What is an API Key?
An API key is a unique code generated by an API provider and used by developers to authenticate their access to the API's services. An API key acts as a security token that allows a user to access and use an API's resources or data.
When a user or application requests an API, the API checks for the presence of a valid API Key in the request header. The request is processed if the API Key is valid and a response is returned. If the API Key is invalid or missing, the request is rejected.
Why Use API Keys?
API Keys are used for various purposes, such as limiting access to certain resources, tracking usage, and enforcing rate limits. They are commonly used in web applications, mobile apps, and other software that rely on APIs.
One of the key advantages of using API Keys for authentication is that they are relatively easy to implement and manage. Unlike more complex authentication methods like OAuth or OpenID Connect, API Keys can be generated and distributed quickly and revoked or disabled as easily.
API Key Types and API Key Example
Let’s take an overview of the different types of API Keys and the scenarios in which they are most commonly used.
- Standard API Keys: These are the most common type of API Keys, which grant access to the full range of API functionality.
Example:
Google API keys are unique identifiers that allow developers to access and utilize various services and resources provided by Google. These keys serve as authentication credentials, enabling secure communication between applications and Google's APIs (Application Programming Interfaces). Google offers a wide range of APIs for services like Maps, YouTube, Calendar, Gmail, and many others.
The Google Maps API key allows developers to access and use the full range of Google Maps services, including geocoding, routing, and location-based search.
- Limited Scope API Keys: These API Keys restrict access to specific areas of an API, such as certain resources or features.
Example: The Twitter API offers a limited scope API key that restricts access to specific areas of the Twitter API, such as read-only access to user timelines or direct messaging.
- Time-limited API Keys: These API Keys are valid for a limited period, after which they expire and can no longer be used.
Example: The Stripe API allows developers to generate time-limited API keys valid for a set period, after which they expire and can no longer be used. It helps to prevent unauthorized access and improve security.
- Revocable API Keys: These API Keys can be revoked or disabled by the API provider, allowing them to quickly shut down access in case of a security breach or other issue.
Example: The Amazon AWS API offers revocable API keys that can be quickly disabled or revoked by the API provider if there is a security breach or other issue. It helps to ensure the security of the API and protect user data.
By understanding the different types of API Keys and their use cases, developers can choose the most appropriate authentication method for their specific needs. By following best practices for API Key management, such as limiting the scope and rotating keys regularly, developers can ensure the security and reliability of their applications.
When to Use API Keys
API Keys authenticate and authorize access to APIs, allowing developers to securely integrate with third-party services or build their API services. This article will cover the basics of obtaining API Keys.
4 Steps to Get API Keys
The process for obtaining API Keys varies depending on the API provider. Generally, it involves creating an account, registering for the API, and generating a unique API Key.
Here are the general steps:
- Register for an account: Go to the API provider's website and register for an account. It usually requires basic information like your name, email address, and password.
- Create an application: Create an application in the provider's developer dashboard or API settings. It may require additional information, like your application's name and description.
- Generate an API Key: Generate a unique API Key associated with your application. Some providers may allow you to set permissions for the API Key, limiting its access level.
- Store the API Key securely: Store the API Key securely, such as in a password-protected file or a secure database.
By following best practices for API Key management, developers can ensure they have the necessary level of access to the API while limiting the risk of unauthorized access.
How to Work with Apidog and API Keys: Best Practices
APIs have revolutionized how modern applications are built and integrated with third-party services. They allow developers to build powerful applications to access data and services from various sources. However, working with APIs can be complex, and authentication and authorization are critical aspects of API security. This article will explore how to work with Apidog and API Keys, including best practices for managing API Keys.
What is Apidog?
Apidog is a powerful API design platform that allows developers to easily design, document, and test APIs. It provides an intuitive interface for designing APIs that you can easily integrate into your application. also provides authentication and authorization features, including API Keys support.

Best Practices for Working with Apidog and API Keys
When working with Apidog and API keys, following best practices is important to ensure security and efficiency.
Here are some tips for working with Apidog and API keys:
- Use strong and unique API keys: When generating API Keys, it's important to ensure they are unique and not easily guessable. It can help prevent unauthorized access to your API and ensure each application has its credentials.
- Limit access to API keys: Some API providers allow you to set permissions for API Keys, which can limit the level of access an application has. You can ensure that applications can only access the necessary resources by setting permissions.
- Regularly rotate API keys: Regularly rotate API keys helps to mitigate the risk of any potential security breaches. It's recommended to rotate API keys at least once every 90 days.
- Use HTTPS for secure communication: When communicating with your APIs, always use HTTPS to ensure that the data transmitted is secure.
- Implement rate limiting: Implement rate limiting to avoid unnecessary API requests and ensure the API server is not overloaded. It can help improve the performance and stability of your APIs.
- Monitor API key usage: Monitor API key usage to detect any unusual or suspicious activity. It can help you identify and respond to potential security breaches promptly.
- Apidog offers robust API key management features, including the ability to create, manage, and monitor API keys. Make use of these features to streamline your API key management process and improve security. Use Apidog's API key management features:
By following these best practices, you can ensure that your API keys and Apidog usage is secure and efficient. Remember to regularly review and update your API key strategy as needed to stay ahead of potential security threats.
A Step-by-Step Guide to Implementing API Keys with Apidog
API keys are an important aspect of API security, providing authentication and authorization for applications that access APIs. Apidog is a powerful API design platform that allows developers to easily design, document, and test APIs.
In this step-by-step guide, we'll walk you through implementing API keys with Apidog.
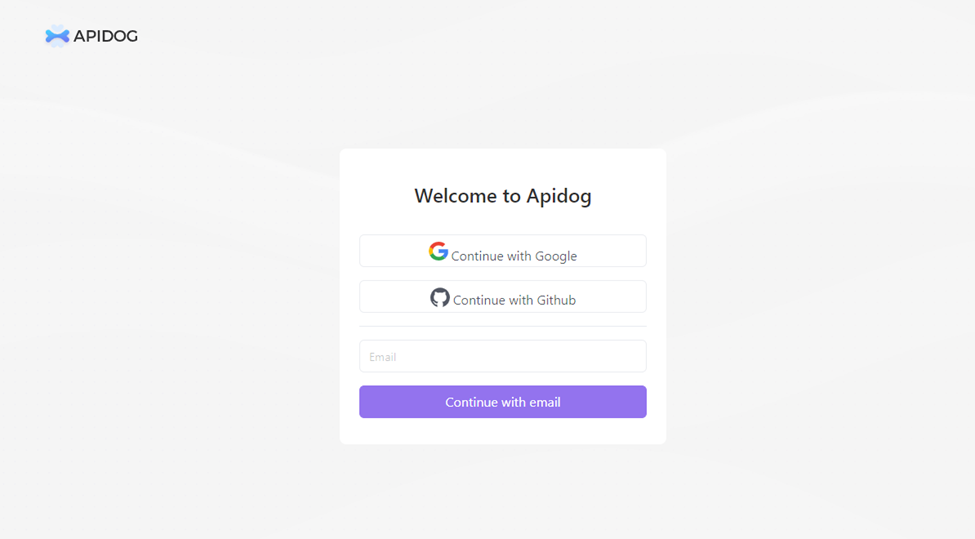
Step 1: Create an Apidog Account
The first step is to create an account with Apidog. You can sign up for a free account. Once you've created an account, you can log in to the Apidog dashboard.
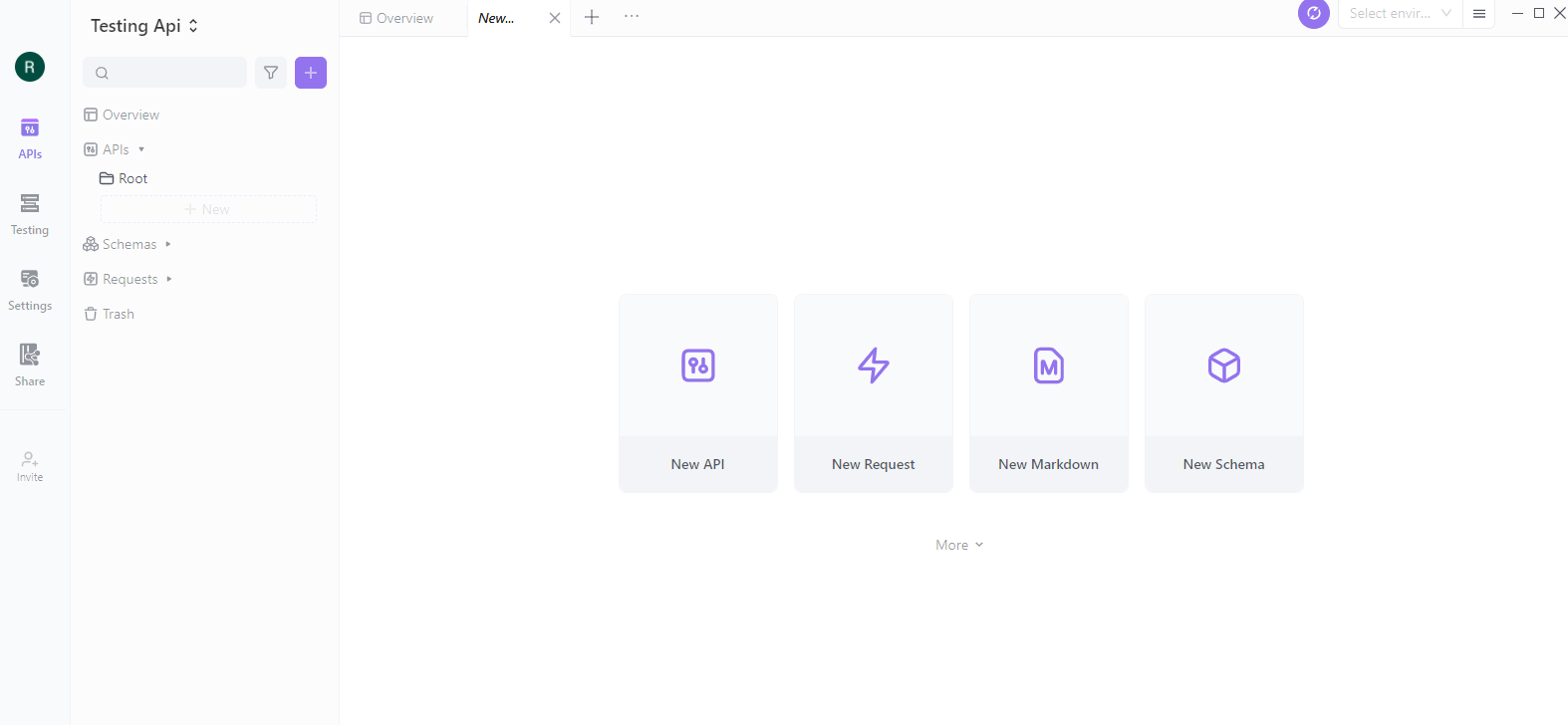
Step 2: Create an API Definition
Click the "Create API" button on the Apidog dashboard to create an API definition. It will open the Apidog editor, allowing you to define your API's structure.
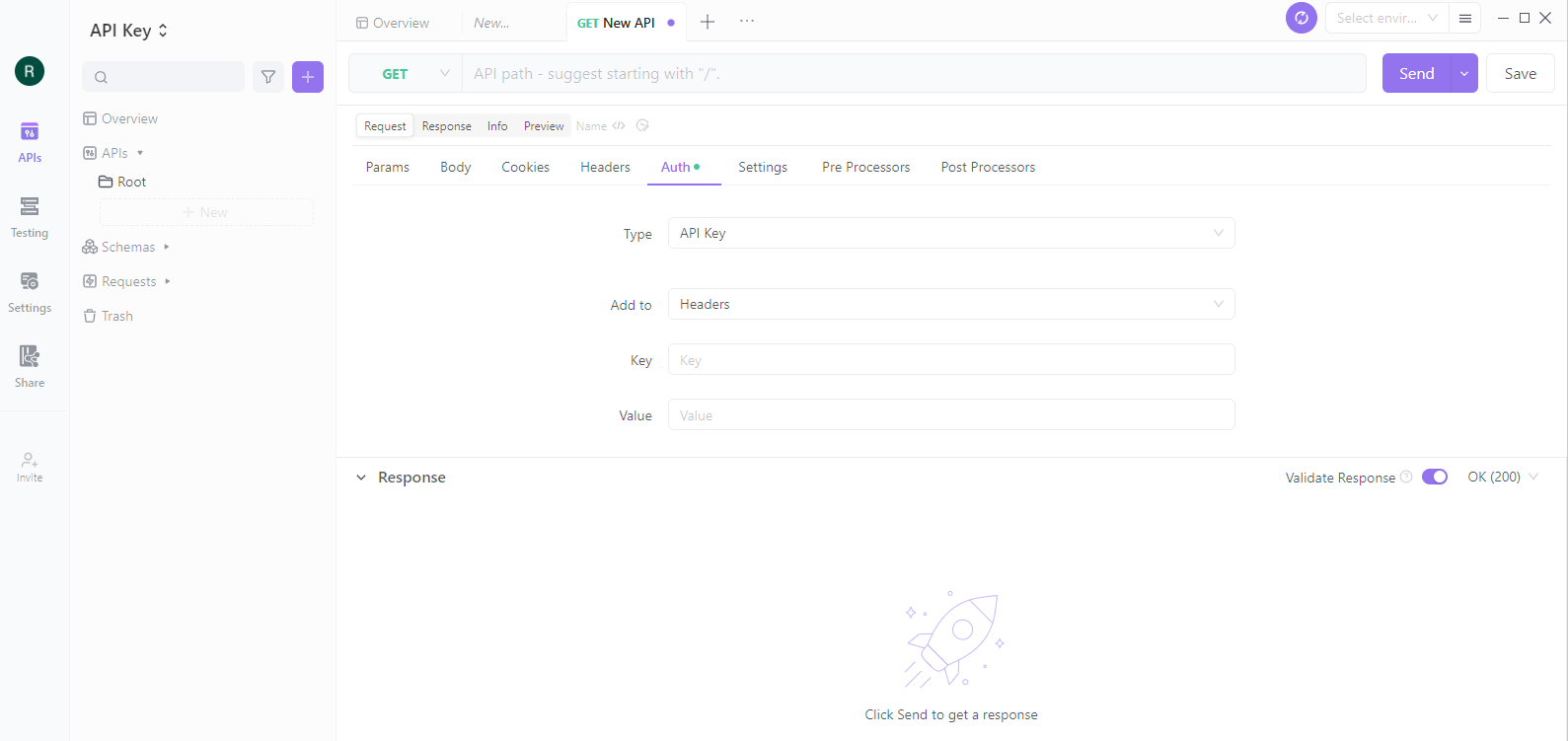
Step 3: Add API Key Authentication
To add API key authentication, click the "Auth" tab in the Apidog editor. Then, select "API Key" from the list of authentication methods. It will enable API key authentication for your API.
Step 4: Generate API Keys
To generate API keys, click the "API Keys" tab in the Apidog editor. Then, click on the "Add API Key" button. It will open a form where you can enter a name for the API key and set its permissions.
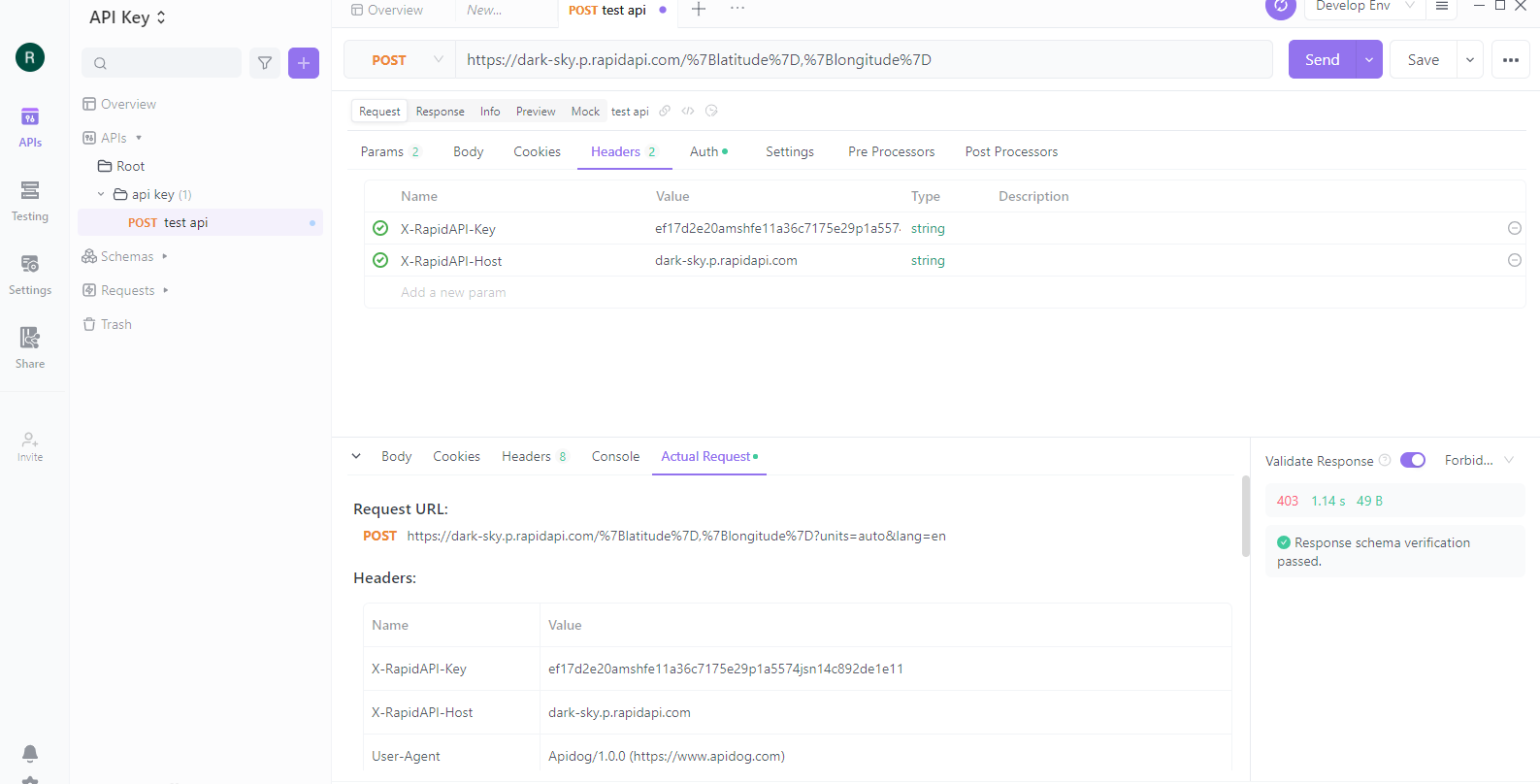
Step 5: Test Your API
Click the "Test" tab in the Apidog editor to test your API. It will open the Apidog testing framework, where you can enter test requests and see the responses from your API.
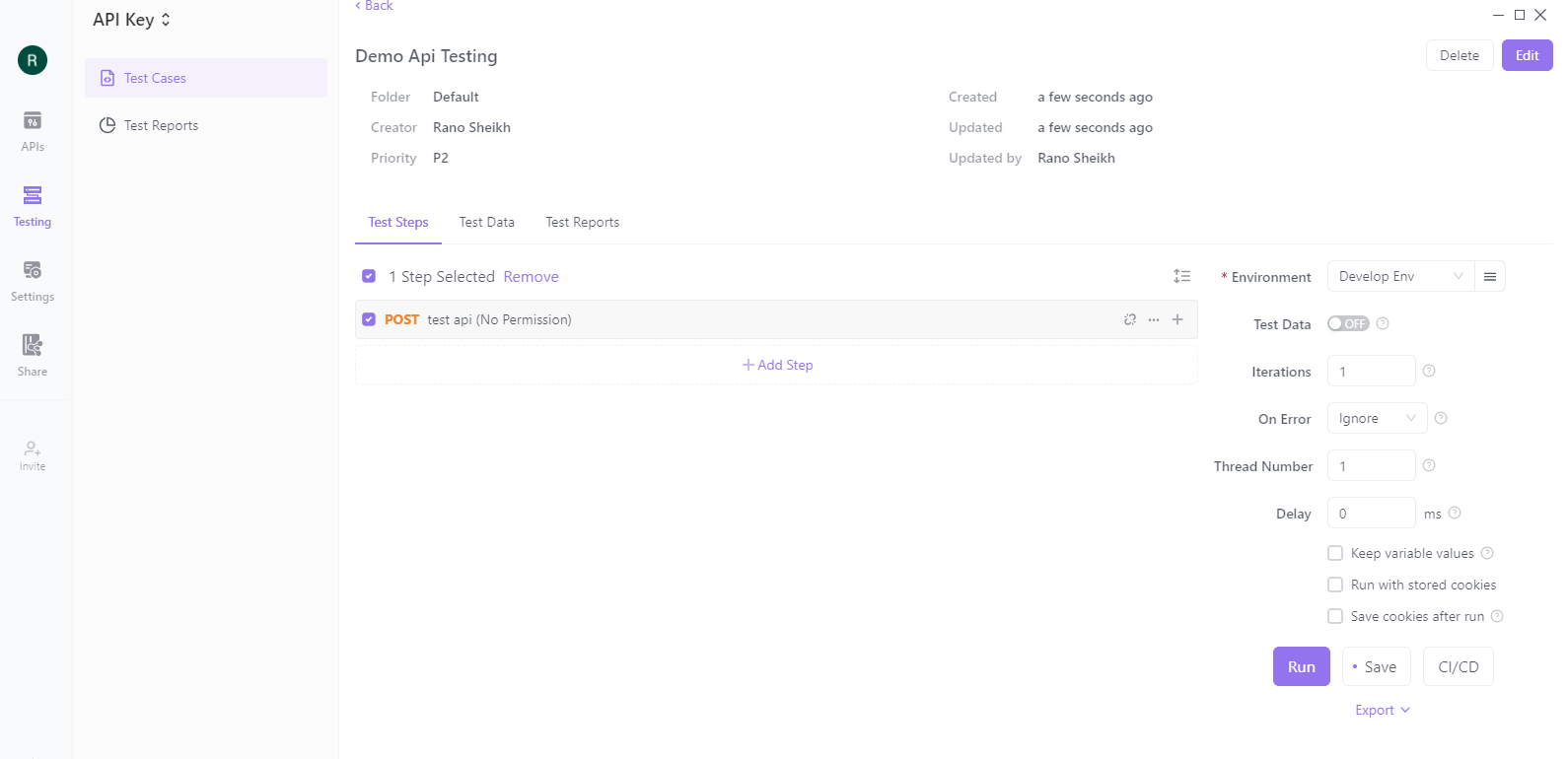
Step 6: Monitor and Manage API Keys
To monitors and manage your API keys, click the "API Keys" tab in the editor. It will show you a list of all your API keys, their permissions, and usage statistics. From here, you can disable or revoke API keys that are no longer needed or have been compromised.
By following these steps, you can ensure that your API is secure and that only authorized applications can access it. With the right tools and practices, working with APIs can be a powerful and efficient way to build modern applications.
Common Pitfalls to Avoid and Troubleshooting Tips
While implementing API keys is straightforward, developers may encounter some common pitfalls. In this section, we'll cover some of these pitfalls and provide troubleshooting tips to help you overcome them.
Forgetting to Enable API Key Authentication
One common pitfall is forgetting to enable API key authentication in the Apidog editor. If you forget to enable API key authentication, your API requests will not be authenticated and will fail.
To avoid this pitfall, make sure that you enable API key authentication in the Apidog editor by selecting "API Key" from the list of authentication methods.
Generating Insecure API Keys
Another common pitfall is generating insecure API keys. Insecure API keys can be easily compromised, allowing unauthorized access to your API.
To avoid this pitfall, make sure that you generate secure API keys that are difficult to guess. Use a permutation of letters, numbers, and symbols, and minimize using easily guessable information such as your name or company name.
Exposing API Keys in Source Code
Another common pitfall is exposing API keys in source code. If you include your API keys in the source code, unauthorized users can easily access them.
To avoid this pitfall, store your API keys securely and do not expose them in the source code. One way to do this is to use environment variables to store your API keys and access them in your application code.
Overlooking API Key Management
A common pitfall is overlooking API key management. If you manage your API keys properly, they can be updated and protected, leading to unauthorized access to your API.
To avoid this pitfall, ensure you have a process for managing your API keys. It includes regularly reviewing and revoking outdated or compromised API keys.
Troubleshooting Tips:
If you encounter issues while implementing API keys with Apidog, here are some troubleshooting tips:
- Double-check your API key settings in the Apidog editor to ensure they are correctly configured.
- Check that your API requests include the correct "X-Api-Key" header with the value of your API key.
- Use Apidog's testing framework to debug your API and identify any issues with your API key authentication.
- Review API key usage statistics to identify any unusual activity or errors.
By avoiding these common pitfalls and following these troubleshooting tips, you can ensure your API keys are secure and properly configured with Apidog. Proper API key management is crucial to maintaining the security and integrity of your APIs.