API (Application Programming Interface) security is vital for an operational API ready for public use. With APIs mainly used as intermediaries facilitating communication between different applications, they should pose sufficient security to ensure that the data exchanged between the two parties remains confidential.
Apidog is a suitable API tool that allows developers to implement OAuth 2.0 and SAML authorization frameworks, reassuring their consumers that their APIs are ready for implementation.
To start using Apidog today, click the button below to begin!

OAuth 2.0 and SAML are two dominant authorization frameworks that developers can use. This article will therefore delve into the details of both OAuth 2.0 and SAML. Before going into the minute descriptions, there will be a simple recap on OAuth.20 and SAML.

What is OAuth 2.0?
OAuth 2.0 is an industry-standard authorization framework specifically designed for application programming interfaces (APIs). It facilitates a secure method for resource owners (typically users) to grant controlled access to their information on a service, to third-party applications (clients), without ever revealing their actual credentials.
Comprehensive Breakdown of OAuth 2.0
OAuth 2.0, the industry-standard authorization framework for APIs, revolves around secure delegation of access. Let's delve into the intricacies of this framework, exploring its components, workflows, and security considerations.
OAuth 2.0 Key Roles
- Resource Owner (RO): The entity (usually a user) who controls the resources being accessed. This could be their photos, emails, or other data stored on a service.
- Resource Server (RS): The server that stores the protected resources and verifies access tokens presented by clients.
- Client (Third-Party Application): The application requesting access to the resources on behalf of the RO. This could be a photo editing app, a fitness tracker, or any service that needs user data.
- Authorization Server (AS): The server responsible for issuing access tokens after verifying the RO's authorization. It acts as a trusted intermediary between the RO, Client, and RS.
OAuth 2.0 Authorization Flows
OAuth 2.0 defines several authorization flows tailored to different application types and security needs. Here are the prominent ones:
- Authorization Code Grant: This flow is commonly used for web applications. The client redirects the RO to the AS, where they grant or deny access. If granted, the AS issues an authorization code to the client. The client then exchanges this code with the AS for an access token. This two-step process enhances security by keeping the authorization code short-lived and confidential.
- Implicit Grant: This flow is suitable for public client applications (e.g., mobile apps with limited secret storage). The AS directly returns an access token to the client upon RO authorization. While convenient, this flow carries security risks due to the exposure of access tokens within the client application.
- Resource Owner Password Grant: This flow is typically used in server-side applications where the client has secure storage for RO credentials. The RO provides their credentials directly to the client, who then uses them to obtain an access token from the AS. Due to the exposure of credentials, this flow should be used cautiously.
- Client Credentials Grant: This flow is used for machine-to-machine authorization, where clients are pre-configured with credentials. The client uses these credentials to directly obtain an access token from the AS for accessing specific resources.
These are just some of the common flows, and the choice depends on factors like application type, security requirements, and user experience considerations.
OAuth 2.0 Tokens
- Access Token: A short-lived credential issued by the AS to the client after successful authorization. It grants the client permission to access specific resources on the RS on behalf of the RO. Access tokens are often designed to be opaque and not contain sensitive information.
- Refresh Token (Optional): A long-lived credential (often with stricter security measures) used to obtain new access tokens without requiring further RO interaction. This is useful for long-running applications that need to maintain access.
OAuth 2.0 Security Considerations
- Limited Scope: Access tokens are typically granted with a specific scope, restricting the resources the client can access.
- Short-lived Access Tokens: Access tokens have a limited lifespan, minimizing the window of vulnerability if compromised.
- Refresh Token Security: Refresh tokens require careful handling due to their long-lived nature. Secure storage and proper invalidation mechanisms are essential.
- HTTPS communication: All communication between parties involved in the OAuth flow should be encrypted using HTTPS to prevent eavesdropping and man-in-the-middle attacks.
OAuth 2.0 Benefits
- Improved Security: Eliminates the need for clients to store RO credentials, reducing the risk of data breaches.
- Granular Access Control: Provides fine-grained control over what resources a client can access.
- Standardized Framework: Simplifies application development by offering a well-defined authorization mechanism.
- Flexibility: Supports various application types through different authorization flows.
What is SAML?
The Security Assertion Markup Language (SAML) is an XML-based standard for exchanging authentication and authorization data between security domains. It facilitates a framework for secure single sign-on (SSO) across web applications, enabling users to authenticate once and access multiple resources without re-entering credentials.
Comprehensive Breakdown of SAML
Security Assertion Markup Language (SAML) plays a crucial role in web single sign-on (SSO) and access control. This in-depth analysis delves into the core concepts, functionalities, security aspects, and practical considerations of SAML.
SAML Core Functionality
SAML operates on the foundation of trust established between two entities:
- Identity Provider (IdP): Acts as a trusted authentication authority. It verifies user credentials and issues assertions about a user's identity attributes (e.g., name, email address, group memberships). Imagine this as a company's secure login portal.
- Service Provider (SP): Represents an application or web resource that relies on the IdP for user authentication and authorization decisions. Think of this as a corporate expense management application that needs to verify a user's identity before granting access.
SAML Authentication Flow
The SAML authentication flow involves a series of secure exchanges between the user, IdP, and SP:
- User Initiates Access: A user attempts to access a protected resource on the SP (e.g., trying to access the expense management application).
- Redirection to IdP: The SP, unable to authenticate the user itself, redirects the user to the IdP for authentication.
- Authentication at IdP: The user interacts with the IdP's login page, providing credentials for verification.
- SAML Assertion Creation: Upon successful authentication, the IdP creates a SAML assertion. This XML document encapsulates information about the user's verified identity attributes.
- Assertion Delivery: The IdP securely transmits the SAML assertion back to the SP.
- Assertion Validation: The SP scrutinizes the assertion's authenticity and integrity using digital signatures. This ensures the assertion hasn't been tampered with and originates from a trusted IdP.
- Access Granted (or Denied): If the assertion is valid, the SP extracts relevant user attributes from it and grants access to the requested resource. If invalid, access is denied.
SAML Key Components
- SAML Assertions: The heart of SAML, these XML documents encapsulate user identity information and other authorization-related data.
- Metadata: These XML files act as blueprints for communication. The IdP and SP exchange metadata to understand each other's capabilities and configuration details (e.g., supported protocols, and security certificates).
- Protocols: A set of defined protocols dictates the message formats and communication flows for authentication and authorization. Common examples include SAML SOAP Binding (for SOAP messaging) and SAML HTTP Binding (for web browser communication).
SAML Security Considerations
- Digital Signatures: SAML assertions are digitally signed by the IdP, guaranteeing their authenticity and preventing unauthorized modifications.
- Secure Communication: Communication between entities (user, IdP, SP) should be encrypted using HTTPS to safeguard data in transit.
- Attribute Release Control: The IdP maintains control over which user attributes are released in the SAML assertion. This adheres to the principle of least privilege, minimizing the amount of user data exposed.
SAML Benefits
- Centralized Authentication: Simplifies user experience by enabling single sign-on across multiple applications that leverage the same IdP. Users only need to authenticate once to access various resources.
- Enhanced Security: Shifts the responsibility of user authentication to a potentially more secure and centralized IdP, potentially improving overall security posture.
- Scalability: Supports a growing number of SPs within a single IdP infrastructure, facilitating secure access management for a larger user base.
- Standardization: Offers a well-defined framework for interoperable SSO between different vendors' IdP and SP solutions. This promotes flexibility and simplifies integration.
Tabulated Differences Between OAuth 2.0 VS. SAML
| Feature | OAuth 2.0 | SAML |
|---|---|---|
| Primary Function | API Access Control | Web SSO and Access Control |
| Authorization Protocol | Yes | No (uses assertions for authentication and authorization) |
| Roles | Resource owner, resource server, client (application), and authorization server | Identity Provider (IdP) and Service Provider (SP) |
| Token Used | Access Token (short-lived, optional refresh token) | SAML Assertion (signed XML document) |
| Security Focus | Eliminates sharing credentials, and has limited scope access tokens. | Digital signatures and secure communication. |
| Benefits | Improved security, granular access control, and standardized framework | Centralized authentication, improved secruity, scalability, and standardization. |
| Workflow | Varies depending on authorziation flow (like Authorization Code Grant). | User -> SP -> IdP -> SP (with SAML Assertion) |
| Suitable for: | Protecting APIs, granting Access to specific resources. | Centrailzied authentication accross multiple applications. |
Apidog - Implement Your Favorite Authentication Framework
API tools are integral in proper API development. A perfect API tool for developers to have control over the entire API lifecycle would be Apidog.


Implementing OAuth 2.0 with Apidog
Let's take a look at how we can apply the OAuth 2.0 authentication on the newly made request.
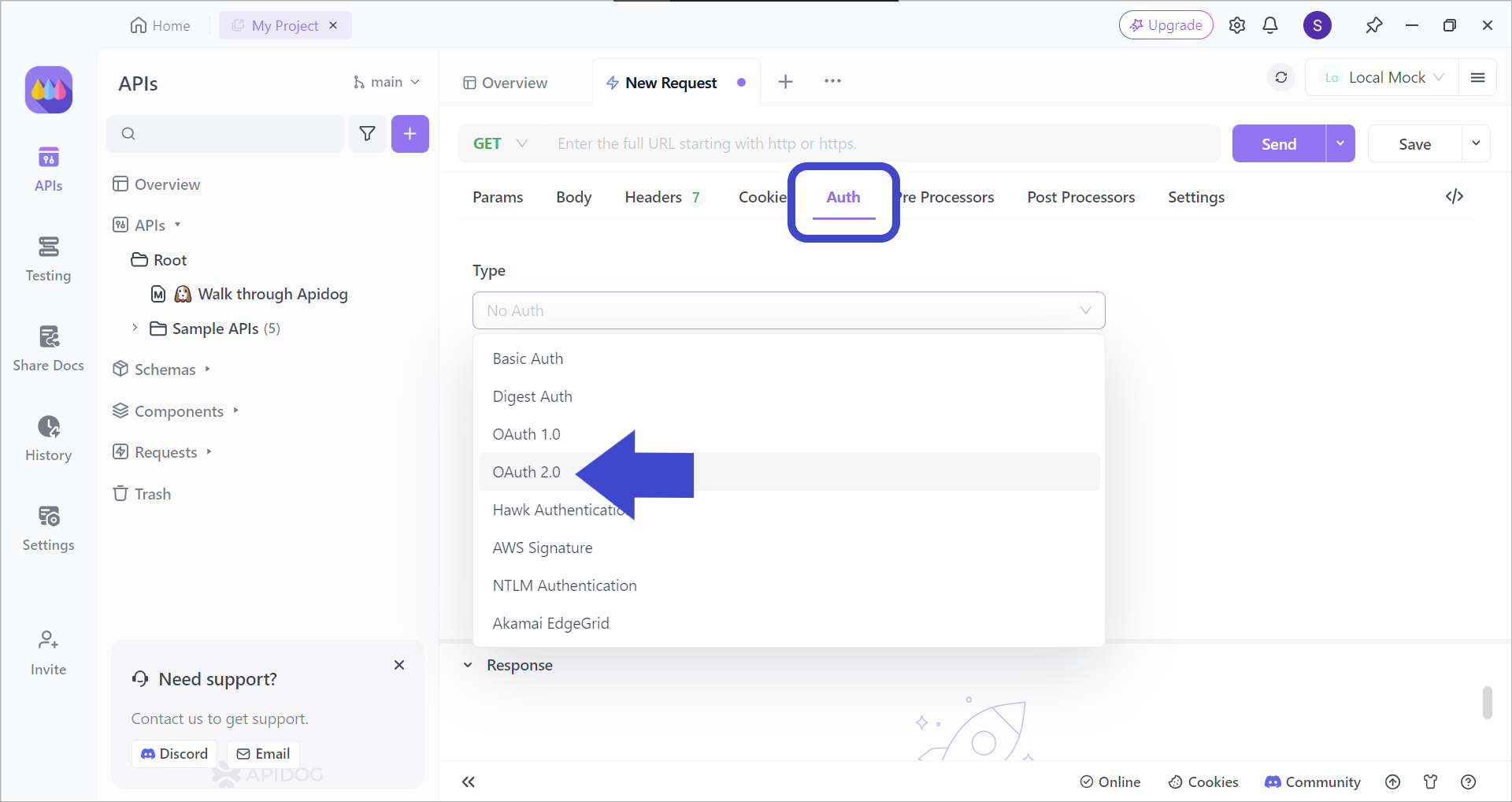
After creating a new request, pick the OAuth 2.0 authentication type, as seen in the image above.
Testing API Endpoints Using Apidog
After every modification made during the API development stage, we need to ensure that the API still runs as intended. With Apidog, you can test each API's endpoint.
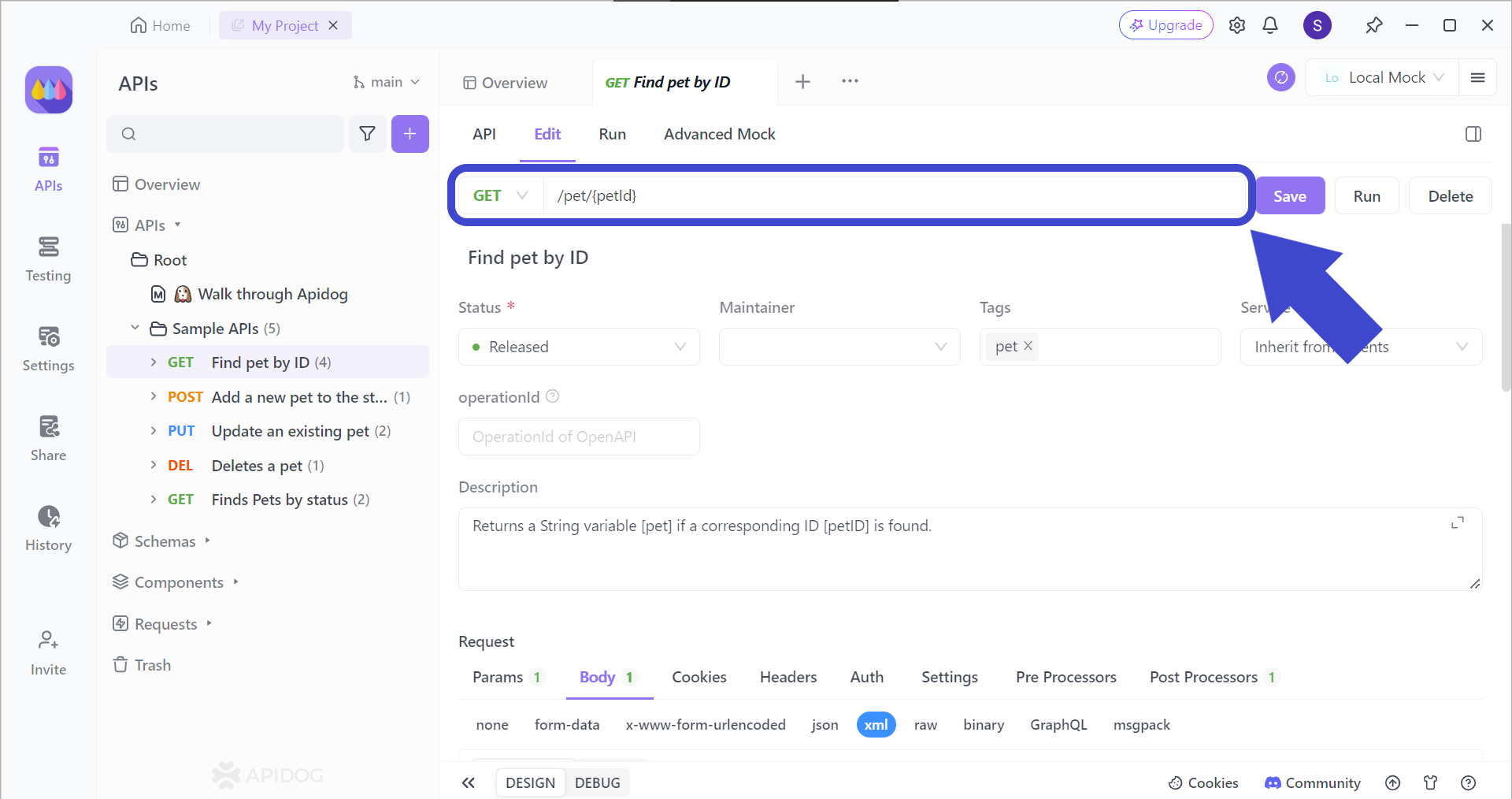
To target the correct API endpoint, you first have to insert the corresponding API endpoint that you want to test. Once you have included the intended API URL, include the parameters that you want to use for the endpoint (if relevant).
If you are still not quite confident about how to test an API endpoint, give this article a read!

Conclusion
Both OAuth 2.0 and SAML play vital roles. OAuth 2.0 shines through its ability to meticulously control access to APIs. By eliminating the need for applications to store user credentials and offering fine-grained control over what resources can be accessed, OAuth 2.0 significantly reduces the attack surface for API security vulnerabilities.
While SAML excels in simplifying user experience through SSO for web applications, it doesn't directly address API access control. Therefore, for securing APIs and ensuring granular access control, OAuth 2.0 stands as the undisputed champion. Its focus on API security and standardized approach makes it the ideal choice for protecting valuable resources within modern application ecosystems.




