between these two processes, ensuring you can distinguish the two concepts from one another.
To ensure that your APIs do have the necessary security, you should consider Apidog, an all-in-one API development tool that provides users a platform to select what type of authentication and security the developer desires.
If you are interested in knowing more about Apidog, try it today for free by clicking on the button below!

What is API Authentication?
API authentication is the security process of verifying the identity of a user or application attempting to access an API. This verification process typically involves confirming the user's or application's credentials against a trusted source, such as a username/password combination, an API key, or a security token issued by an authorization server.
The primary objective of API authentication is to ensure that only authorized users or applications can access the API's resources. It acts as the first layer of security, establishing who is trying to interact with the API.

Process of API Authentication
1. Request with Credentials: When an application or user wants to access the API, they initiate a request. This request includes authentication credentials that verify their identity. These credentials come in various forms depending on the chosen method:
- API Keys: Unique identifiers assigned to applications for API access. Simple to implement, but requires careful management to prevent misuse.
- Tokens: Short-lived credentials generated after successful login (e.g., OAuth). More secure than API keys due to expiration time limits.
- Username/Password: Traditional method used for user authentication. Requires secure password storage and might be less convenient for application-to-application communication.
2. Verification by API: The API receives the request and puts the provided credentials through a verification process:
API Keys/Tokens: The API validates if the key/token is:
- Valid (exists in the system)
- Not expired (hasn't exceeded its lifespan)
- Belongs to a recognized application or user
Username/Password: The API checks if the username and password match a registered user in its database. This might involve secure password hashing techniques to protect user credentials.
Granting or Denying Access:
- Success: If the credentials pass verification, the API grants access to the requested resources within the API. This could involve allowing data retrieval, manipulation, or triggering specific functionalities.
- Failure: If the credentials are invalid (e.g., wrong key/token, incorrect username/password), access is denied. The API typically returns an error message explaining the issue.
Advantages of API Authentication
Improved Security
The primary benefit of API authentication lies in its ability to fortify the overall security posture of an API. It acts as a vigilant gatekeeper, meticulously scrutinizing every access attempt. Only authorized applications and users wielding valid credentials are granted access, while any unauthorized attempts are resolutely thwarted.
This significantly diminishes the risk of data breaches, where malicious actors attempt to steal, manipulate, or tamper with sensitive information. By implementing a robust authentication mechanism, organizations can establish a secure environment for data exchange, fostering trust with users and stakeholders.
Improved Accountability and Traceability
API authentication meticulously chronicles access attempts, meticulously logging who is accessing the API and at what precise time. This granular data stream furnishes organizations with invaluable insights for activity monitoring. Potential security threats can be swiftly identified and addressed by analyzing these logs. Furthermore, API authentication fosters accountability among users and applications.
If any unauthorized actions are attempted, the logs provide an audit trail, pinpointing the source of the issue and enabling prompt corrective measures. This not only safeguards data but also deters unauthorized access attempts, as users are aware that their actions are being monitored.
Improved User Trust
The implementation of a robust API authentication mechanism communicates a crystal-clear message – user data security is a top priority. By employing rigorous verification procedures, organizations demonstrate their unwavering commitment to protecting user information.
This instills confidence in users, assuring them that their data is shielded behind a secure authentication layer. Consequently, user satisfaction and loyalty are likely to flourish, as users feel secure in interacting with the API.
Improved Data Privacy
Numerous industries operate within the purview of stringent data privacy regulations. These regulations often mandate the enforcement of robust security measures to safeguard user data. API authentication plays a pivotal role in ensuring compliance with these regulations.
By meticulously verifying user identities and access attempts, organizations can demonstrate their adherence to data privacy requirements, mitigating potential legal ramifications and fostering trust with regulatory bodies.
Examples of API Authentication
1. API Keys:
- Function: Simple credentials, often resembling long strings of characters, assigned to authorized applications. These keys act as unique identifiers that applications present when requesting access to an API.
Benefits:
- Simplicity: Easy to implement and manage for a limited number of applications.
- Stateless: Don't require maintaining session information on the API server, reducing server load.
Drawbacks:
- Security Concerns: API keys are susceptible to compromise if not handled carefully. If a key is leaked, unauthorized access can occur.
- Limited Control: Difficult to revoke access for a compromised key. You would need to regenerate and distribute new keys to all authorized applications.
- Example: A weather monitoring service might provide API keys to registered developers who want to incorporate live weather data into their mobile applications.
2. Tokens:
- Function: Short-lived credentials generated after successful user authentication (often through protocols like OAuth). These tokens act as temporary substitutes for usernames and passwords, enhancing security.
Benefits:
- Enhanced Security: Expires after a predetermined timeframe, mitigating the risk of unauthorized access even if a token is compromised.
- Granular Control: Access levels can be associated with tokens, allowing for more fine-grained control over what users can do within the API.
Drawbacks:
- Increased Complexity: Implementing token-based authentication can be more complex than using API keys.
- State Management: Requires managing token expiration and potential refresh mechanisms on both the API server and client application.
- Example: A social media platform might utilize tokens to grant access to a user's profile information after a successful login. The token would expire after a set period of inactivity, requiring the user to re-authenticate before accessing the information again.
3. Username and Password:
- Function: Traditional authentication method where users provide a username and password to access the API.
Benefits:
- Familiarity: Users are already accustomed to using usernames and passwords for various online services.
Drawbacks:
- Security Concerns: Prone to brute-force attacks or credential leaks if not implemented securely (e.g., weak password hashing).
- Less Suitable for Machine-to-Machine Communication: Not ideal for scenarios where applications need to interact with the API without human intervention.
- Example: An internal corporate API used by employees might leverage username and password authentication for access control. However, for public-facing APIs, token-based methods are often preferred.
What is API Authorization?
API authorization is the security process of verifying what level of access a previously authenticated user of an application has to specific resources or functionalities within an API.
API authorization process enforces access control policies that determine the permitted actions (such as reading, writing, updating, and deleting) a user or application can perform on specific data or functionalities exposed by the API.

Process of API Authorization
1. Access Request:
- A user or application initiates a request to access the API. This request typically involves an HTTP verb (GET, POST, PUT, DELETE) specifying the desired action and a URL pointing to the specific API resource.
2. Authentication Check (Optional):
- In some cases, authorization might be preceded by an authentication step. This verifies the identity of the user or application making the request. Common methods include API keys, username/password combinations, or tokens issued by an authorization server (e.g., OAuth).
- Note: Not all authorization schemes require separate authentication. Some methods, like API keys, inherently handle both identity verification and access control.
3. Authorization Policy Evaluation:
- Once the user or application is identified (or if authentication is not required), the API authorization layer kicks in.
- The API server retrieves the relevant access control policy associated with the requested resource or functionality. These policies define permitted actions for different user roles or applications.
- The retrieved policy is then evaluated against the user's or application's attributes. These attributes can include:
- User Roles: (e.g., admin, editor, reader)
- Permissions: Specific actions allowed on the resource (e.g., read, write, update, delete)
- Contextual Factors: (e.g., location, device type, time of access)
4. Access Decision:
- Based on the policy evaluation, the API server makes an authorization decision. This decision determines whether to grant or deny access to the requested resource or functionality.
- Grant Access: If the user's or application's attributes match the permitted actions within the policy, access is granted.
- Deny Access: If a mismatch occurs, access is denied, and the user or application receives an error message (e.g., "Unauthorized" or "Forbidden").
5. Resource Access (or Error Response):
- Depending on the authorization decision:
- Access Granted: The user or application receives the requested data or is allowed to perform the desired action on the API resource.
- Access Denied: The user or application receives an error message indicating they lack the necessary permissions.
Additional Considerations:
- Authorization Tokens: In some authorization schemes (e.g., OAuth), access tokens are issued after successful authentication. These tokens encapsulate the user's or application's permissions and are included in subsequent API requests for authorization checks.
- Fine-grained Access Control: Advanced authorization methods like Attribute-Based Access Control (ABAC) allow for highly granular control over access decisions by considering various user and request attributes.
Key Benefits of API Authorization
Enhanced Security:
- Restricts Unauthorized Access: The primary benefit is blocking unauthorized users or applications from accessing sensitive data or functionalities within your API. This mitigates risks like data breaches, unauthorized modifications, and denial-of-service attacks.
- Granular Control: Authorization allows you to define access permissions on a very specific level. You can control what actions different users or applications can perform on specific resources. For example, an editor might be allowed to update blog posts, while a reader can only view them.
Improved User Trust:
- Data Protection: Robust authorization demonstrates your commitment to protecting user data. Users feel more confident in using your API knowing their information is only accessible to authorized individuals.
- Transparency: Clear and defined access control policies provide transparency to users regarding what data they can access and what actions they can perform.
Increased Efficiency and Scalability:
- Reduced Risk of Errors: By restricting unauthorized access, you minimize the chances of accidental data modifications or deletions by unauthorized users.
- Simplified Management: Authorization policies can be applied to groups of users with similar roles, streamlining permission management for large user bases.
Additional Advantages:
- Compliance: Certain industries have strict data privacy regulations. Implementing API authorization can help you adhere to compliance requirements.
- Improved Debugging: Authorization logs track access attempts, making it easier to identify suspicious activity or troubleshoot permission-related issues.
Real-world Examples of API Authorization
E-commerce Platform:
- Scenario: A mobile shopping app integrates with an e-commerce store's API to display product information and allow users to add items to their carts.
- Authorization: The API uses API key authorization. The mobile app provides a unique API key with each request. The e-commerce platform's server verifies the key against a list of authorized applications before granting access to product data.
- Additional Considerations: For adding items to the cart (a modifying action), the authorization might require an additional access token obtained through user login within the mobile app.
Social Media App:
- Scenario: A social media app utilizes an API to post updates and photos on behalf of users.
- Authorization: The API leverages OAuth 2.0, a popular authorization framework. The user logs in to the social media app, which then redirects them to the social media platform's authorization server. There, the user grants the app permission to post on their behalf. The authorization server issues an access token that the social media app uses for subsequent API calls to post content.
- Benefits: OAuth provides a secure way for users to grant access without sharing their actual login credentials with the social media app.
Banking Application:
Scenario: A mobile banking app interacts with a bank's API to view account balances and transfer funds.
Authorization: The API likely employs a combination of methods.
- Basic Authentication: During login within the mobile app, the user provides their username and password. These credentials are used for basic authentication against the bank's system.
- Access Tokens: Upon successful login, the bank's system might issue an access token with an expiration time. The mobile app includes this token in subsequent API requests for authorization checks on specific actions (e.g., viewing balance vs. transferring funds).
Security Focus: For financial institutions, robust API authorization is critical to safeguard sensitive user data and prevent unauthorized transactions.
Tabulated Differences Between API Authentication VS. Authorization
| Feature | API Authentication | API Authorization |
|---|---|---|
| Purpose | Verifies the identity of a user or application trying to access an API. | Determines what level of access a previously authenticated user or application has to specific resources or functionalities within an API. |
| Focus | "Who are you?" | "What are you allowed to do?" |
| Process | User/application provides credentials (username/password, API key, token), and API server verifies credentials against a trusted source. | Access control policies define permitted actions for different user roles or applications, and user/application attributes (roles, permissions, context) are evaluated against these policies. |
| Outcome | Grants access to the authorization stage (if successful). | Grants or denies access to specific resources or functionalities within the API. |
| Example Methods | Username/password combinations, and API keys - Security tokens issued by an authorization server (e.g., OAuth) | Roles-Based Access Control (RBAC), Attribute-Based Access Control (ABAC), and API keys (can sometimes handle both authentication and authorization) |
| Relationship | Often precedes authorization | Works in conjunction with authentication (not always required) |
Apidog - Enforce Your API's Security with API Authentication and Authorization!
Setting up adequate security for your API is often a commonly overlooked aspect of API development. However, providing proper security to ensure that the API and the consumer's information are safe is essential. This is why you need to select and use an API tool like Apidog.


Setting Up API Authentication On Apidog

With Apidog, you can edit specific APIs' authentication methods. There are several choices for you to select from. To access this part of Apidog, you need to first:
- Select an API.
- Click the
Editheading. - Scroll down to the
Requestsection. - Click the
Authheader. - Finally, select which
Typeof authentication you like.
Testing API Endpoints Using Apidog
To ensure that the APIs you have developed run smoothly, you can test their endpoints individually with Apidog!
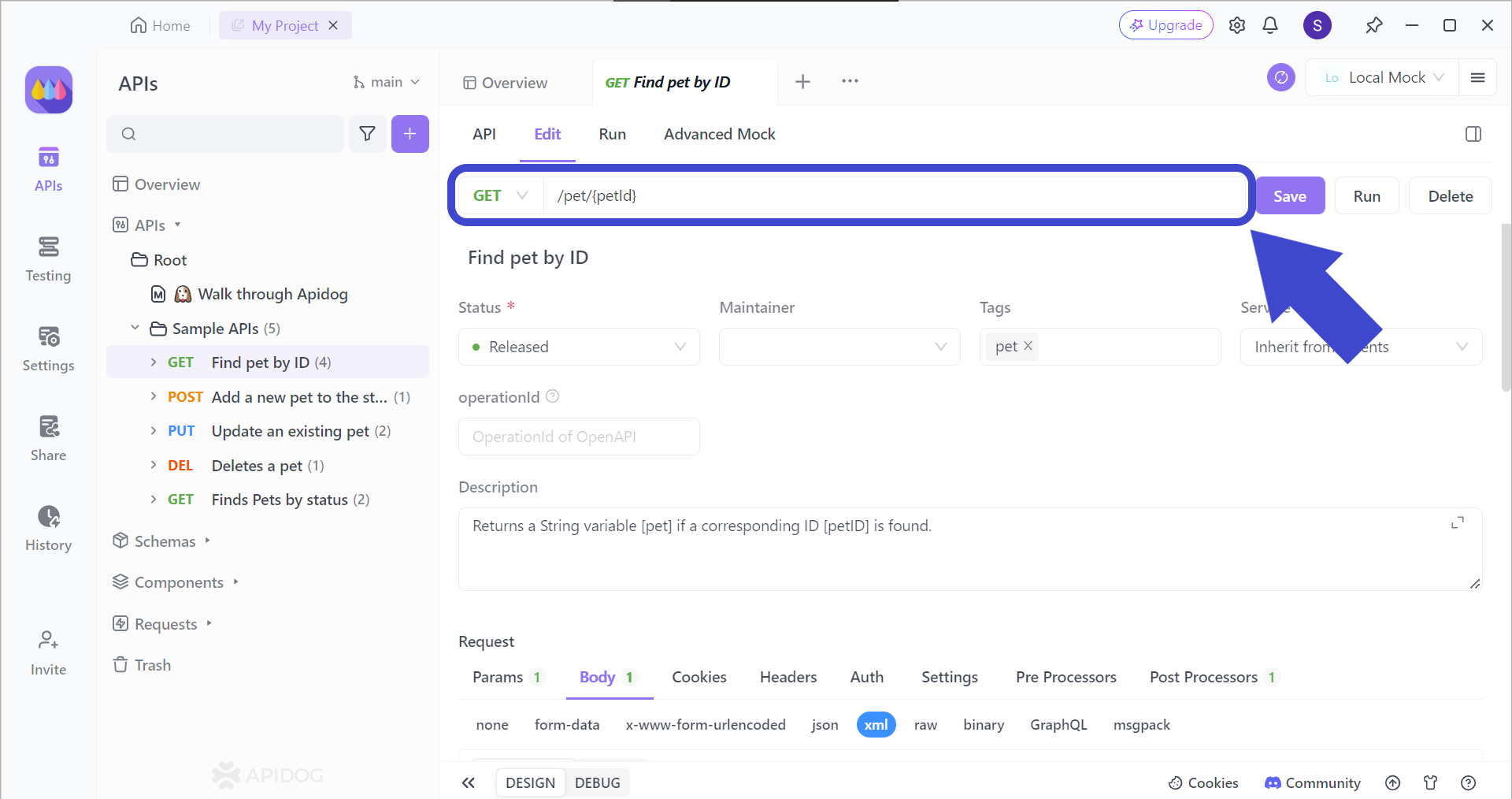
To target the correct API endpoint, you first have to insert the corresponding API endpoint that you want to test. Once you have included the intended API URL, include the parameters that you want to use for the endpoint (if relevant).
In case you are unfamiliar with passing multiple parameters in an API URL, check out this article to find out how you can specifically target a resource inside a rich collection of data!

Conclusion
API authentication and authorization are two critical security measures that work in tandem to safeguard your API. Authentication verifies the identity of users or applications attempting to access your API, acting as the first line of defense. Authorization then determines what level of access these authenticated users or applications have to specific resources or functionalities within the API.
By implementing robust authentication and authorization mechanisms, you can ensure that only authorized users can interact with your API, protecting sensitive data and maintaining the integrity of your system. This not only enhances security but also fosters trust among users who can be confident their information is well-protected.
Ensure that all your APIs are protected with sufficient layers of security. If you need an API tool to bolster your API's protection, you can use Apidog to apply API authentication!